Simple Application Security Integrations for DevOps Threat Researcher
Serverless Security
Explore why application security matters and how you can integrate it into your build process without added stress or interruption.
Time is of the essence when building in the cloud, as organizations need DevOps teams to develop and deploy quickly to keep up with business and consumer needs. You may already be building like the wind, but application security keeps standing in the way. You know you need to improve it—but you’re looking for a way to do so without interrupting your workflow.
One way is to use runtime application self-protection, a security technology that kicks in when the application starts to run in order to detect and block threats in real-time. Trend Micro Cloud One™ – Application Security is designed to work in environments where traditional security cannot be deployed, like serverless and containerized applications, due to absence of an underlying host. By hooking into your framework at key points, it can detect and exploit attempts to immediately prevent hacks and identify vulnerabilities such as remote command execution, illegal file access, malicious file uploads, and more.
Advantages of Using Application Security
- Easy and quick to deploy.
- Deploys across just about any architecture and network topology.
- Runs fast since all protection takes place inside the application directly, eliminating network latency
- More reliable high-level alerts—only concerned with exploitable vulnerabilities specific to your application
- Supports secure sockets layer (SSL) tunneling and termination.
- Protects the web application from most of the OWASP Top 10 Vulnerabilities like standard query language (SQL) Injections, sensitive data exposure, XML External Entities (XXE), and more.
- Protects the application from third-party open source software vulnerabilities, specifically the unknown ones that fly under the radar of common open source vulnerability scanners.
Protection Policies Provided in Application Security
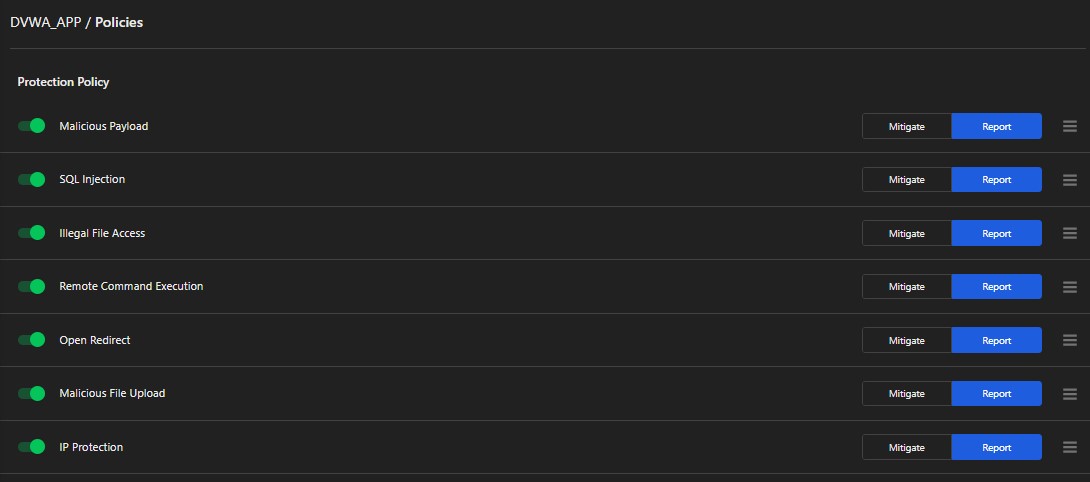
As you see here, there are different protection policies provided for all the application vulnerabilities possible. You can either choose to just detect the attacks (option: Report) or prevent the attack (option: Mitigate). Let’s walk through different vulnerabilities that policies can detect:
1. Malicious Payload
This is an attack component like ransomware or worms. Malicious payloads are dangerous because they remain inactive until activated, essentially camouflaging amongst your infrastructure until signaled to attack.
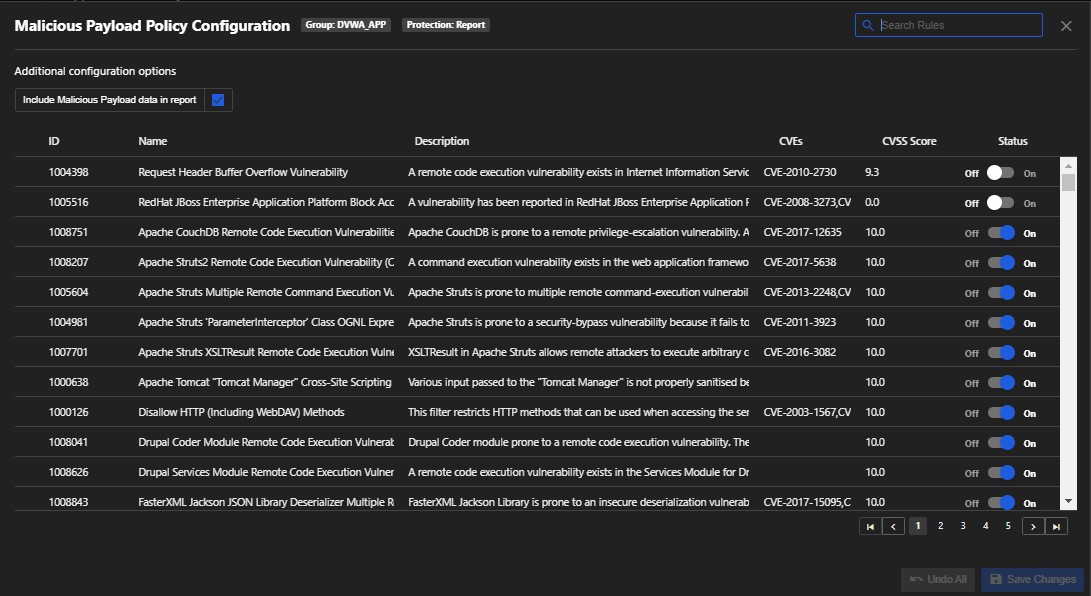
You can select which Trend Micro Intrusion Prevention System (IPS) rule you want to apply here in this policy.
