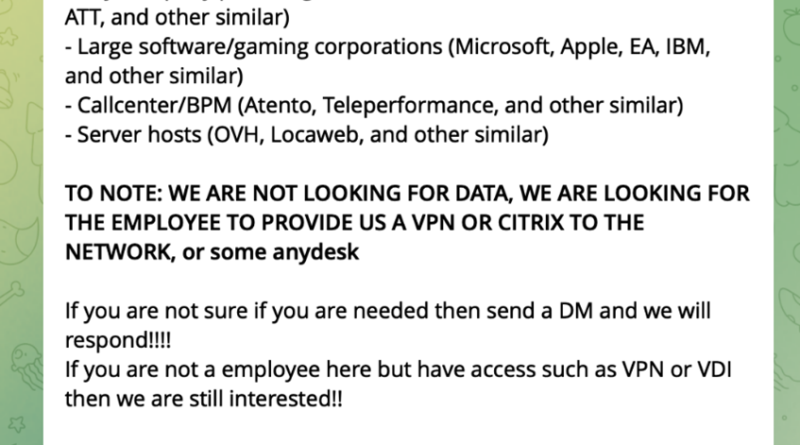
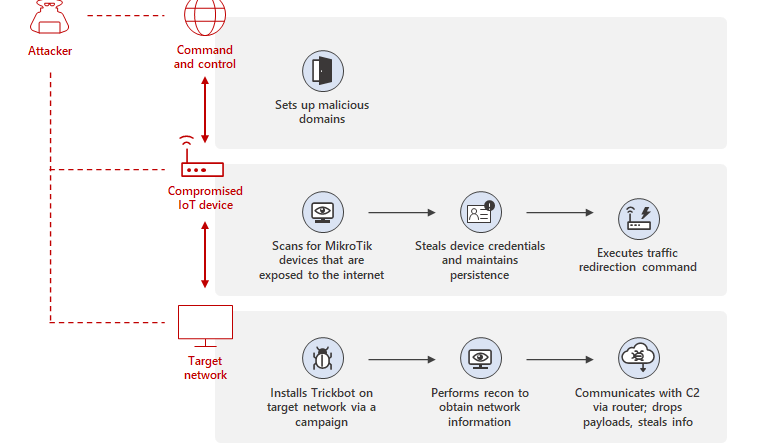
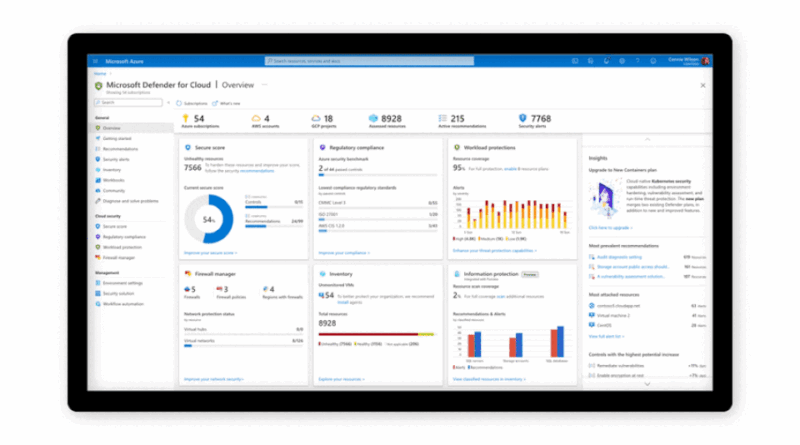
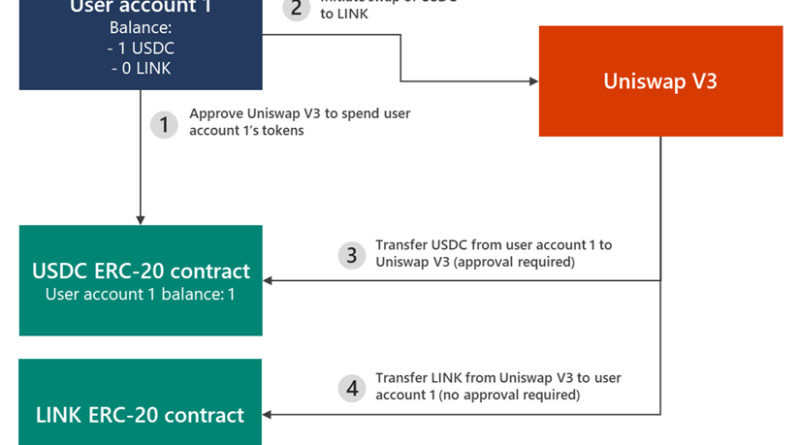
Microsoft protects against human-operated ransomware across the full attack chain in the 2022 MITRE Engenuity ATT&CK® Evaluations
For the fourth year in a row, the independent MITRE Engenuity ATT&CK® Evaluations demonstrated that threats are no match for Microsoft’s multi-platform extended detection and response (XDR) defense capabilities.
The post Microsoft protects against human-operated ransomware across the full attack chain in the 2022 MITRE Engenuity ATT&CK® Evaluations appeared first on Microsoft Security Blog. READ MORE HERE…