Evolved phishing: Device registration trick adds to phishers’ toolbox for victims without MFA
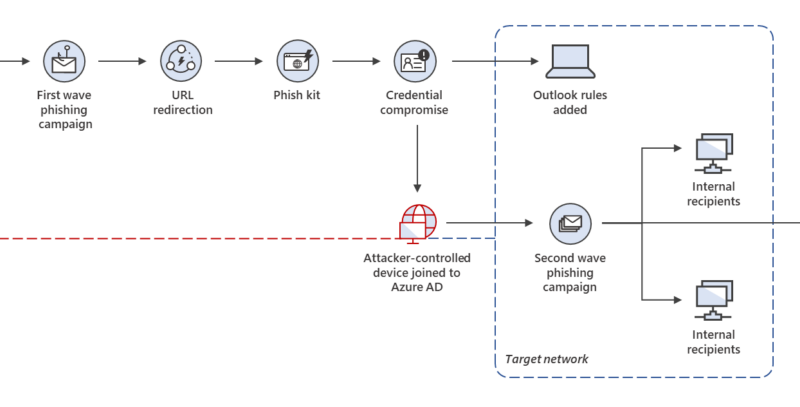
We uncovered a large-scale, multi-phase campaign that adds a novel technique to traditional phishing tactics by joining an attacker-operated device to an organization’s network to further propagate the campaign.
The post Evolved phishing: Device registration trick adds to phishers’ toolbox for victims without MFA appeared first on Microsoft Security Blog. READ MORE HERE…