2. SQL Injection
This policy finds any SQL Injections lurking in your application. An SQL Injection is one of the most common web hacking techniques; it places malicious code in SQL statements (usernames and user IDs).
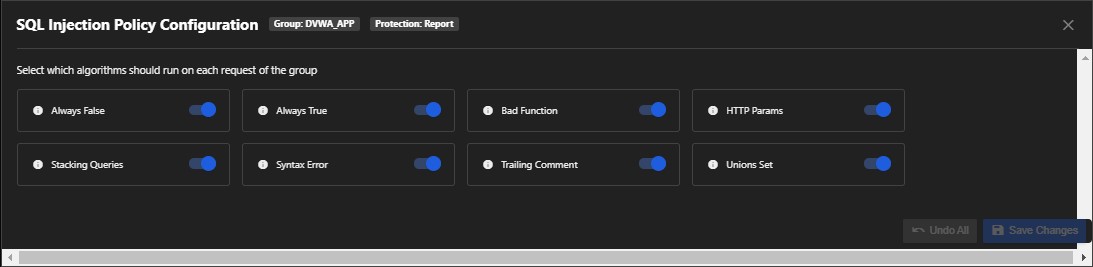
You can also choose which detection algorithm you want active to detect SQL Injections.
3. Illegal File Access
This policy detects any file access (Read and Write) that is restricted based on the default rules or customized rules that you have set up.
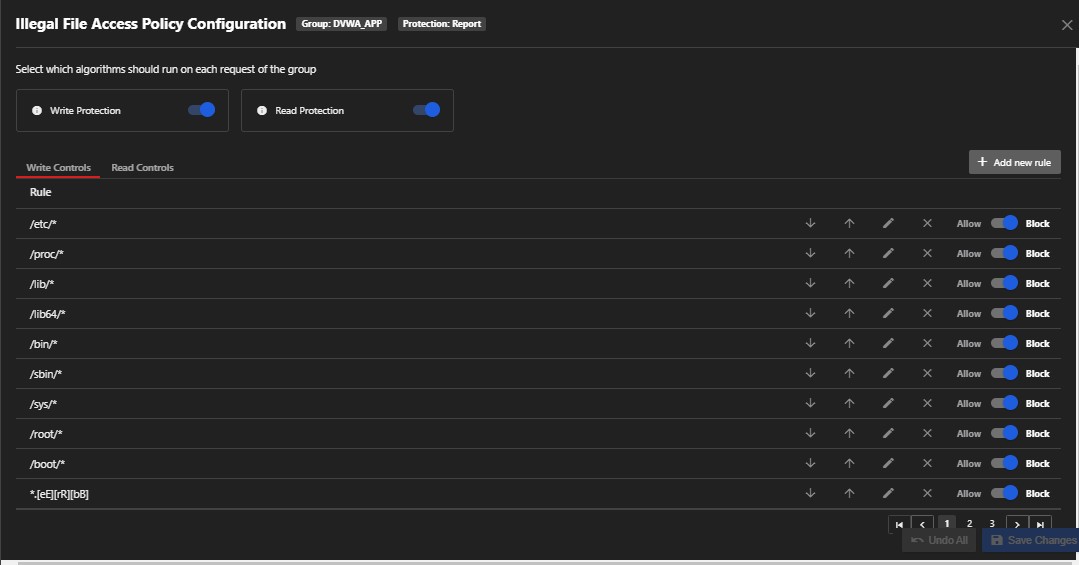
You can write your own rules or enable/disable existing rules from here.
