Trend Micro Research : Research
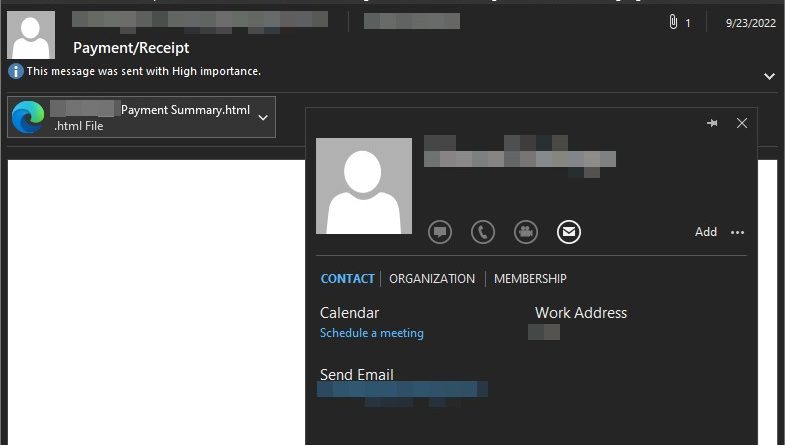
What SOCs Need to Know About Water Dybbuk, A BEC Actor Using Open-Source Toolkits
We analyze a BEC campaign targeting large companies around the world that was leveraging open-source tools to stay under the radar. Read More HERE…
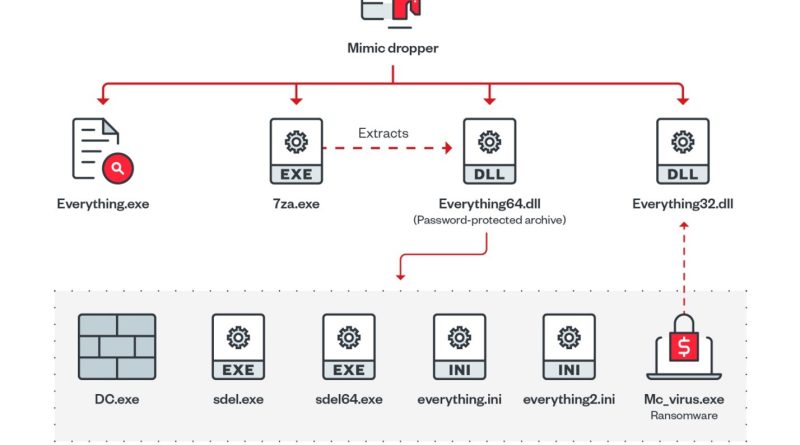
New Mimic Ransomware Abuses Everything APIs for its Encryption Process
Trend Micro researchers discovered a new ransomware that abuses the APIs of a legitimate tool called Everything, a Windows filename search engine developed by Voidtools that offers quick searching and real-time updates for minimal resource usage. Read More HERE…
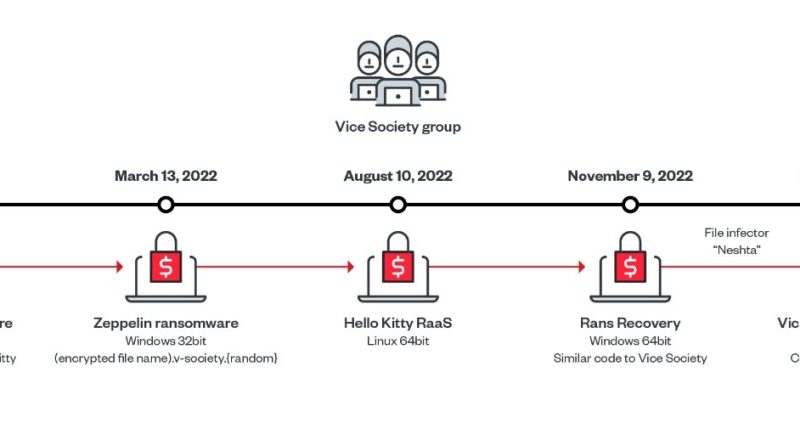
Vice Society Ransomware Group Targets Manufacturing Companies
In this blog entry, we’d like to highlight our findings on Vice Society, which includes an end-to-end infection diagram that we were able to create using Trend Micro internal telemetry. Read More HERE…
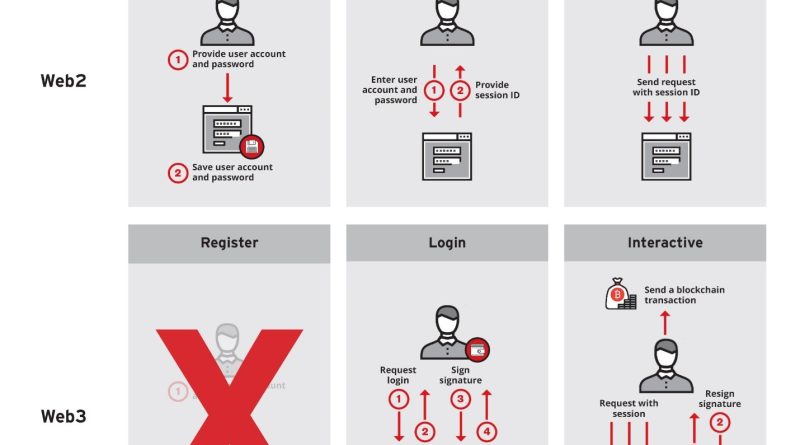
“Payzero” Scams and The Evolution of Asset Theft in Web3
