Water Labbu Abuses Malicious DApps to Steal Cryptocurrency
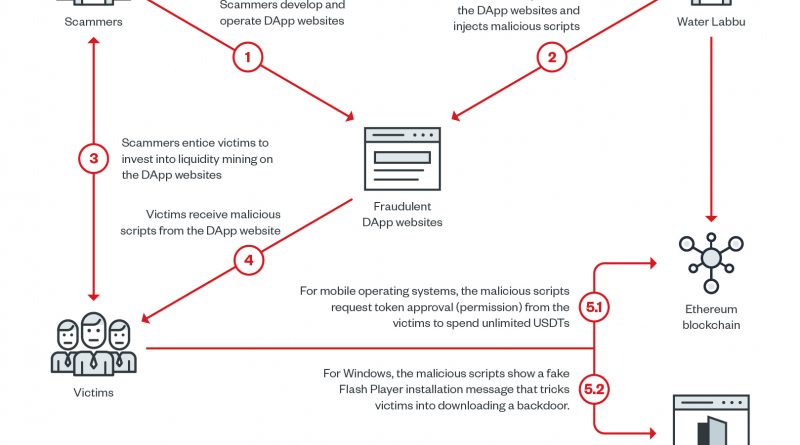
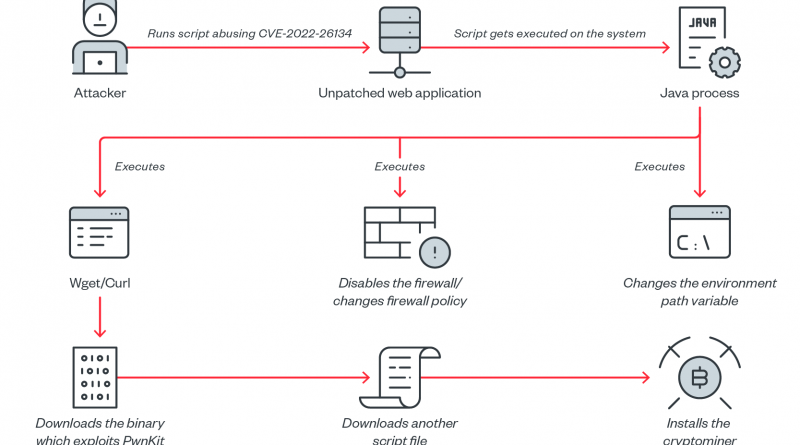
The parasitic Water Labbu capitalizes on the social engineering schemes of other scammers, injecting malicious JavaScript code into their malicious decentralized application websites to steal cryptocurrency. Read More HERE…