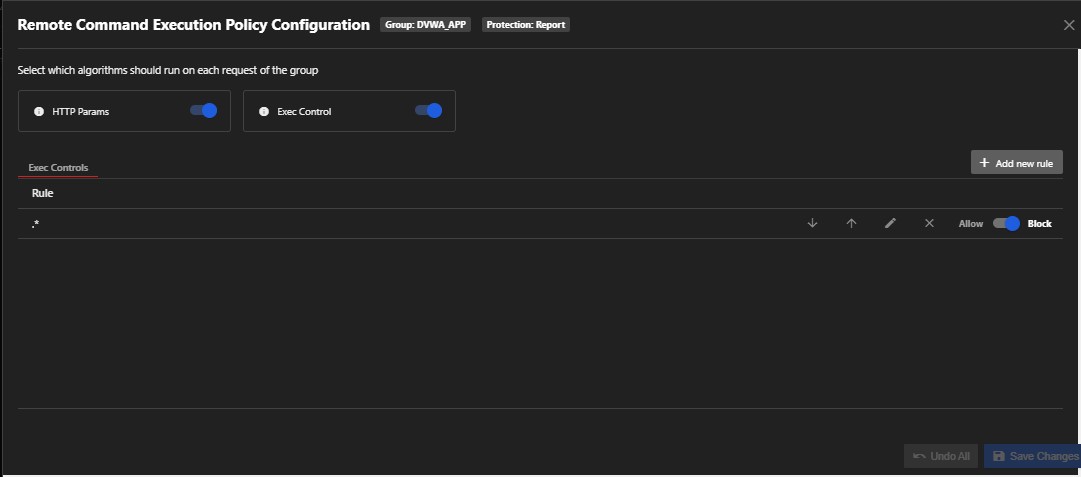
4. Remote Command Execution
This is when an attacker runs any malicious code of their choosing with system-level privileges on any vulnerable server. Once the server has been exploited, the attacker can gain access to all private data and information on that server. You can detect this dangerous threat by applying the detection algorithm with customized rules.
5. Open Redirect
An open redirect is when attackers change the URL accessed by the customer to redirect to their web server. This is often used in phishing emails, where customers are prompted to click a link with a supposedly trustworthy name that in actuality leads them to a malicious website.
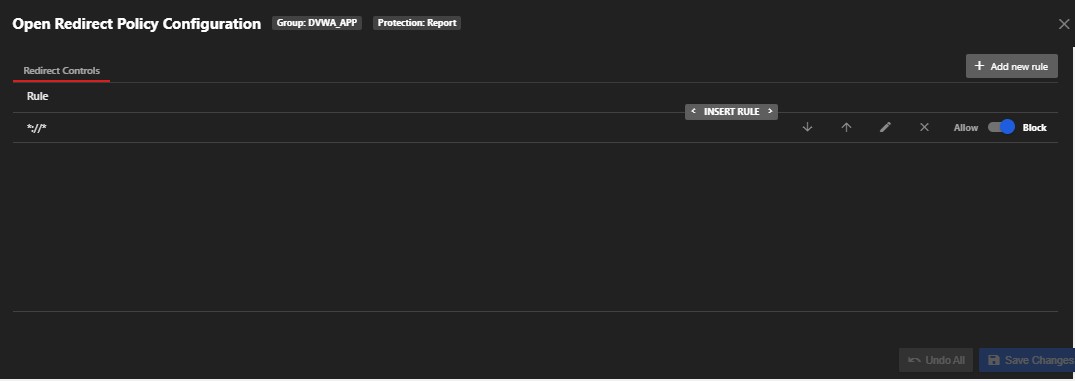
You can write your custom rules or enable/disable existing rules from here.
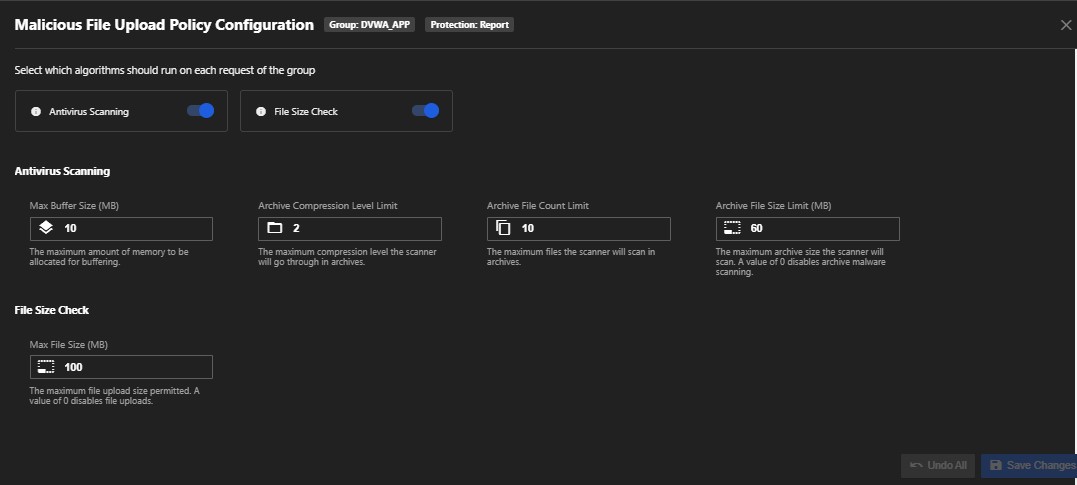
6. Malicious File Upload
When invalidated files are uploaded on vulnerable servers, they can execute malicious script on the server-side to either upload phishing pages that extract users’ data, grant access to other illegal software, or gain control of the server to scrape valuable data. This policy scans for any malicious files potentially uploaded to your application, checks the file size, and blocks it based on the threshold provided by you.
7. IP Protection
An IP address is essentially your internet address—the exact location where you receive emails, browse the web, etc. When websites have access to your IP address, it can potentially be sold to third parties without your consent and be used by malicious actors to spy on you. Protecting your IP address by utilizing IP and subnet filtering or whitelisting is essential keep cybercriminals from gaining access to valuable data.
