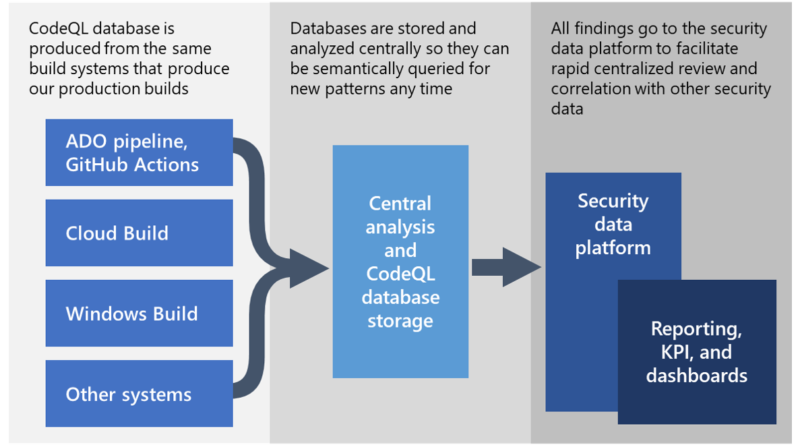
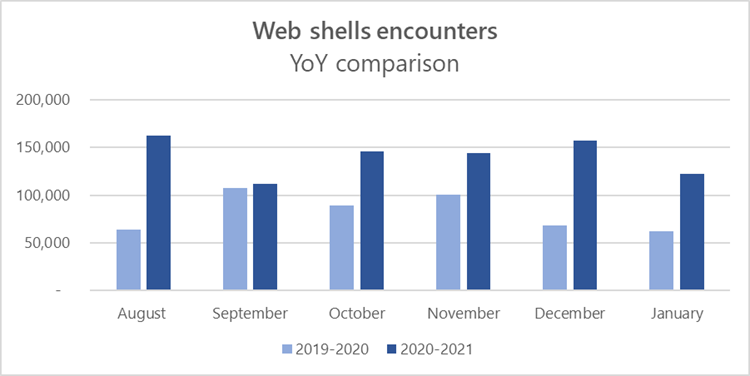
New Security Signals study shows firmware attacks on the rise; here’s how Microsoft is working to help eliminate this entire class of threats
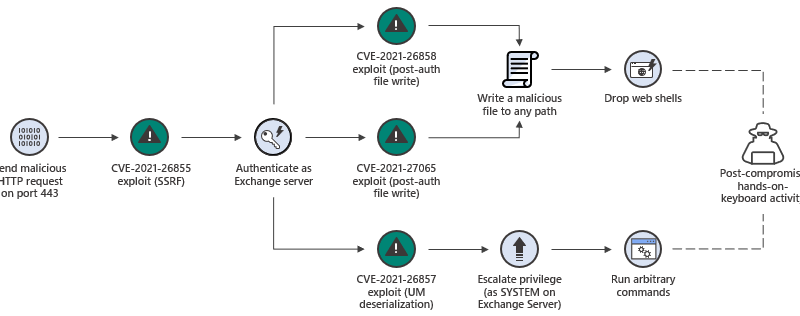
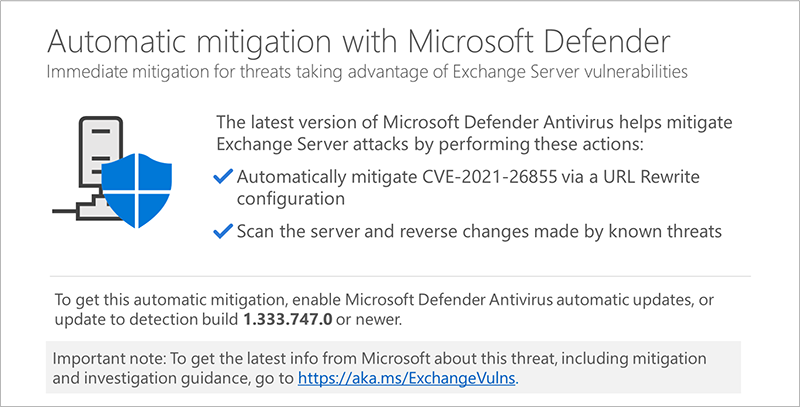
The March 2021 Security Signals report showed that more than 80% of enterprises have experienced at least one firmware attack in the past two years, but only 29% of security budgets are allocated to protect firmware.
The post New Security Signals study shows firmware attacks on the rise; here’s how Microsoft is working to help eliminate this entire class of threats appeared first on Microsoft Security. READ MORE HERE…