sLoad launches version 2.0, Starslord
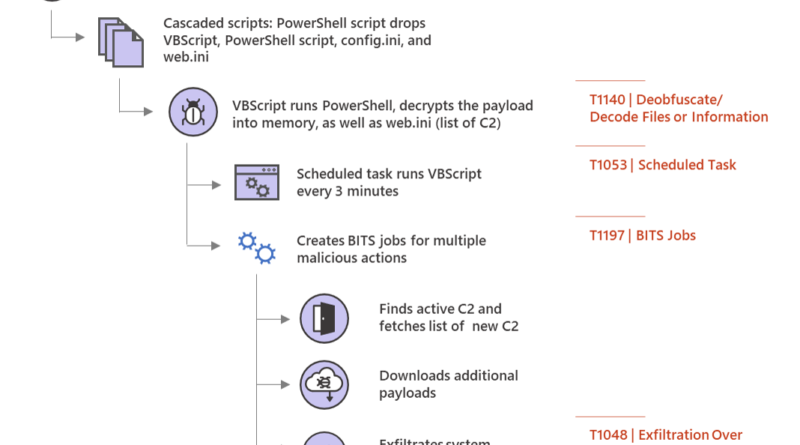
sLoad has launched version 2.0. With the new version, sLoad, which is a PowerShell-based Trojan downloader notable for its almost exclusive use of the Windows BITS service for malicious activities, has added an anti-analysis trick and the ability to track the stage of infection for every affected machine.
The post sLoad launches version 2.0, Starslord appeared first on Microsoft Security. READ MORE HERE…