Sophisticated ‘Impulse Project’ Crypto Scam Sprawls With 1,000 Affiliate Sites
Researchers have unraveled a web of more than a thousand scam websites that lead back to Russian-language group Impulse Team, which has been running one the largest crypto scam affiliate campaigns of its kind to date.
The fraudulent websites shared similar content intended to trick targets into opening crypto accounts and paying an upfront fee to claim a cryptocurrency prize that would never materialize, according to a report this week from Trend Micro.
With some sites dating back to 2016, analysts at the firm reported that the crypto scam affiliate program, called “Impulse Project” was a mature, professional operation that grows by offering would-be fraudsters with all the tools necessary to start up a franchise of their very own.
“We have been able to uncover a massive cryptocurrency scam involving more than a thousand websites handled by different affiliates,” all linked to Impulse Project, the researchers said.
Calling All Crypto-Fraud Affiliates
Trend Micro found Impulse Project advertising for affiliates on a few Russian-speaking cybercriminal forums. Interested parties were asked to “subscribe” to the service for an undisclosed amount.
“We couldn’t find information regarding the rates applied by the threat actor, but joining these types of programs typically requires a fee,” according to the post.
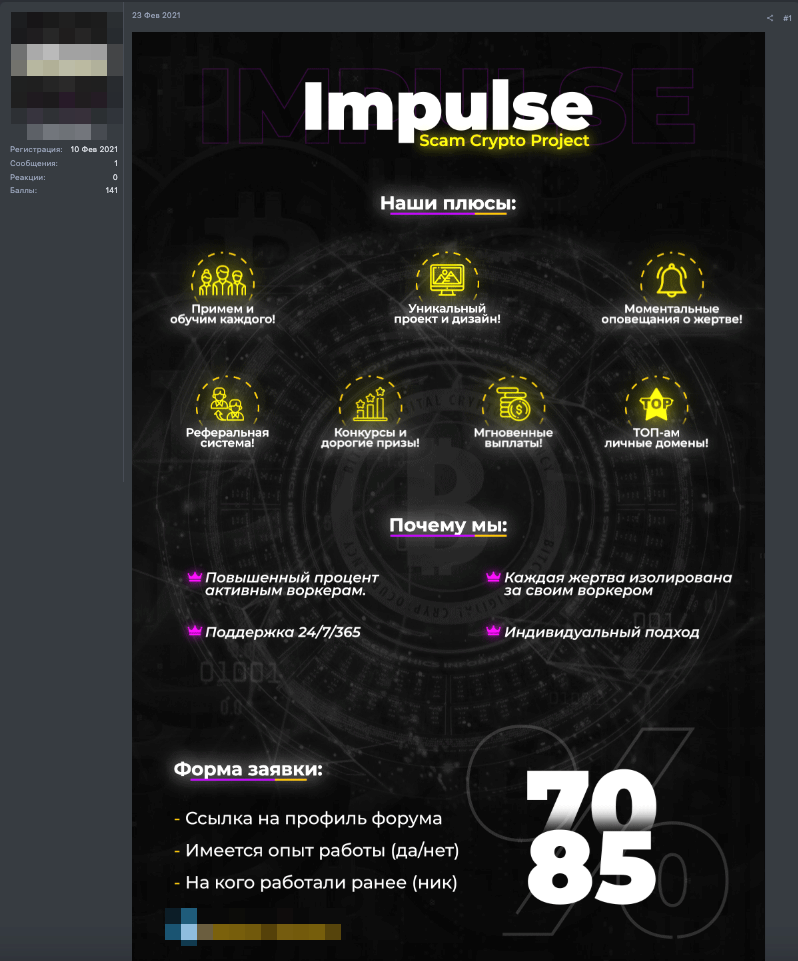
“Furthermore, a percentage of every fraudulent transaction goes to the masterminds.”
Affiliates are asked to set up their own domain names and then hand them over to the Impulse Team, which configures them with scripts used for CloudFlare services.
“Affiliates get one database for their websites,” the researchers explained. “This means that if a victim creates an account on one website, the credentials also work for all the other websites used by the affiliate. This provides additional evidence that the affiliates run their own operation separately from each other.”
One of the Largest Crypto Scams Ever Seen
While Trend Micro’s report doesn’t pinpoint a specific dollar amount the Impulse Project crypto scam has pulled in over the years, it estimates victims were in the thousands, “making it perhaps one of the largest-ever crypto scam campaigns.”
For comparison, the current crypto fraud campaign at the top of the leaderboard is OneCoin, which was estimated to have stolen more than $4 billion from 3 million unwitting investors, with an operation dating back to 2014, Craig Jones, vice president of security operations at Ontinue, tells Dark Reading.
“While the total financial impact of the Impulse Team’s operation is not specified in the Trend Micro report, its vast network of over a thousand websites suggests a considerable potential reach and impact
Impulse Project Sophistication Kept It Hidden
Unlike OneCoin, led by the notorious “Cryptoqueen” Ruja Ignatova, Impulse Project is more careful in picking its targets, according to Karl Steinkamp, director of delivery transformation and automation at Coalfire, who spoke to Dark Reading about the cryptocurrency scam operations.
“The approach of being tactical in this manner indicates a level of sophistication above your common cybercriminal,” Steinkamp explains. “These individuals are content in getting fewer, higher value targets and access vs the ‘spray and pray’ method of malware distribution, whereby malware is widely distributed with the malware expectation of impacting more potential, yet less valuable targets.”
A smaller campaign footprint also makes detection more difficult, Steinkamp adds.
“When malware is more broadly distributed, the time for systems to identify and quarantine it is dramatically more,” he says. “The focus here drives home the cybercriminal’s approach and motive.”
Impulse Project Detection & Mitigation
As affiliate programs like Impulse Project continue to offer easy-to-use, crypto-scammer starter packs, it’s up to security teams to drive user awareness of these types of social engineering campaigns and keep them from becoming a target.
“The economy of cybercrime has evolved to include affiliate programs for all kinds of scams and operations,” says Melissa Bischoping, director of endpoint security research at Tanium. “Enterprise security teams need to be aware that popular, easy-to-deploy affiliate offerings may result in a lot more attempts to phish or scam users.”
Network monitoring can provide some detection help, but ultimately these kinds of campaigns rely on user behavior for success, she adds.
“Though higher in volume, tactics, techniques, and procedures (TTPs) will often be similar among affiliates, which can aid in detection and prevention,” Bischoping advises. “For scams such as these that rely on social engineering for success, education and awareness is an essential piece of your security portfolio.”
Read More HERE
