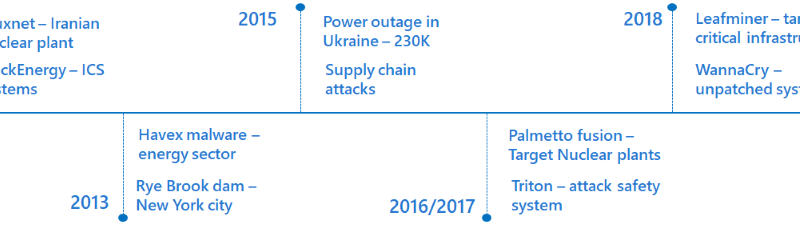
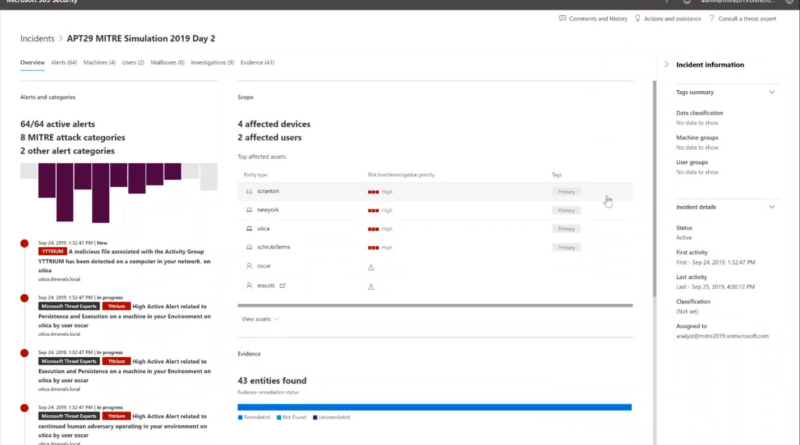
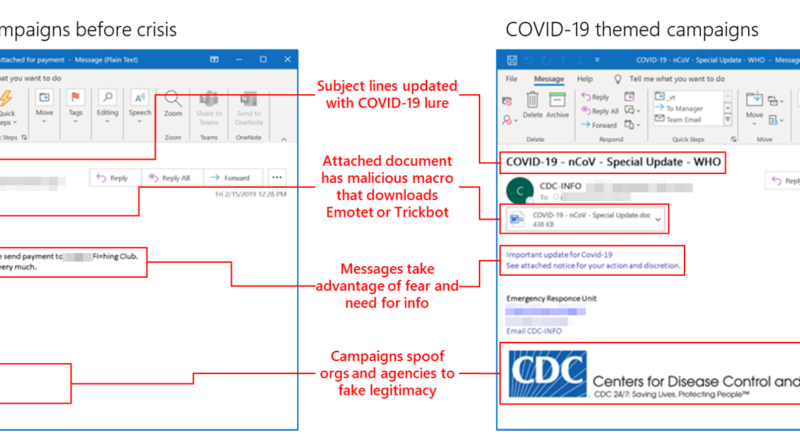
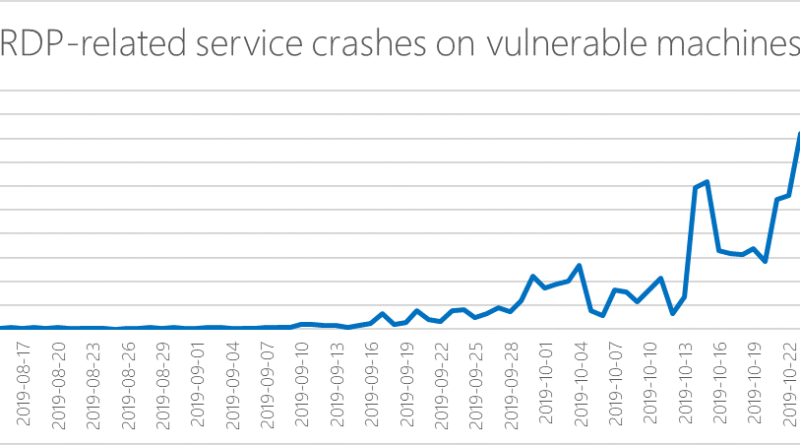
Defending the power grid against supply chain attacks: Part 3 – Risk management strategies for the utilities industry
By working with governments, trade organizations, and suppliers, the utility industry can improve security across the supply chain.
The post Defending the power grid against supply chain attacks: Part 3 – Risk management strategies for the utilities industry appeared first on Microsoft Security. READ MORE HERE…