Vulnerable SDK components lead to supply chain risks in IoT and OT environments
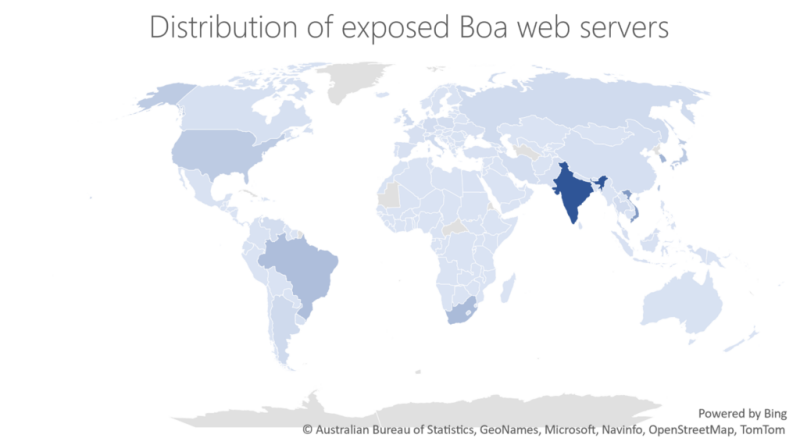
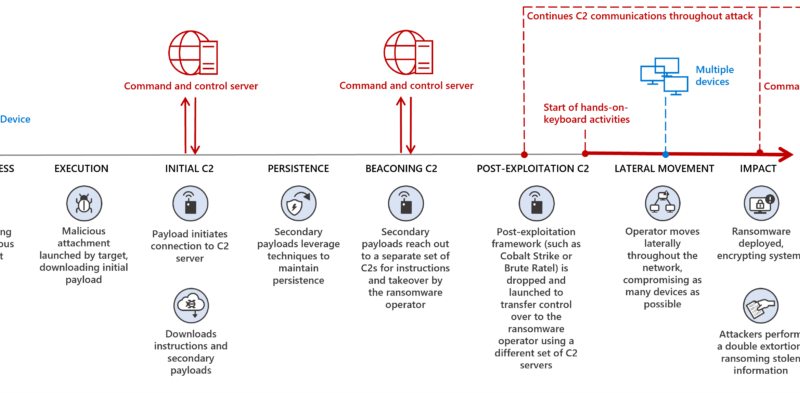
As vulnerabilities in network components, architecture files, and developer tools have become an increasingly popular attack vector to leverage access into secure networks and devices, Microsoft identified such a vulnerable component and found evidence of a supply chain risk that might affect millions of organizations and devices.
The post Vulnerable SDK components lead to supply chain risks in IoT and OT environments appeared first on Microsoft Security Blog. READ MORE HERE…