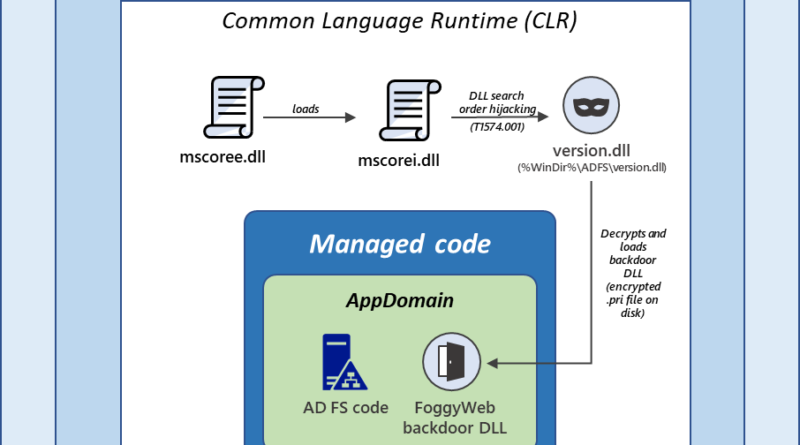
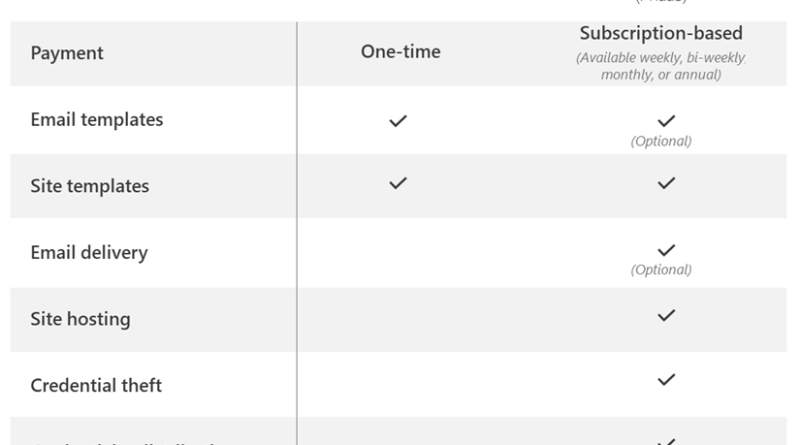
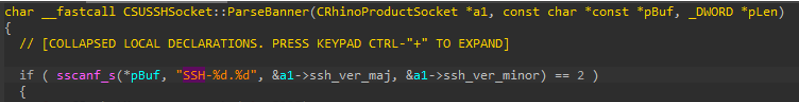
AI-driven adaptive protection against human-operated ransomware
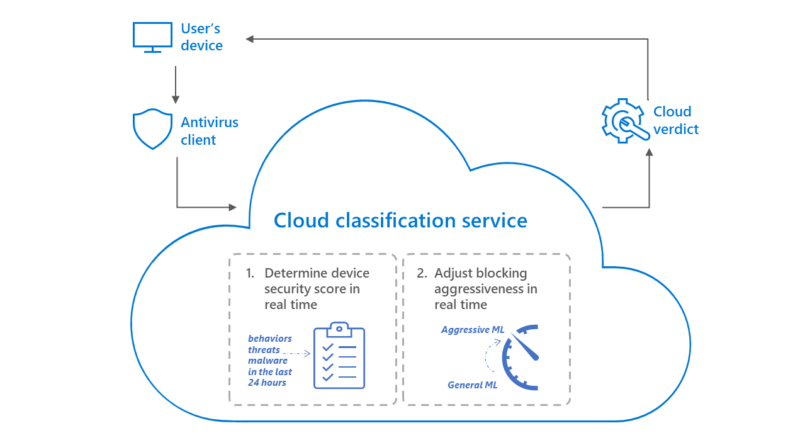
We developed a cloud-based machine learning system that, when queried by a device, intelligently predicts if it is at risk, then automatically issues a more aggressive blocking verdict to protect the device, thwarting an attacker’s next steps.
The post AI-driven adaptive protection against human-operated ransomware appeared first on Microsoft Security Blog. READ MORE HERE…