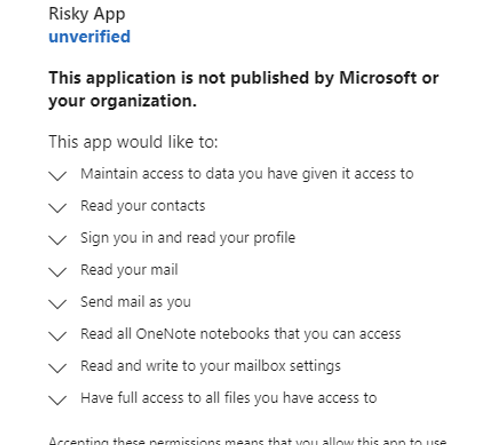
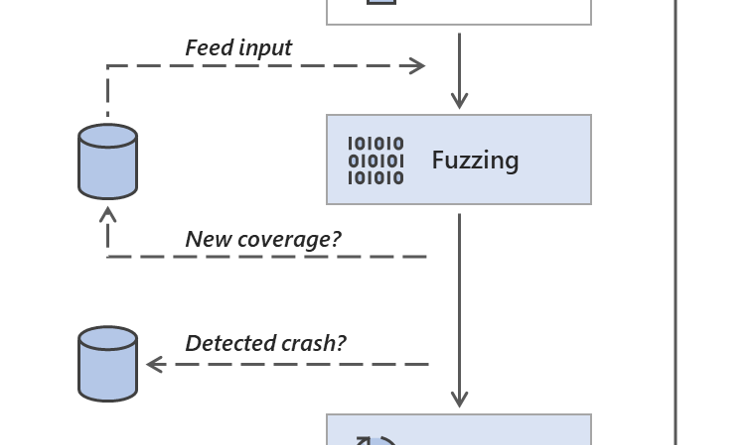
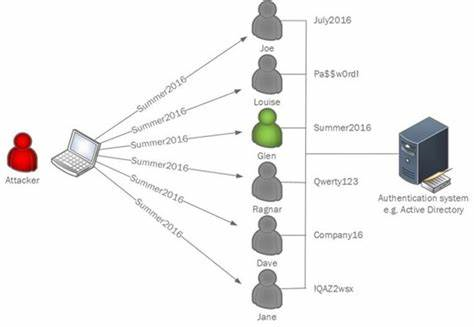
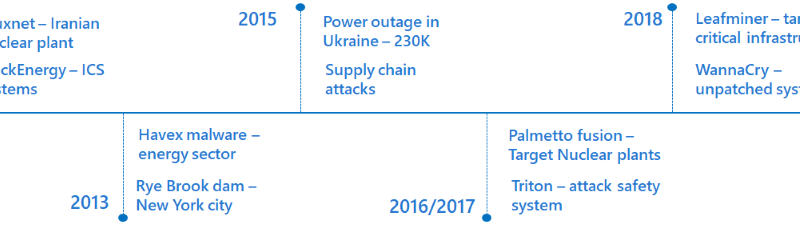
Top Tips For Home Cybersecurity And Privacy In A Coronavirus-Impacted World (part 2)
The past few months have seen radical changes to our work and home life under the Coronavirus threat, upending norms and confining millions of American families within just four walls. In this context, it’s not surprising that more of us are spending an increasing portion of our lives online. But this brings with it some…
The post Top Tips For Home Cybersecurity And Privacy In A Coronavirus-Impacted World (part 2) appeared first on . Read More HERE…