Widespread credential phishing campaign abuses open redirector links
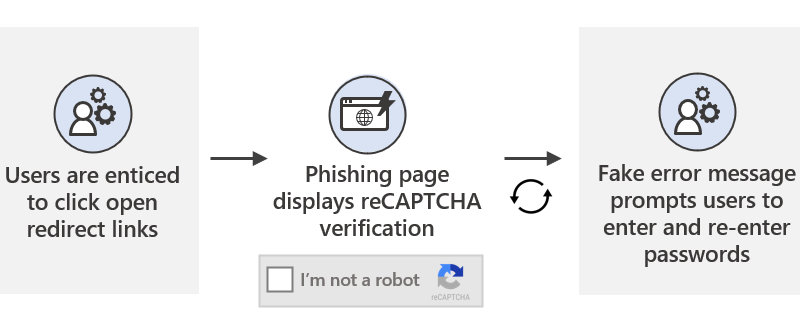
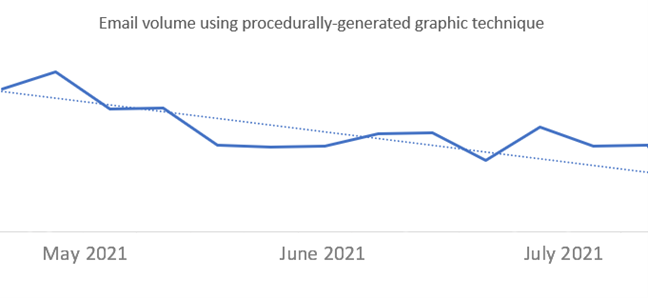
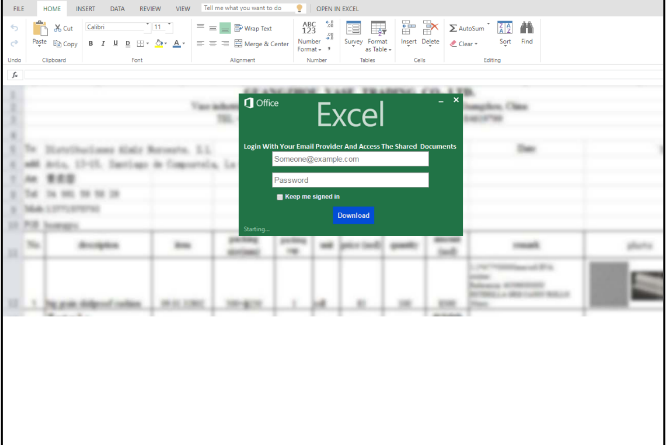
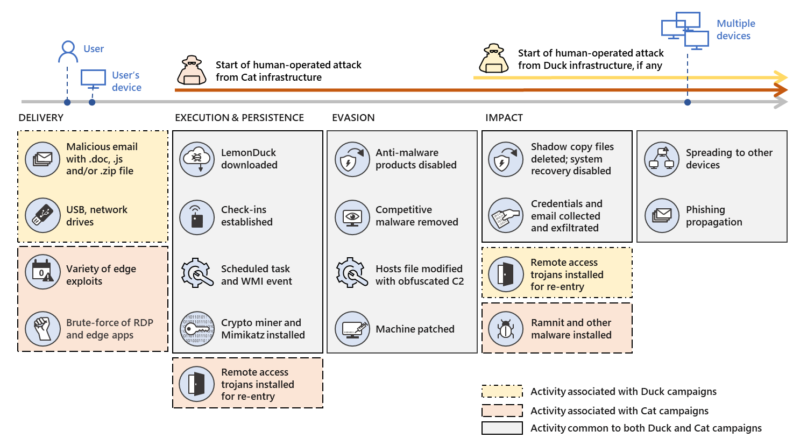
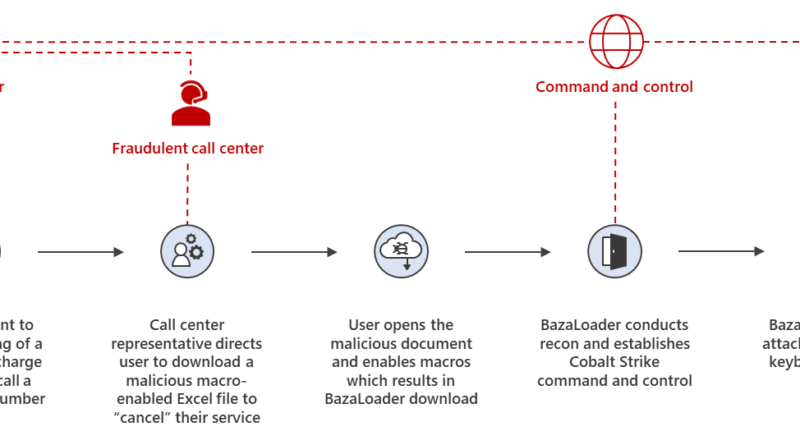
Microsoft has been actively tracking a widespread credential phishing campaign using open redirector links, which allow attackers to use a URL in a trusted domain and embed the eventual final malicious URL as a parameter.
The post Widespread credential phishing campaign abuses open redirector links appeared first on Microsoft Security Blog. READ MORE HERE…