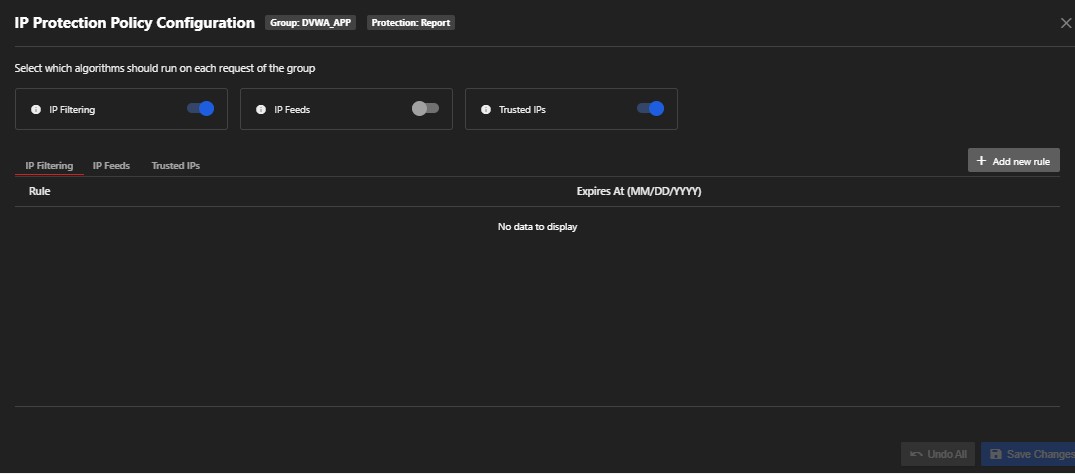
You can add new rules here, specifying a single IP or a subnet to filter or whitelist.
On Host Web Application Used for Attack Demo
Okay, now that we’ve covered the basics of Application Security, let’s take a look at how it works in real-time. For this demo, we are using a Damn Vulnerable Web Application (DVWA). This is a PHP/MySQL web application that is, you guessed it, damn vulnerable. DVWA provides security professionals a chance to test their skills and tools in a legal environment. It also helps web developers better understanding the process of securing web applications in a dummy, no-pressure environment. Want to try it for yourself? Click here.
For our demo purpose we have deployed DVWA on host. Please note that this application is vulnerable to several kinds of attacks, so we advise you don’t deploy it to any public servers or production environments.
Let’s start with setting up Application Security with DVWA:
Application Security Integration with DVWA
Since DVWA is based on PHP, we install a PHP-based Application Security agent on the Amazon Elastic Compute Cloud (EC2) instance we want to manage.
1. Stop the httpd/apache2 service.
2. Copy the downloaded trend_app_protect-*.so into the PHP extension directory.
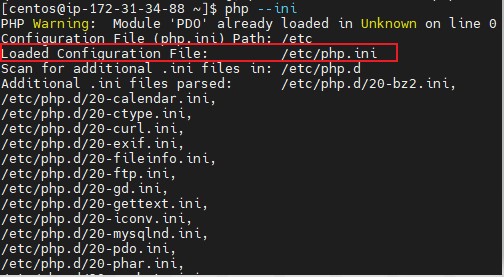
3. Edit the php.ini file currently being used by PHP. To find the file path of php.ini being used, run the command php –ini and look for Loaded Configuration File.
4. Populate the php.ini file with the extension name and the Application Key and Secret (which you can find from the Application Security console). Be careful about any whitespaces that maybe added while copying and pasting the key and secret from the Application console.
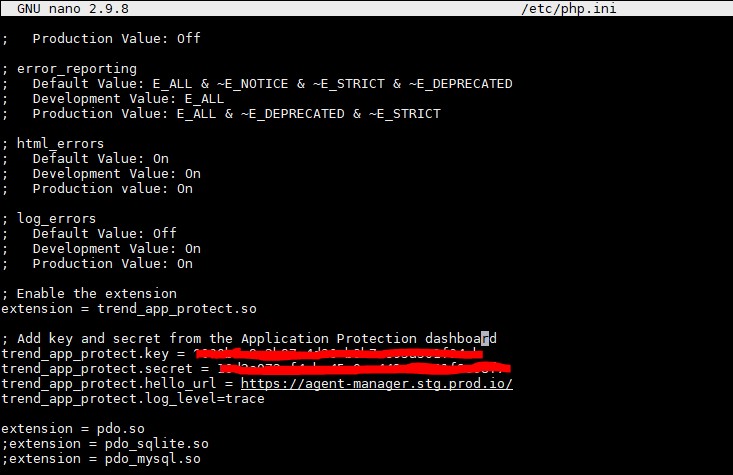
5. After step 4 is completed, you might also need to add trend_app_protect.hello_url in the php.ini file, as shown in the above image. After doing so, save the file and restart the httpd/apache2 service, along with the PHP-FPM service.
6. Send a simple HTTP request or, just access the website from your browser for the hosted DVWA application to activate the agent.
