Forrester names Microsoft a Leader in 2019 Endpoint Security Suites Wave
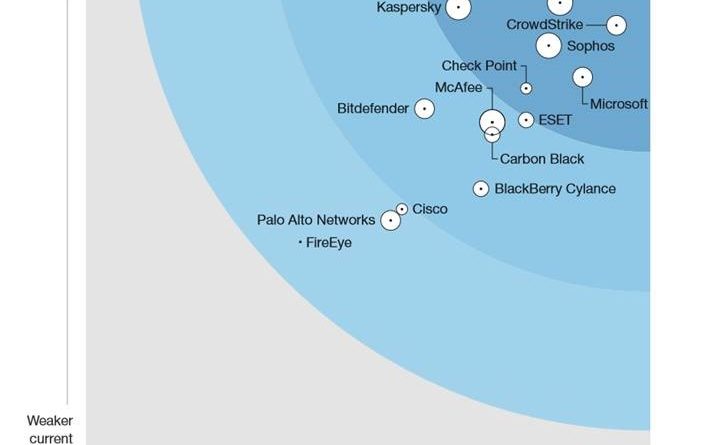
Microsoft is positioned as a leader in The Forrester Wave™: Endpoint Security Suites, Q3 2019, receiving among the second highest scores in both the strategy and market presence categories.
The post Forrester names Microsoft a Leader in 2019 Endpoint Security Suites Wave appeared first on Microsoft Security. READ MORE HERE…