Trend Micro Research : Cyber Threats
In Review: What GPT-3 Taught ChatGPT in a Year
Amidst the uproar and opinions since November 2022, we look at the possibilities and implications of what OpenAI’s ChatGPT presents to the cybersecurity industry using a comparison to earlier products, like its predecessor GPT-3. Read More HERE…
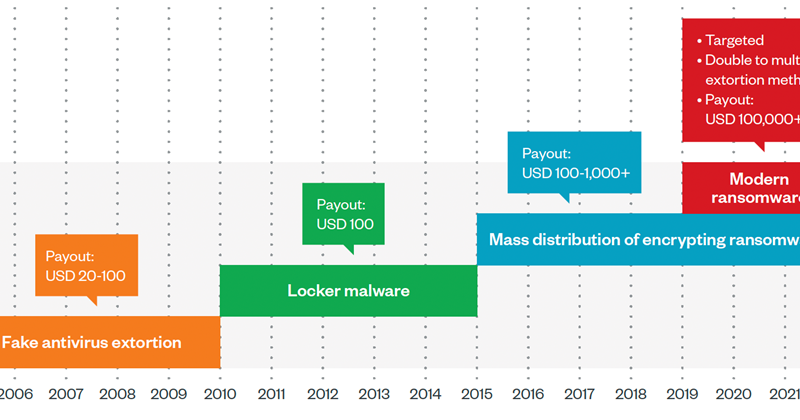
A Deep Dive into the Evolution of Ransomware Part 1
This 3-part blog series takes an in-depth look at the evolution of ransomware business models, from the early stages to current trends. Read More HERE…
Invitation to a Secret Event: Uncovering Earth Yako’s Campaigns
We detail the intrusion set Earth Yako, attributed to the campaign Operation RestyLink or EneLink. This analysis was presented in full at the JSAC 2023 in January 2023. Read More HERE…
TgToxic Malware’s Automated Framework Targets Southeast Asia Android Users
We look into an ongoing malware campaign we named TgToxic, targeting Android mobile users in Taiwan, Thailand, and Indonesia since July 2022. The malware steals users’ credentials and assets such as cryptocurrency from digital wallets, as well as money from bank and finance apps. Analyzing the automated features of the malware, we found that the threat actor abused legitimate test framework Easyclick to write a Javascript-based automation script for functions such as clicks and gestures. Read More HERE…
Attacking The Supply Chain: Developer
In this proof of concept, we look into one of several attack vectors that can be abused to attack the supply chain: targeting the developer. With a focus on the local integrated developer environment (IDE), this proof considers the execution of malicious build scripts via injecting commands when the project or build is incorrectly “trusted”. Read More HERE…
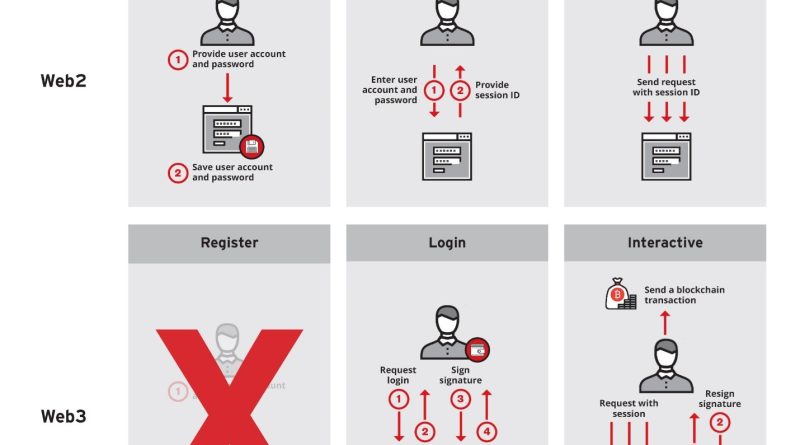
“Payzero” Scams and The Evolution of Asset Theft in Web3
In this entry, we discuss a Web3 fraud scenario where scammers target potential victims via fake smart contracts, and then take over their digital assets, such as NFT tokens, without paying. We named this scam “Payzero”. Read More HERE…