Best practices for defending Azure Virtual Machines
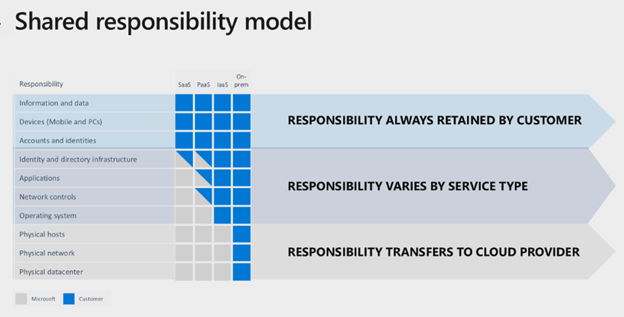
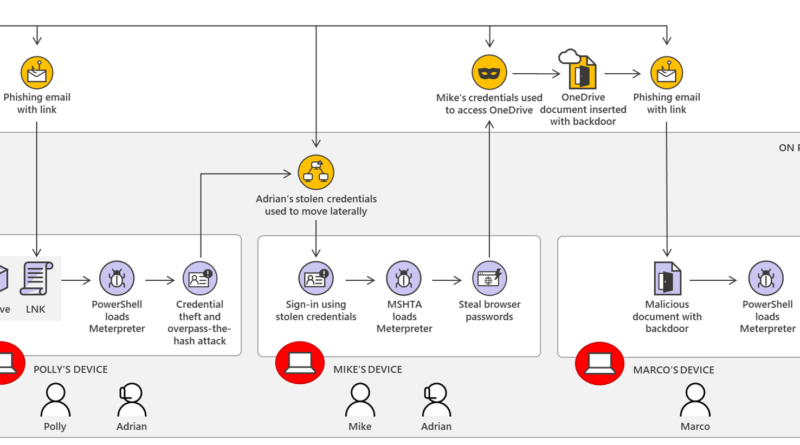
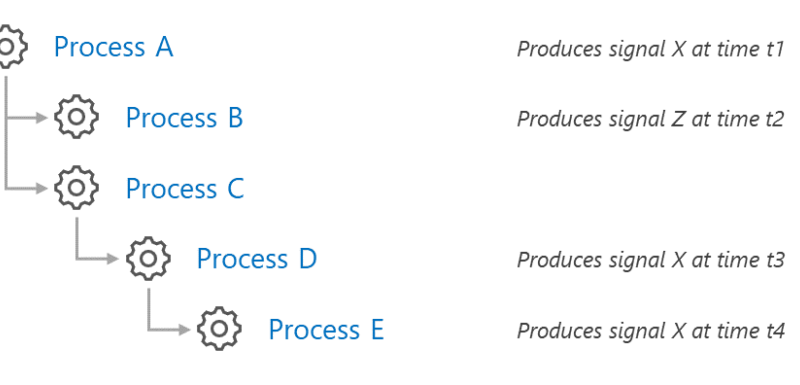
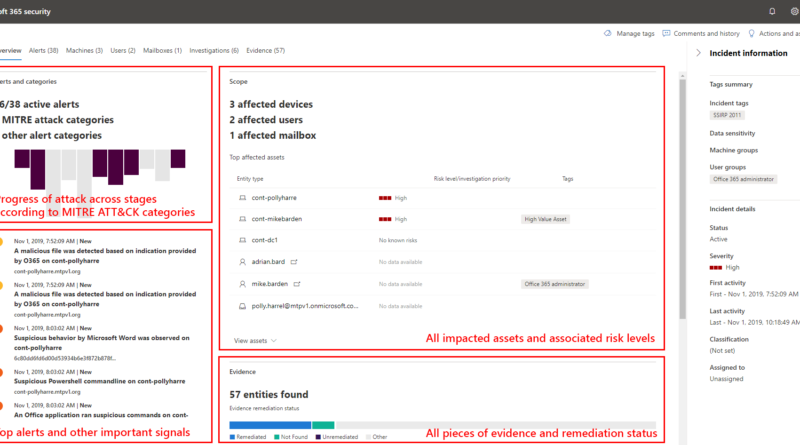
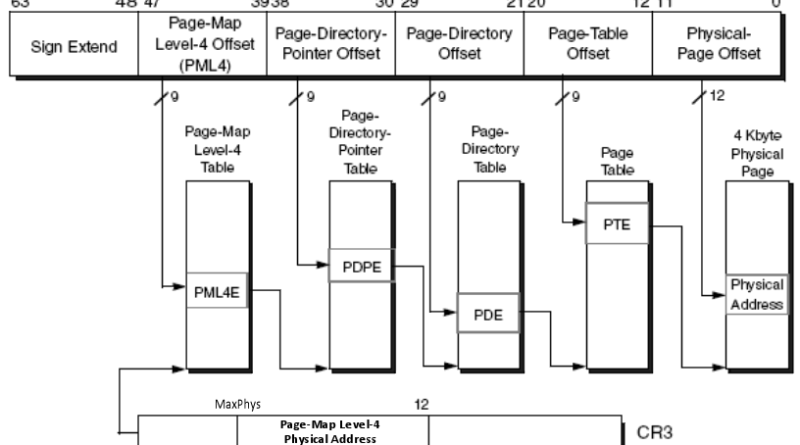
One of the things that our Detection and Response Team (DART) and Customer Service and Support (CSS) security teams see frequently during investigation of customer incidents are attacks on virtual machines from the internet. This is one area in the cloud security shared responsibility model where customer tenants are responsible for security. Security is a…
The post Best practices for defending Azure Virtual Machines appeared first on Microsoft Security. READ MORE HERE…