7. Now, you should see triggers on the Application Security console. The status should turn green from grey.
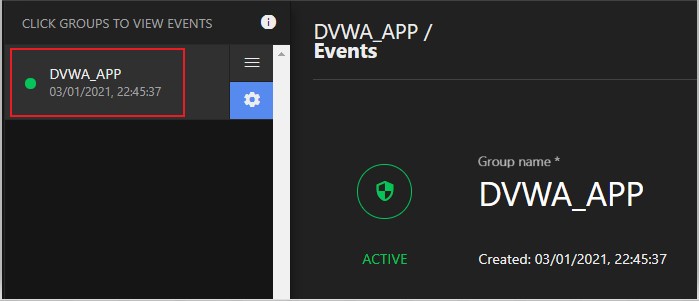
8. When you trigger any module from the Application Security console, you will get the status as Attacks Ongoing and the color changes to red.
Proof of Concept Demo
Now that Application Security is up and running on the DVWA, we’ll take a look at what types of attacks it will find. For the purpose of this demo, Application Security is kept in detect mode. You can also opt to keep it in block mode, which will block all the attacks.
1. VULNERABILITY: OS Command Injection
Attack:
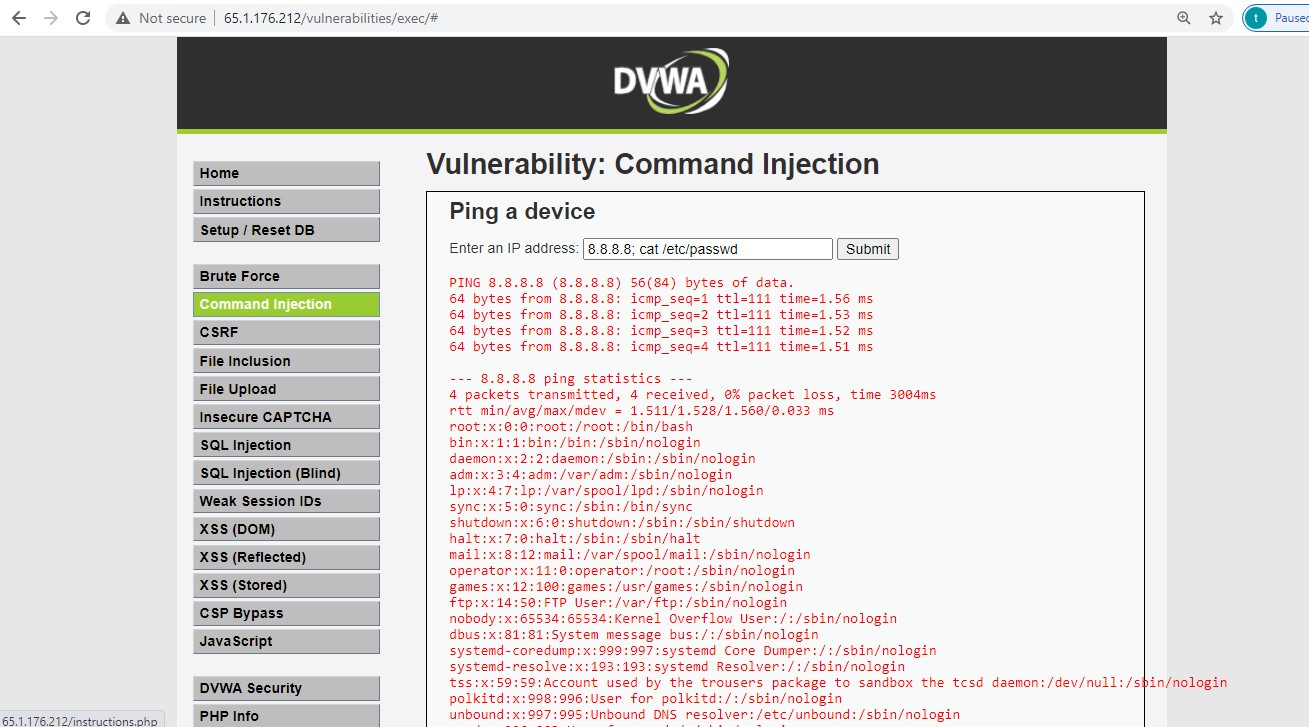
As you can see with the payload 8.8.8.8; cat /etc/passwd, we are able to exfiltrate contents of the passwd file that stored users’ confidential info.
