Spyware Co Leaves Terabytes Of Exposed Data Online
This story is part of When Spies Come Home, a Motherboard series about powerful surveillance software ordinary people use to spy on their loved ones.
A company that markets cell phone spyware to parents and employers left the data of thousands of its customers—and the information of the people they were monitoring—unprotected online.
The data exposed included selfies, text messages, audio recordings, contacts, location, hashed passwords and logins, Facebook messages, among others, according to a security researcher who asked to remain anonymous for fear of legal repercussions.
Last week, the researcher found the data on an Amazon S3 bucket owned by Spyfone, one of many companies that sell software that is designed to intercept text messages, calls, emails, and track locations of a monitored device.
Motherboard was able to verify that the researcher had access to Spyfone’s monitored devices’ data by creating a trial account, installing the spyware on a phone, and taking some pictures. Hours later, the researcher sent back one of those pictures.
Read More: Don’t Use Software To Spy On Your Spouse
The researcher said that the exposed data contained several terabytes of “unencrypted camera photos.”
“There’s at least 2,208 current ‘customers’ and hundreds or thousands of photos and audio in each folder,” he told Motherboard in an online chat. “There is currently 3,666 tracked phones.”
Got a tip? You can contact this reporter securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzo@motherboard.tv
The exposed data also included 44,109 unique email addresses, according to Troy Hunt, who maintains the data breach website Have I Been Pwned, and who analyzed some of the data after the researcher shared it with him.
The company’s backend services were also left wide open, not requiring a password to log into them, according to the researcher, who said he was able to create admin accounts and see customer data.
A screenshot sent by the researcher, showing he had admin access to Spyfone portals.
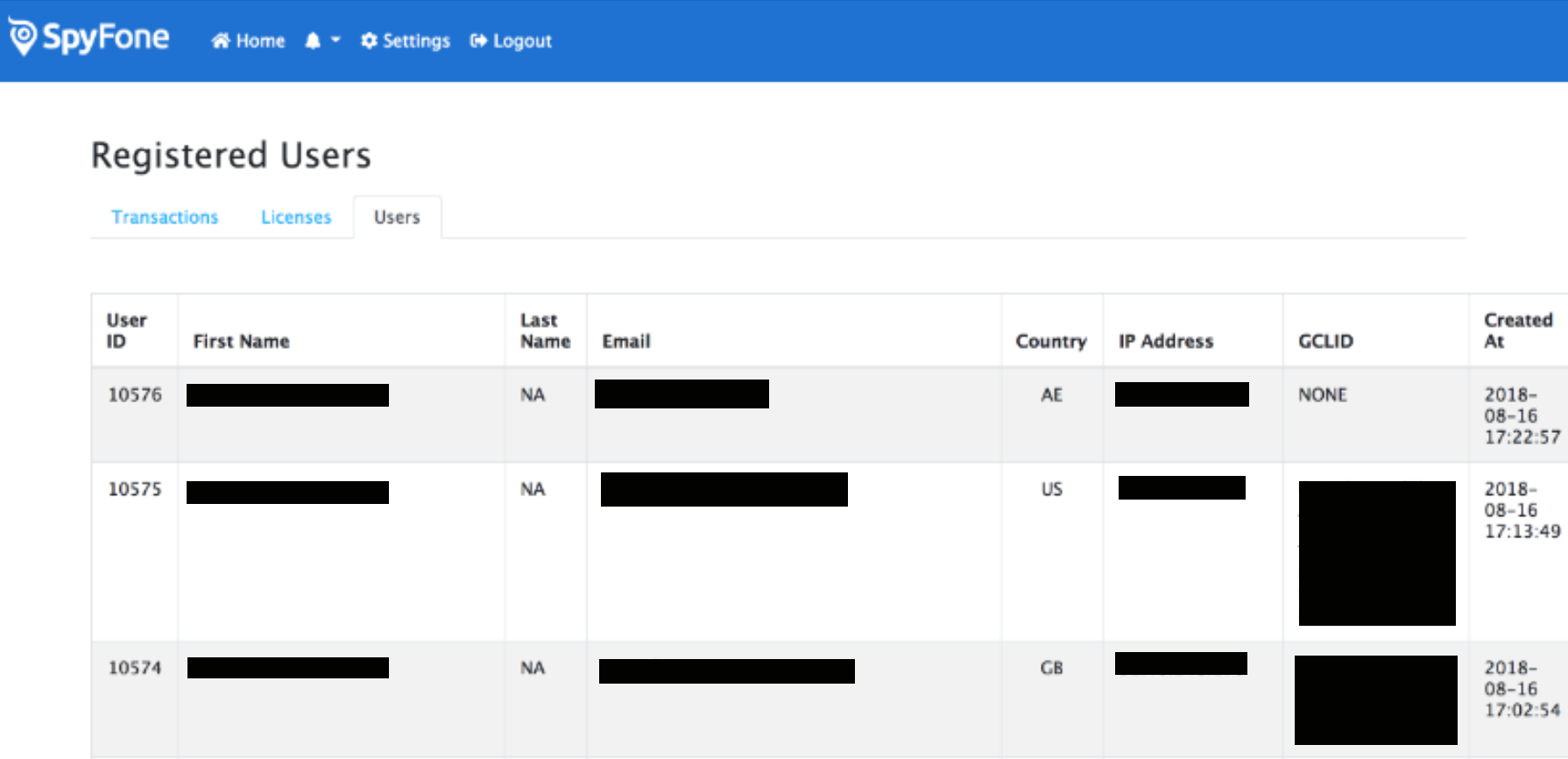
Spyfone also left one of it’s APIs completely unprotected online, allowing anyone who guesses the URL to read what appears to be an up-to-date and constantly updating list of customers. The site shows first and last names, email and IP addresses. As of Thursday, there were more than 11,000 unique email addresses in the database, according to a Motherboard analysis.
“Spyfone appears to be a magical combination of shady, irresponsible, and incompetent,” Eva Galperin, the director of cybersecurity at digital rights group Electronic Frontier Foundation, told Motherboard.
Steve McBroom, a Spyfone representative, told Motherboard on Monday that the company is investigating the leak, and expressed relief that the person who found it had good intentions.
“Thank god it is a researcher, someone good trying to protect,” McBroom said in a phone call.

On Wednesday, McBroom confirmed the data leak “that affected approximately 2,200 of our customers.”
“We have partnered with leading data security firms to assist in our investigation, and continue to coordinate with law enforcement authorities about this situation. Every day our team takes great strides to enhance our site’s security and we certainly anticipate that this recent data breach is the last,” McBroom said. “Communications about the breach and the investigation have gone out to our customers.”
This is the latest in a seemingly endless series of data breaches and leaks of consumer spyware companies. In the last 18 months, Motherboard has reported hacks on FlexiSpy, two separate ones on Retina-X, Spy Master Pro, Mobistealth, and SpyHuman. The common element among all these appears to be the companies’ poor—if not irresponsible—approach to security, especially regarding their most sensitive data: that of people monitored, some of whom are children.
Joseph Cox contributed reporting.
Solve Motherboard’s weekly, internet-themed crossword puzzle: Solve the Internet .
READ MORE HERE


