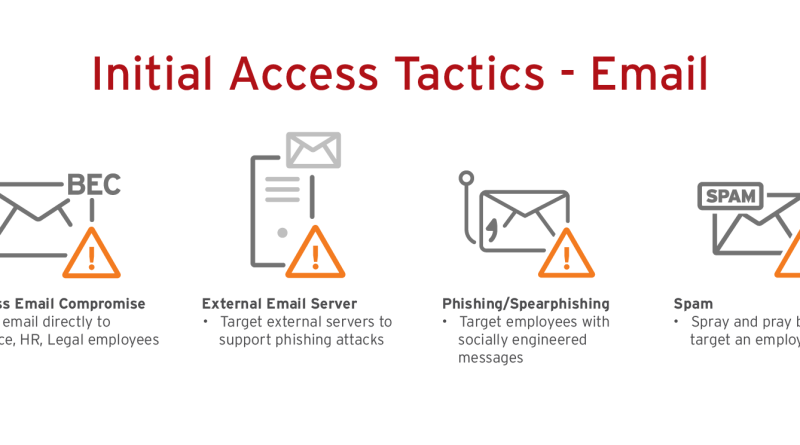
Email Security Best Practices for Phishing Prevention
Trend Micro Research reported a 137.6% growth in phishing attacks blocked and detected in 2021. Explore the latest phishing trends and email security best practices to enhance your email security and reduce cyber risk. Read More HERE…