Spam is Chipotle’s secret ingredient: Marketing email hijacked to dish up malware
Between July 13 and July 16, someone took over the Mailgun account owned by restaurant chain Chipotle Mexican Grill and placed an order for login credentials using misappropriated marketing messages.
Phish-fighting firm INKY said on Thursday that it spotted 121 phishing emails during this period originating from Chipotle’s Mailgun account.
The phishing messages included two fake voicemail notifications with attached malware, otherwise known as “vishing” among those who make such distinctions. They also included 14 emails designed to look like USAA Bank communiques and 105 messages dressed up as if they came from Microsoft. These faked missives pointed recipients to credential harvesting websites designed to mimic USAA Bank and Microsoft Sign-in pages respectively.
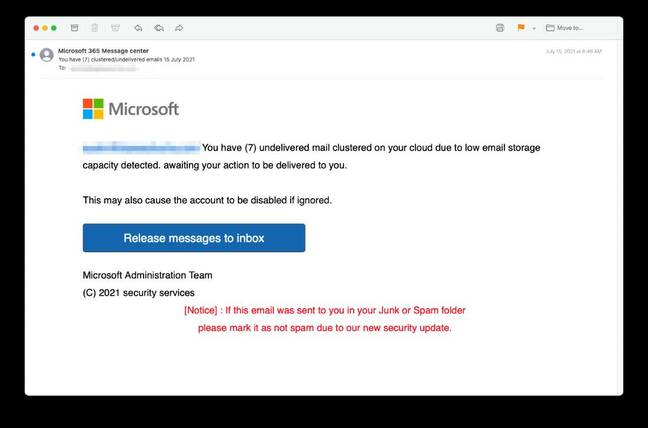
To a trained eye, or anyone who might wonder why USAA or Microsoft messages would originate from mail.chipotle.com, the deception would be evident upon examining the raw email header data. But a sample Microsoft phishing message published by INKY suggests that inconsistency would not have been visible to recipients.
“It is important that recipients (and email security software) notice the discrepancy between a sender’s display name (Microsoft, USAA, VM Caller ID) and its actual email address (postmaster@chipotle[.]com),” wrote Bukar Alibe, cyber security analyst at INKY, in a blog post provided to The Register. “It’s pretty clear that Microsoft and USAA would never use mail.chipotle[.]com URLs to resolve account issues.”
“But secure email gateways often check only whether the sending domain is legitimate and is transmitting from an approved range of IP addresses. That schema can lead to absurdities like Microsoft apparently sending an account notice via Chipotle.”
This particular approach to phishing was employed successfully by the Nobelium group infamous for its attack on SolarWinds: the reportedly Kremlin-run gang used the United States Agency for International Development’s (USAID) email marketing account at Constant Contact, a Mailgun competitor, to distribute malware.
One advantage of hijacking email marketing accounts is that such services tend to make an effort to ensure their messages get delivered by minimizing reputation-tarnishing spam and applying messaging security technology like SPF, DKIM, and DMARC.
However, in an email to The Register, Alibe said the messages were caught before sender credibility came into play. “Despite the Chipotle-Mailgun origin, INKY still labeled these emails as dangerous so fortunately our users were either warned or the emails went to quarantine,” he said.
Dave Baggett, CEO of INKY, added, “Of course we don’t know the outcomes for other mail protection vendors’ customers.”
Alibe said it’s not clear how Chipotle’s Mailgun account was compromised. “We have seen phishing emails and sites impersonate Mailgun to harvest Mailgun credentials so it’s highly probable that a Chipotle employee was a credential harvesting victim,” he said.
Baggett said it’s possible a Chipotle employee opened an email attachment with malware that led to the compromise of the employee’s account or device.
“In general, INKY sees a rising trend here: attackers are increasingly using ‘shared infrastructure’ – cloud services shared across many companies and users – to hide their true identities,” he said. “We see this in abuse of cloud file sharing services like Dropbox as well as cloud email infrastructure like Mailgun.”
It’s also not known, to INKY at least, where the phishing attack came from. “These emails originated from Mailgun servers so we have no hints on who is behind this attack or their location,” said Alibe.
“It’s also important to remember that it’s easy for attackers to set up multiple untraceable online presences in any virtual territory they choose,” said Baggett. “So in 2021 the geolocation of the IPs used by an attacker says nothing about where the attacker is truly domiciled; it’s mainly useful in assessing what cloud provider was breached. In other words: it’s straightforward to tie an IP used in an attack to a particular cloud provider, but generally impossible to link to a source actor country.”
The Register asked Chipotle for details about how the compromise occurred and we’ve not heard back. ®
READ MORE HERE