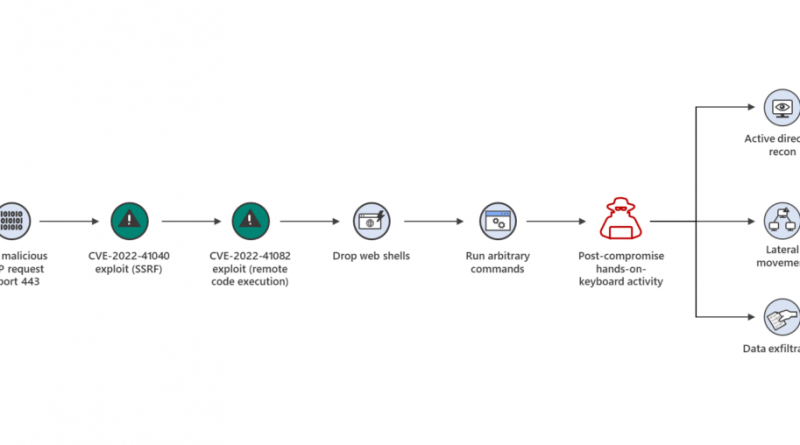
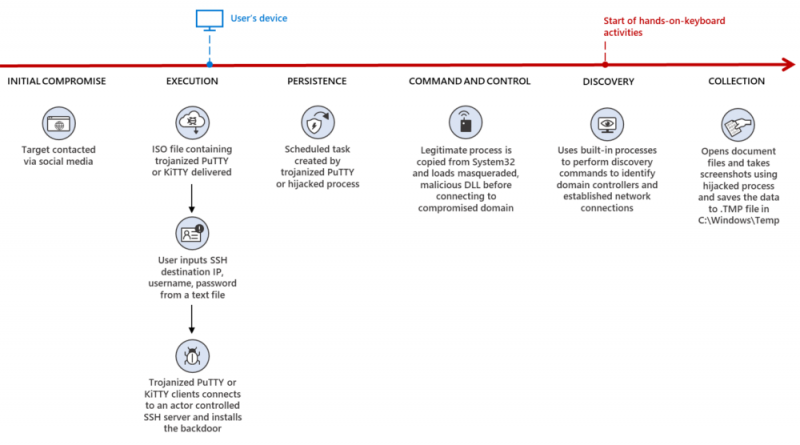
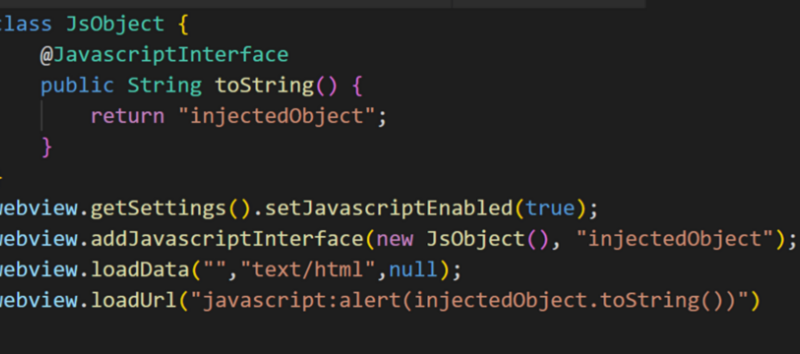
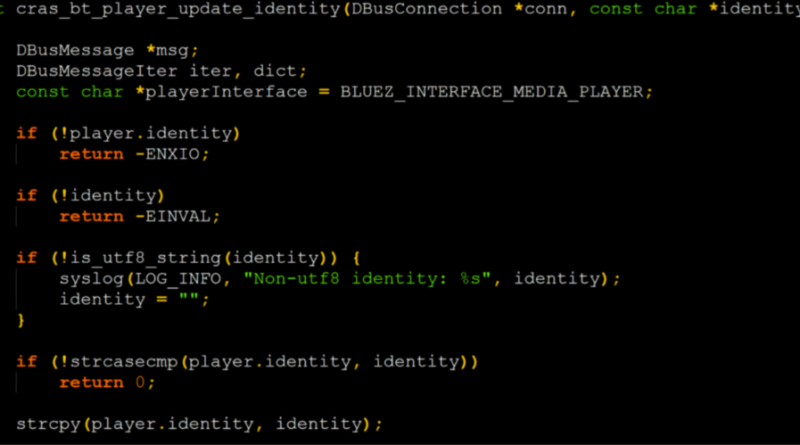
Cisco launches 10-year plan to train 25 million people in IT skills
As Cisco celebrates the 25th anniversary of Cisco Networking Academy, the company on Tuesday announced two new certifications and a plan to provide networking, cybersecurity and general IT training to 25 million people over the next 10 years.The training will be done through the company’s networking academy, an IT skills-to-jobs program that provides IT courses, learning simulators, and hands-on learning opportunities, supporting instructors and learners in 190 countries. To date, Cisco says more than 17.5 million global learners have taken Cisco Networking Academy courses to gain IT skills, with 95% of students attributing their post-course job or education opportunity to Cisco Networking Academy.To read this article in full, please click here READ MORE HERE…