Ghost in the shell: Investigating web shell attacks
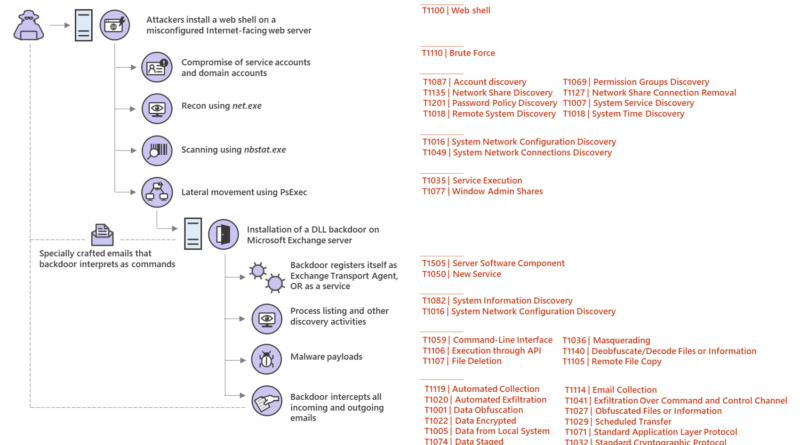
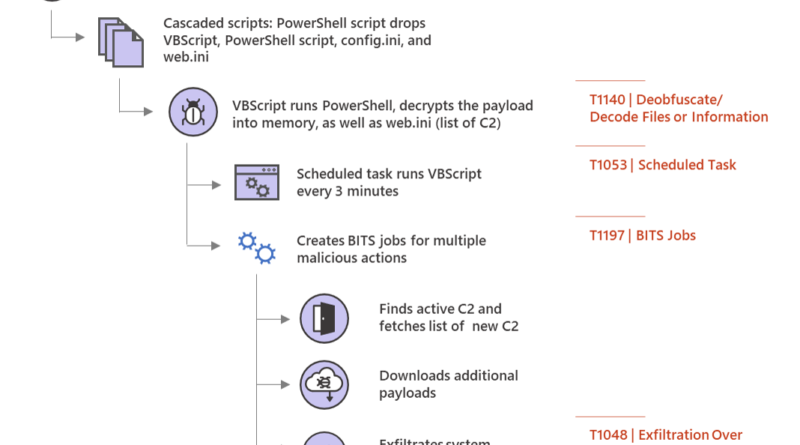
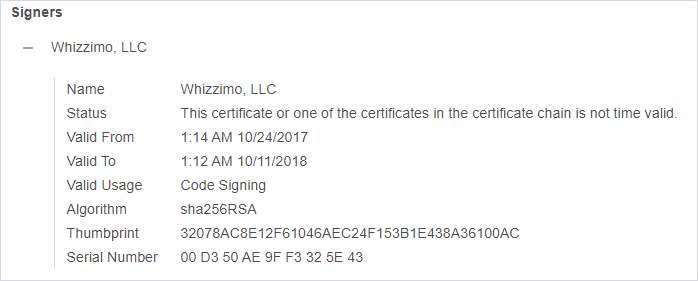
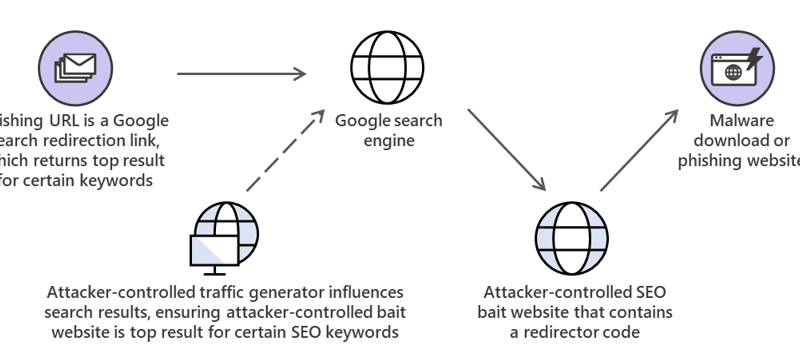
Web shell attacks allow adversaries to run commands and steal data from an Internet-facing server or use the server as launch pad for further attacks against the affected organization.
The post Ghost in the shell: Investigating web shell attacks appeared first on Microsoft Security. READ MORE HERE…