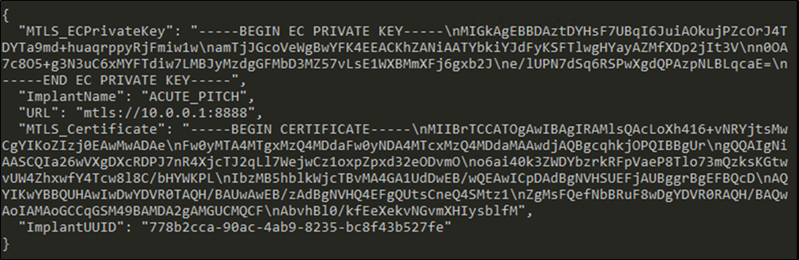
Looking for the ‘Sliver’ lining: Hunting for emerging command-and-control frameworks
Threat actors evade detection by adopting the Sliver command-and-control (C2) framework in intrusion campaigns.
The post Looking for the ‘Sliver’ lining: Hunting for emerging command-and-control frameworks appeared first on Microsoft Security Blog. READ MORE HERE…