Detections: Yes
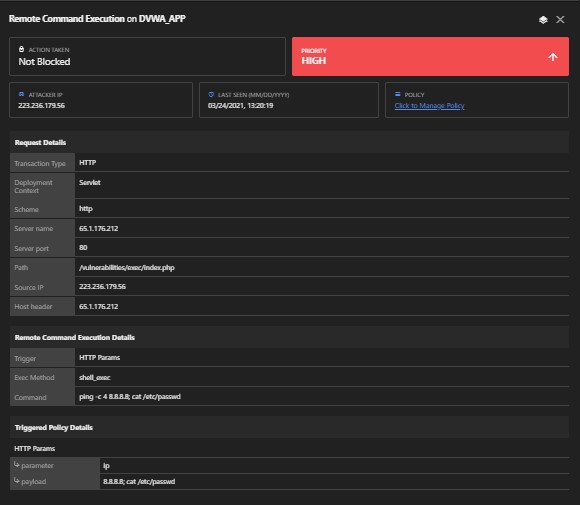
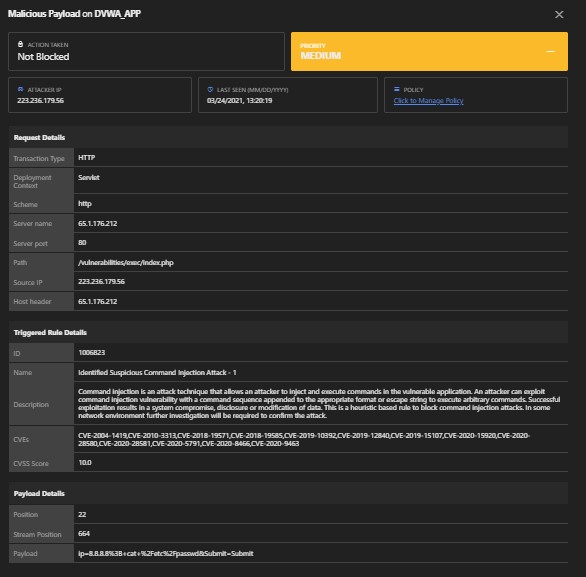
Module: Remote Command Execution, Malicious Payload
2. VULNERABILITY: File Inclusion
Attack:
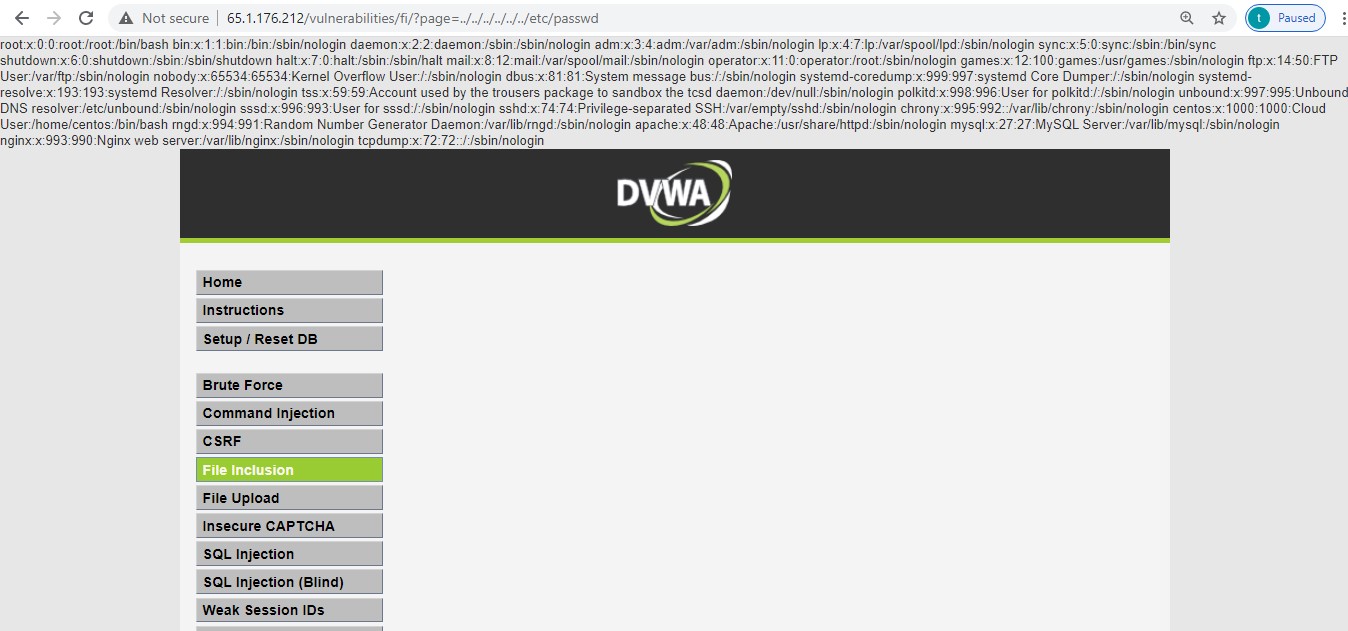
We are exploiting the vulnerability by incorporating directory traversal payload ../../../../../../etc/passwd to exfiltrate contents of the password file for user information.
