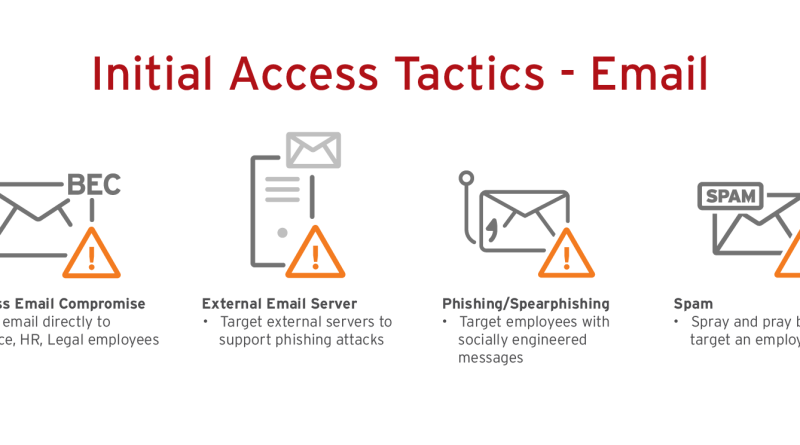
Security Culture Matters when IT is Decentralized
Decentralization can make enterprises more agile but it also makes IT and network security more complex. Creating a strong security culture, deploying the right tools, and defining an incident response plan are key to keeping the business protected. Read More HERE…