Beneath the surface: Uncovering the shift in web skimming
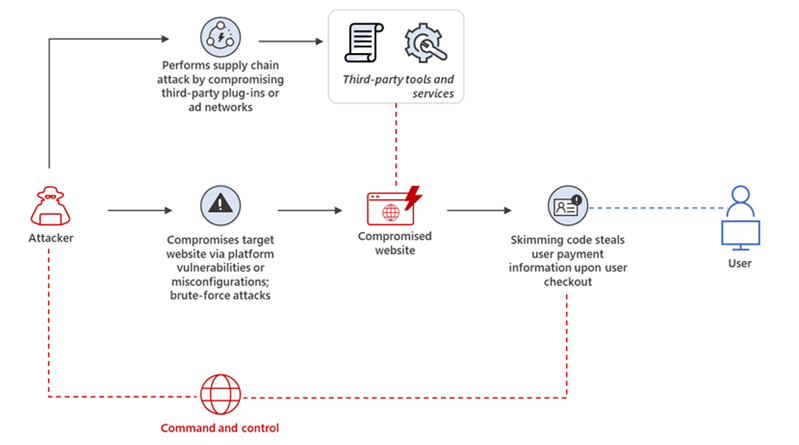
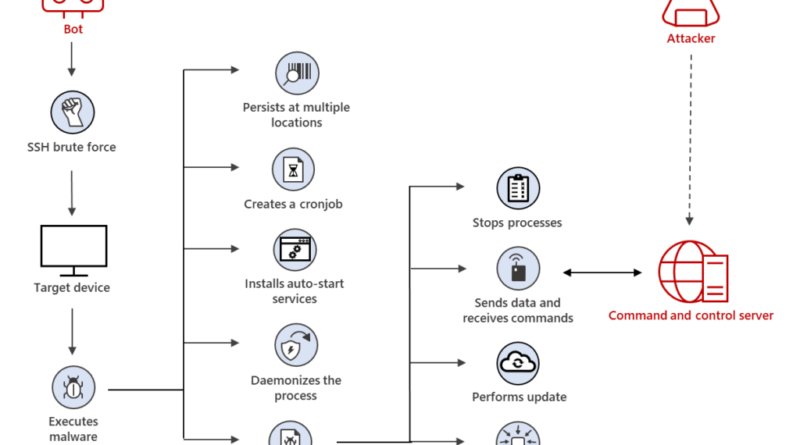
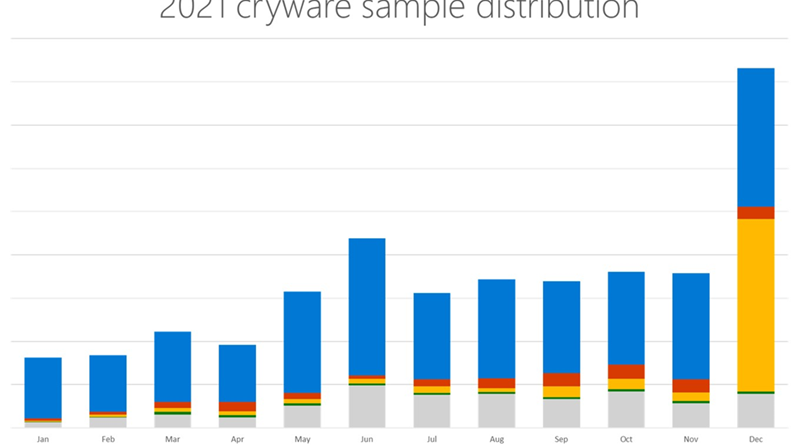
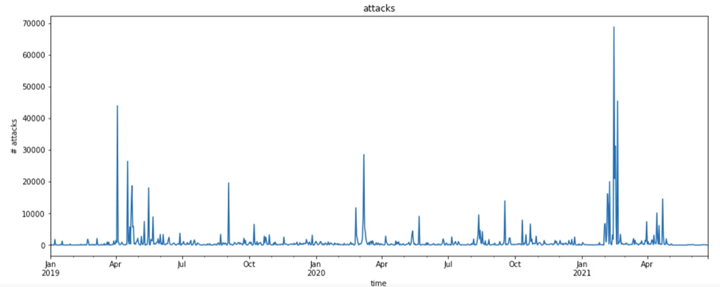
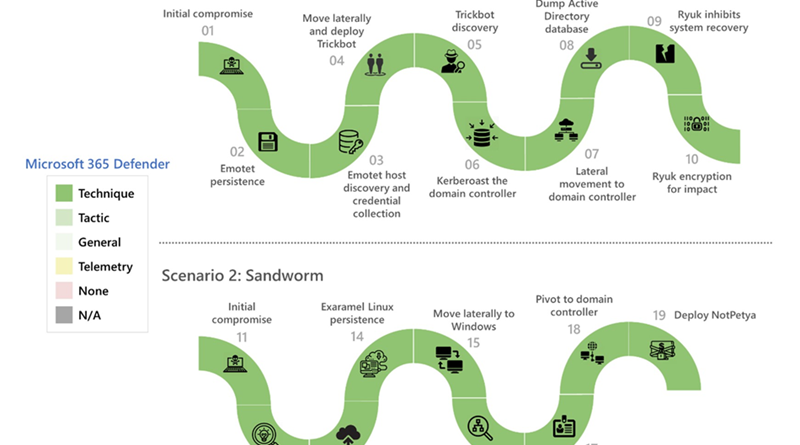
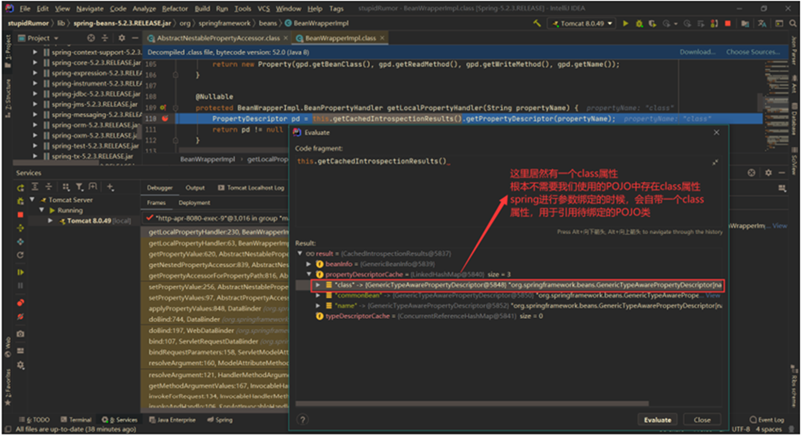
Web skimming campaigns now employ various obfuscation techniques to deliver and hide the skimming scripts. It’s a shift from earlier tactics where attackers conspicuously injected the malicious scripts into e-commerce platforms and content management systems (CMSs) via vulnerability exploitation, making this threat highly evasive to traditional security solutions.
The post Beneath the surface: Uncovering the shift in web skimming appeared first on Microsoft Security Blog. READ MORE HERE…