Detections: Yes
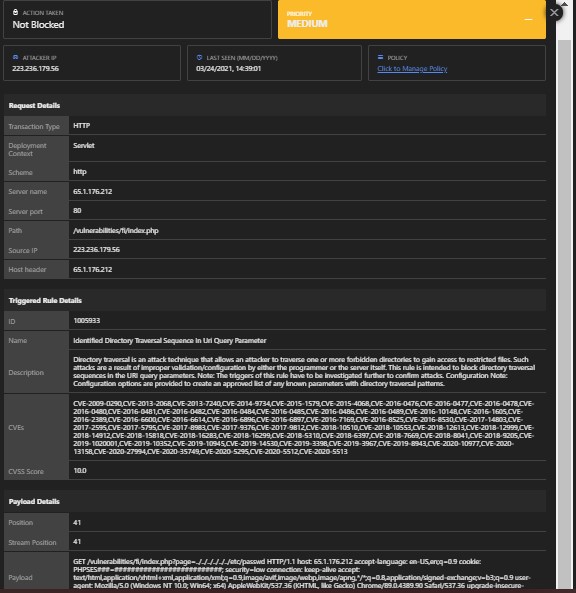
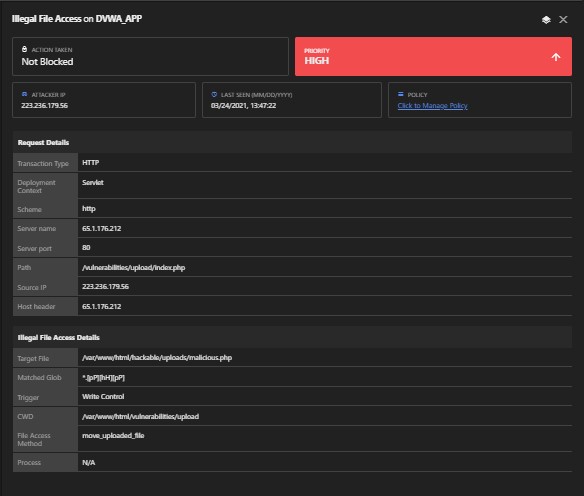
Module: Malicious Payload, Illegal File Access
3. VULNERABILITY: Malicious File Upload
Attack:
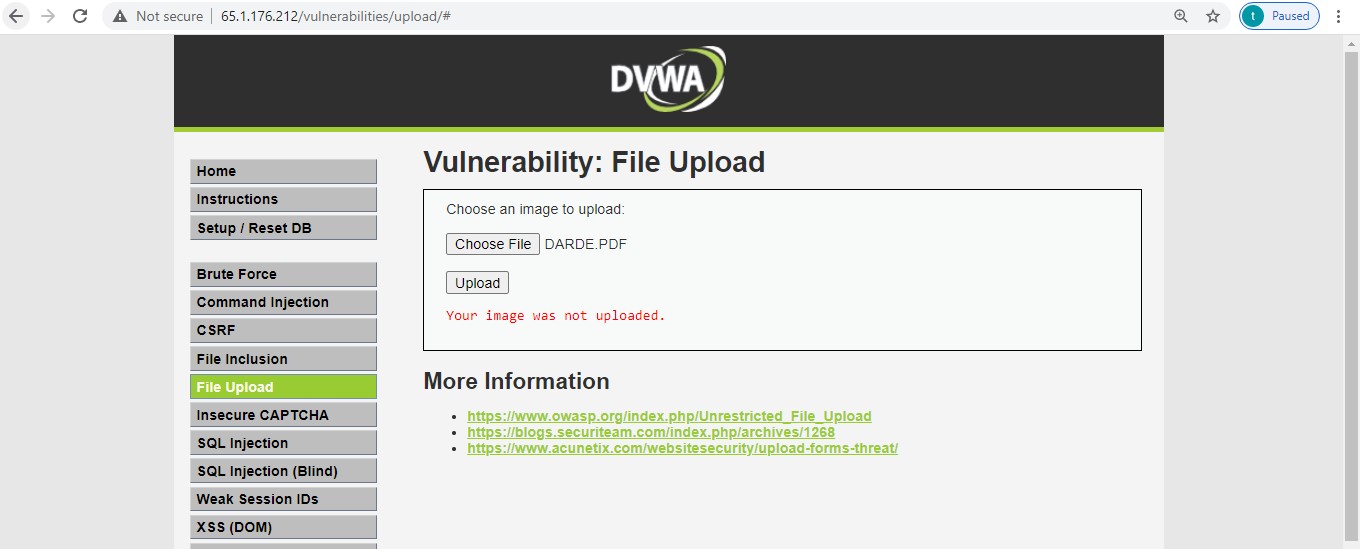
We are exploiting the vulnerability by uploading a malicious file in the application to perform further attacks.
