How to gain 24/7 detection and response coverage with Microsoft Defender ATP
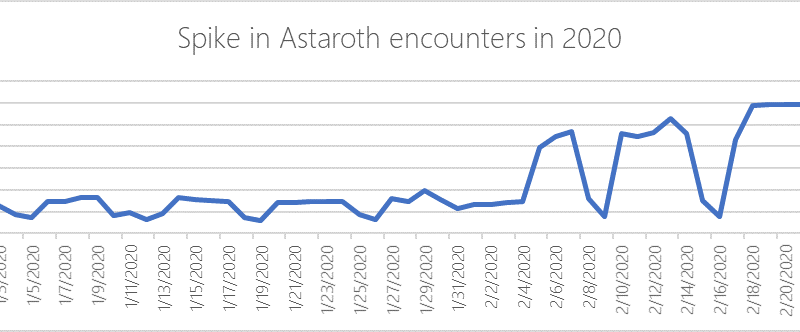
Security incidents don’t happen exclusively during business hours: attackers often wait until the late hours of the night to breach an environment.
The post How to gain 24/7 detection and response coverage with Microsoft Defender ATP appeared first on Microsoft Security. READ MORE HERE…