Iron Tiger’s SysUpdate Reappears, Adds Linux Targeting
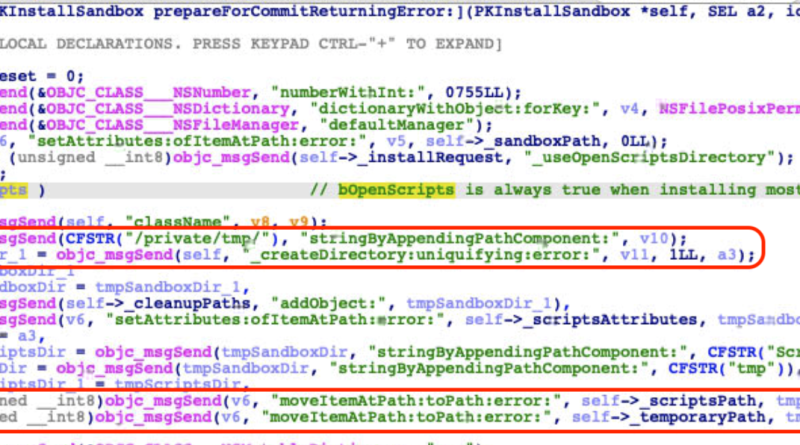
We detail the update that advanced persistent threat (APT) group Iron Tiger made on the custom malware family SysUpdate. In this version, we also found components that enable the malware to compromise Linux systems. Read More HERE…