Trend Micro Research : Exploits&Vulnerabilities
Threat Actors Target AWS EC2 Workloads to Steal Credentials
We found malicious samples attempting to steal Amazon Elastic Compute Cloud (EC2) Workloads’ access keys and tokens via typosquatting and the abuse of legitimate tools. Read More HERE…
How Underground Groups Use Stolen Identities and Deepfakes
The growing appearance of deepfake attacks is significantly reshaping the threat landscape. These fakes brings attacks such as business email compromise (BEC) and identity verification bypassing to new levels. Read More HERE…
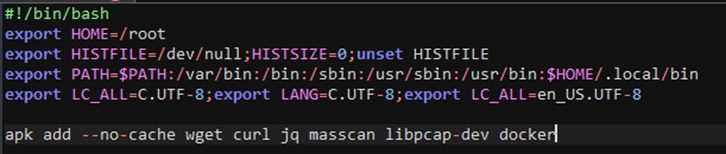
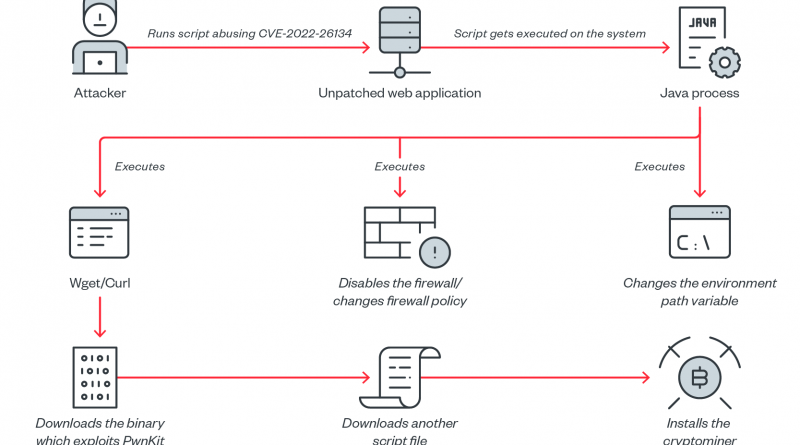
Atlassian Confluence Vulnerability CVE-2022-26134 Abused For Cryptocurrency Mining, Other Malware
Users are advised to patch immediately: We found exploit samples abusing the Atlassian Confluence vulnerability (CVE-2022-26134) in the wild for malicious cryptocurrency mining. Read More HERE…
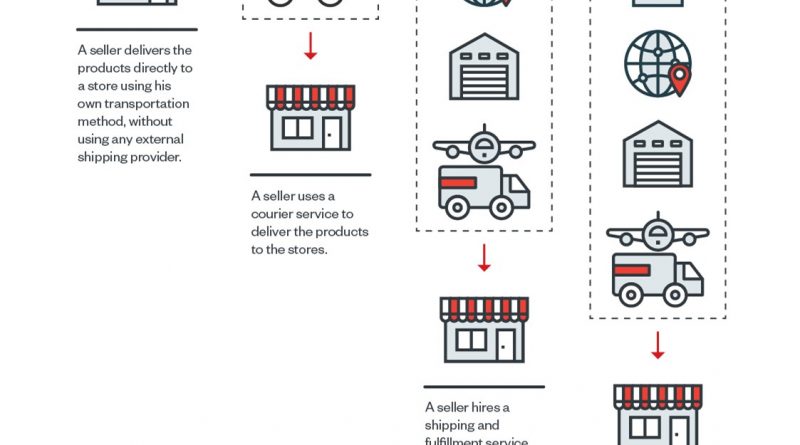
Security Risks in Logistics APIs Used by E-Commerce Platforms
Our research examines the security flaws that we found in the logistics API implementation of e-commerce platforms that can potentially expose the consumers’ personal information. We discuss the security risks that such flaws present for software engineers, e-commerce platform providers, and consumers. Read More HERE…
A Post-exploitation Look at Coinminers Abusing WebLogic Vulnerabilities
This blog entry details how Trend Micro Cloud One™ – Workload Security and Trend Micro Vision One™ effectively detected and blocked the abuse of the CVE-2020-14882 WebLogic vulnerability in affected endpoints. Read More HERE…
Ransomware Actor Abuses Genshin Impact Anti-Cheat Driver to Kill Antivirus
We investigate mhyprot2.sys, a vulnerable anti-cheat driver for the popular role-playing game Genshin Impact. The driver is currently being abused by a ransomware actor to kill antivirus processes and services for mass-deploying ransomware. Read More HERE…
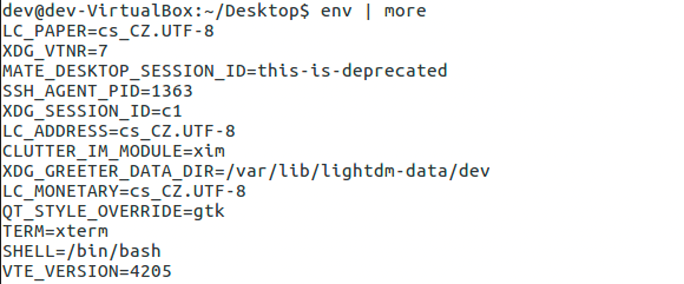
Analyzing the Hidden Danger of Environment Variables for Keeping Secrets
While DevOps practitioners use environment variables to regularly keep secrets in applications, these could be conveniently abused by cybercriminals for their malicious activities, as our analysis shows. Read More HERE…
Oil and Gas Cybersecurity: Industry Overview Part 1
With geopolitical tensions running high, oil and gas companies may be more susceptible to cyberattacks. Read More HERE…
Analyzing Penetration-Testing Tools That Threat Actors Use to Breach Systems and Steal Data
We discovered the use of two Python penetration-testing tools, Impacket and Responder, that malicious actors used to compromise systems and exfiltrate data. We share our key findings in this report. Read More HERE…