Detections: Yes
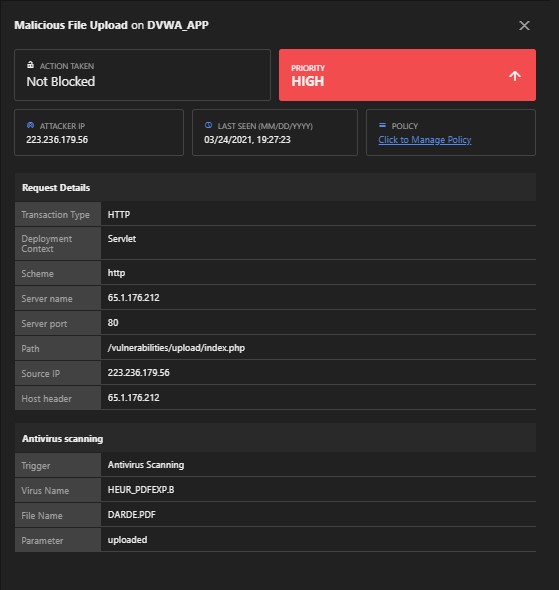
Module: Malicious File Upload
4. VULNERABILITY: SQL Injection
Attack:
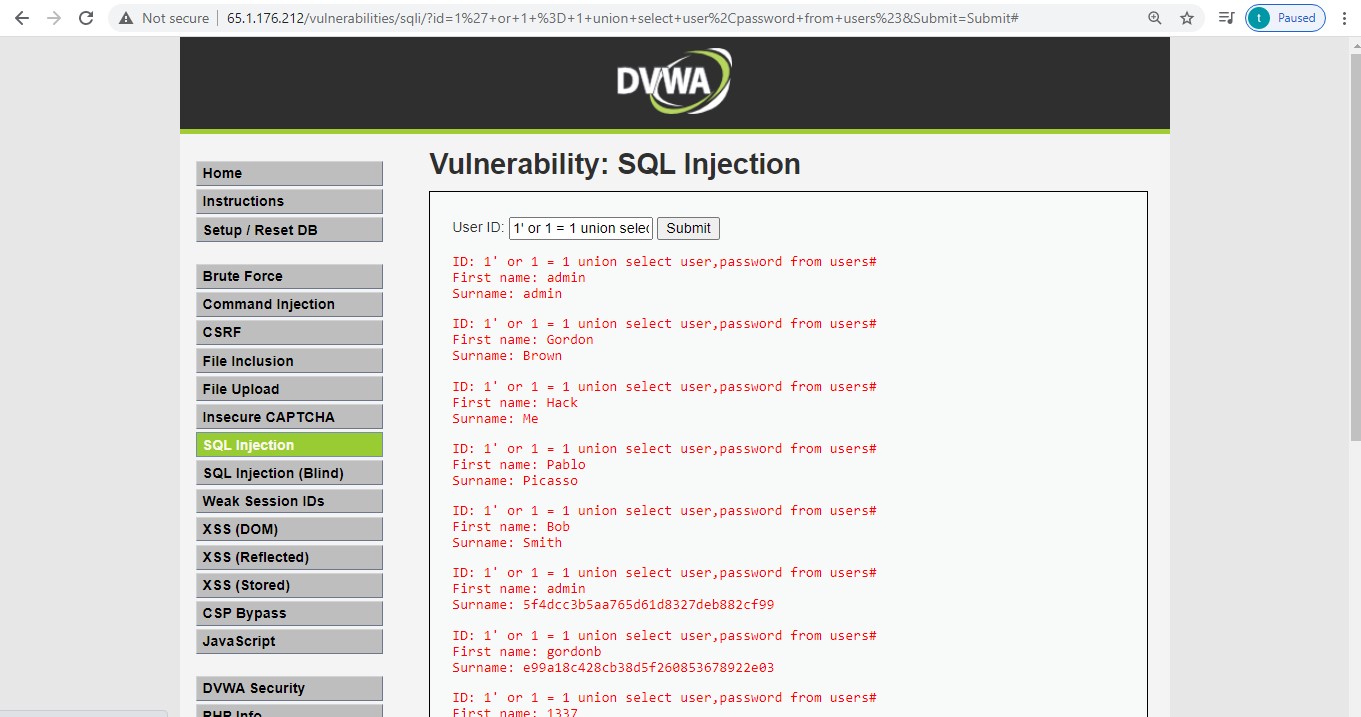
We are exploiting the vulnerability by putting the payload 1%27+or+1+%3D+1+union+select+user%2Cpassword+from+users%23&Submit=Submit in user input to extract usernames and passwords stored in the database.
Detections: Yes
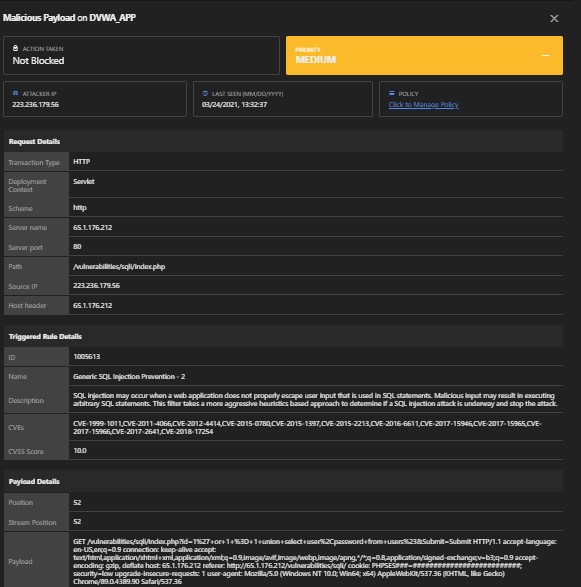
Module: Malicious Payload
Conclusion
As seen in the demo, Application Security is effective at detecting and thwarting advanced threats and vulnerabilities that could cause harm. By implementing Application Security early in the development phase, you can make minor corrections throughout the build process and deploy with full confidence that your app is as strong as possible.
Not only do you reap the security benefits of using an automated, integrated solution like Application Security, but you also strengthen the DevOps culture of collaboration between teams. With everyone on the same team, you can cross the finish line more efficiently and without as much stress.
Curious to try it for yourself? Start your free 30-day trial today. You can also watch serverless and container demos to learn more.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE




