SMS PVA Part 3: Countries Most Impacted by Service

Malware
In this final part, we discuss the countries most affected by SMS PVA services as well as lay out several recommendations to mitigate the risks of such threats.
Part two of our blog entry discussed the impacts and implications of SMS PVA services. The article also explored how these services work by using Carousell as an example. Moreover, it discussed the “benefits” of SMS PVA services to cybercriminals.
In the final installation of our series, we’ll discuss relevant statistics and recommendations to mitigate the threats that SMS PVA services pose.
Geographical distribution
In the screenshots above. ReceiveCode posted the top countries that use their services. From that information, we see Thailand, Indonesia, South Africa, the United States, Russia, Colombia, Bangladesh, Mexico, Turkey, Angola and India routinely make up the top 10 of countries with smart phones affected by smspva.net.
There are some differences if we base the country infection distribution based on Trend Micro’s SPN telemetry data due to market distribution but we can verify that Indonesia, Russia, Thailand, and India are really amongst the top countries with infected Android phones.
Using the same telemetry data, we can map the user-agent of the infected devices to what is most likely the brand and phone model. The following diagram shows a breakdown of the mobile phones that we identified to be communicating with smspva.net’s information collection backend:
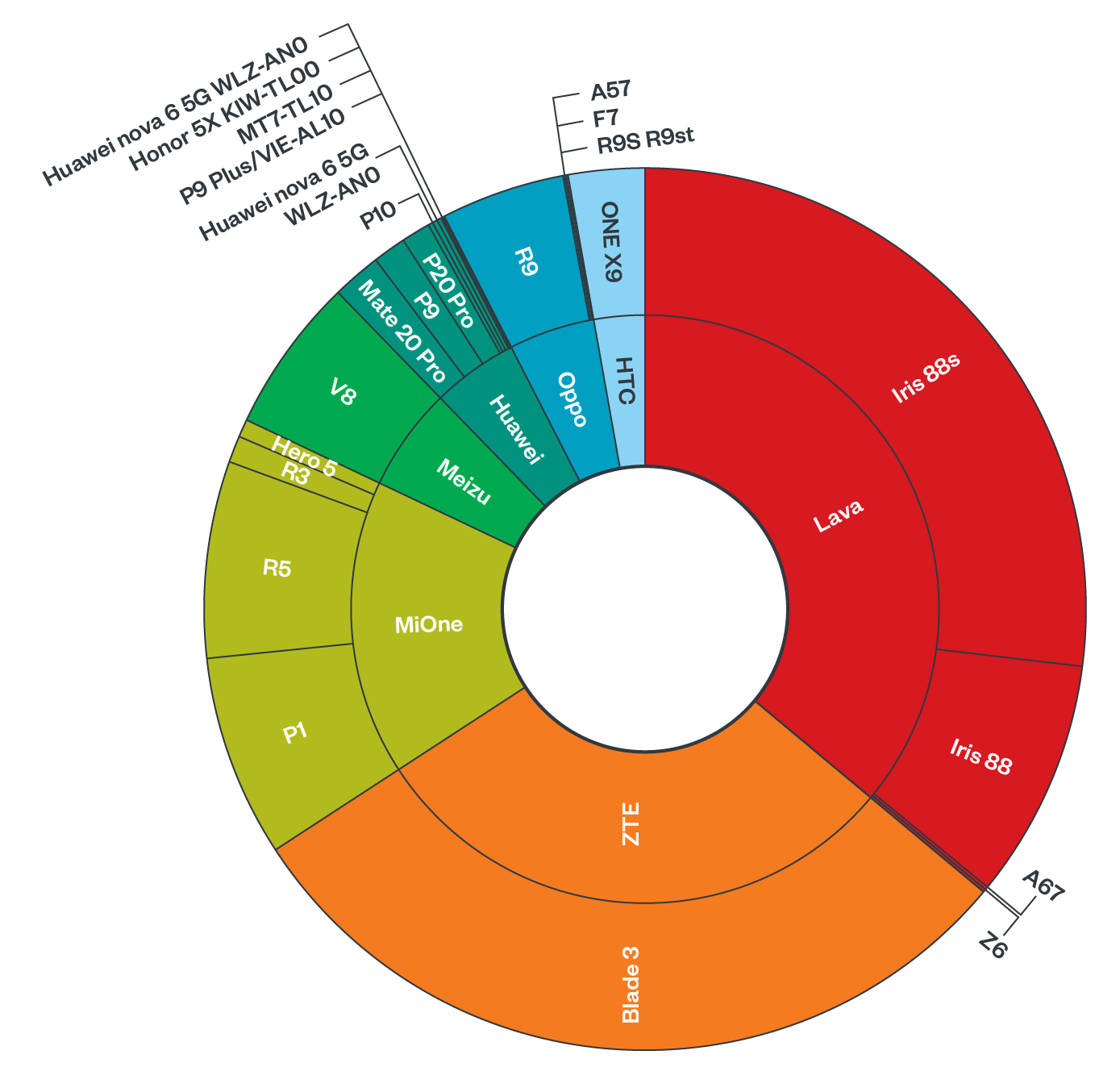
The affected devices are mostly budget brands manufactured in China. Lava is an Indian brand, but some models are manufactured in China, the Iris 88 models seen here are one of those.
This indicates there might be a supply chain compromise somewhere along with the manufacturing of these budget devices, such that it comes pre-installed with the SMS interception dex file or a downloader that installs it at a later time.
Most of the affected services are messaging apps like LINE, WeChat, Telegram, and WhatsApp. Social media platforms like TikTok, Twitter, and Facebook are also affected.
Messaging apps are currently the biggest target of smspva.net users and can be linked to increased spam and fraud from fake accounts on these platforms. There have been increased reports of scams such as romance, stocks pump-and-dump, tourist attraction, and impersonation scams on messaging platforms, with accounts most likely created using SMS PVA services.
Recommendations
We used to enjoy the anonymity that the internet offers, but as our online identifies become more connected with our real-world personas, the need for verified accounts becomes increasingly important to assure authentic behavior and prevent real-world harm.
As of now, SMS verification is the only widespread mechanism to ensure accounts are created by and for real people, not bots, fake personalities, or troll farms. The existence of SMS PVA services brings to light the inadequacy of one-time SMS verification as the only means to validate if an account is created by a real person.
Here are some recommendations we have to mitigate threats brought about by services like smspva.net.
For online platforms and services:
- Have periodic verifications to ensure the mobile number used to verify the account is the day-to-day mobile number used by the account owner. SMS PVA services abuse the fact that SMS verification is only being done one time during account creation. Some applications send in-app verifications if the application is detected to be online. This type of verification may prevent the use of SMS PVA services for the acquisition of the application accounts.
- Platforms need to be careful in launching sign-up or in-game bonus programs with monetary value. We’ve seen groups quickly monetize sign-up and in-game bonuses because of their ability to create bulk accounts. More stringent measures should be taken when launching these programs and should implement additional verifications on top of SMS verification to prevent abuse.
- Some fake accounts can be detected by checking the origin country of the mobile phone against the account profile created. If the mobile number does not match with the ethnical origin, language, gender, profile photo, and/or login IP address of the created account, or the user activity does not match a typical behavior of a user within a particular region, it is a flag the account was possibly registered using SMS PVA services and should require additional verification.
- Profile avatar image or profile attributes reuse. This is especially applicable to accounts created specifically for romance, spam, and stocks investment scams. These accounts are created in bulk and photos of attractive persons are reused as profile photos and randomly generated names.
- Pivot off the content. Most fake accounts post or send the same messages, which can be used as an initial pivot to investigate the veracity of the account.
For smartphone users:
- Ensure the provenance of the devices you sell under your brand name. There have been well-documented cases of devices that came pre-infected with malware.
- Ensure that all the applications included in default ROM images of the devices and the ROM image itself as well as the components that perform ROM update (FOTA/OTA) are trusted and/or coming from trusted sources.
For consumers:
- Secure your phones. Make sure there is no malware running in your smartphone that allows these SMS PVA services to abuse your mobile number. Trend Micro offers TMMS to detect and mitigate malicious code and network traffic related to this type of activity.
- Do not install untrusted applications or applications from untrusted sources on your device.
- Do not use unverified ROM images on your phone devices.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



