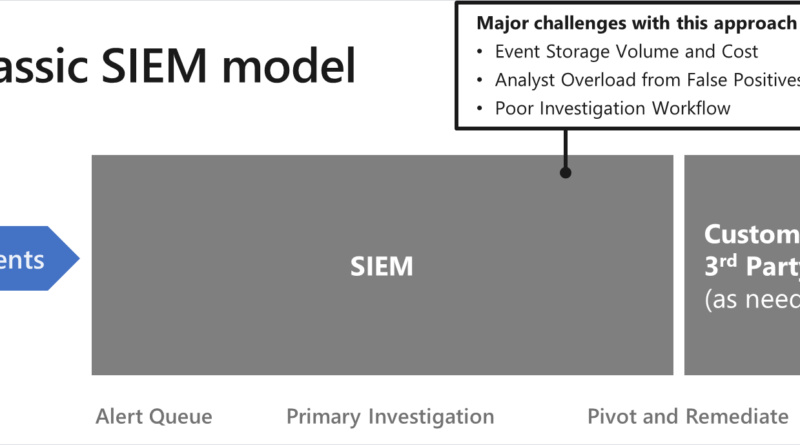
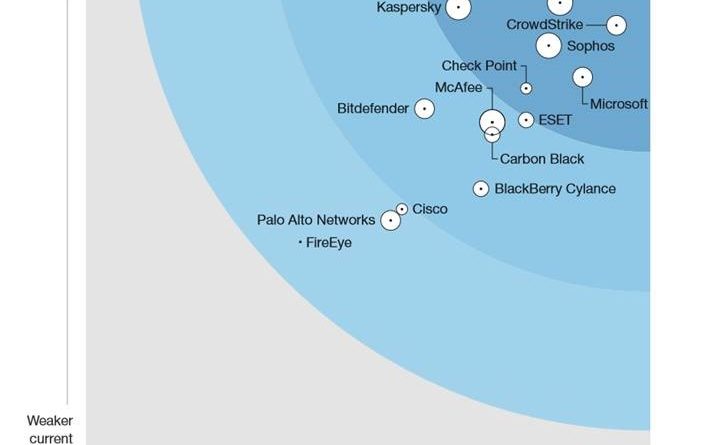
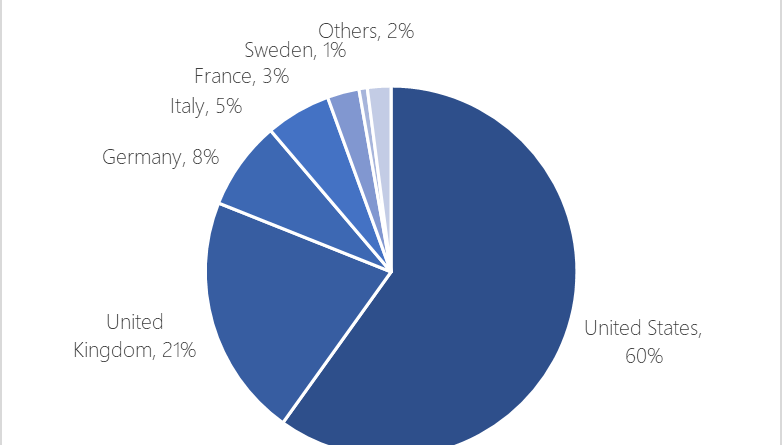
Microsoft works with researchers to detect and protect against new RDP exploits
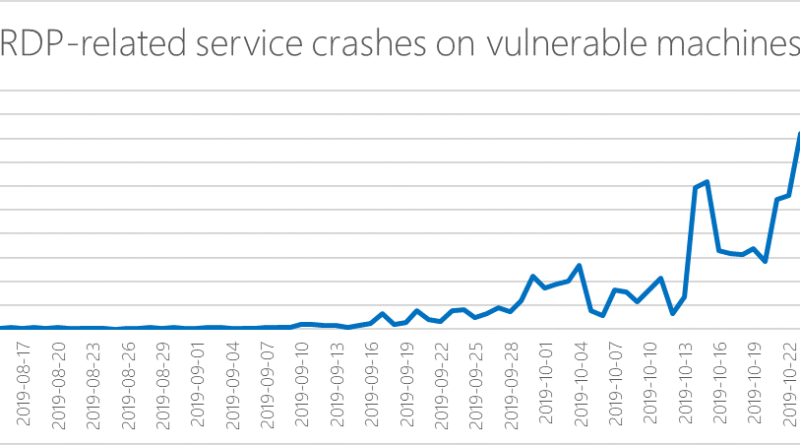
The new exploit attacks show that BlueKeep will be a threat as long as systems remain unpatched, credential hygiene is not achieved, and overall security posture is not kept in check.
The post Microsoft works with researchers to detect and protect against new RDP exploits appeared first on Microsoft Security. READ MORE HERE…