In this entry, we discuss a Web3 fraud scenario where scammers target potential victims via fake smart contracts, and then take over their digital assets, such as NFT tokens, without paying. We named this scam “Payzero”. Read More HERE…
Batloader Malware Abuses Legitimate Tools, Uses Obfuscated JavaScript Files in Q4 2022 Attacks
We discuss the Batloader malware campaigns we observed in the last quarter of 2022, including our analysis of Water Minyades-related events (This is the intrusion set we track behind the creation of Batloader). Read More HERE…
Gootkit Loader Actively Targets Australian Healthcare Industry
We analyzed the infection routine used in recent Gootkit loader attacks on the Australian healthcare industry and found that Gootkit leveraged SEO poisoning for its initial access and abused legitimate tools like VLC Media Player. Read More HERE…
Dridex Returns, Targets MacOS Using New Entry Method
The Dridex variant we analyzed targets MacOS platforms with a new technique to deliver documents embedded with malicious macros to users. Read More HERE…
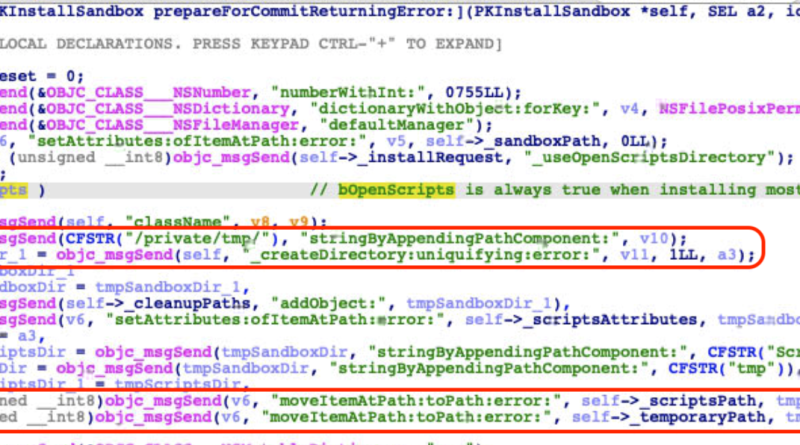
A Technical Analysis of CVE-2022-22583 and CVE-2022-32800
This blog entry discusses the technical details of how we exploited CVE-2022-22583 using a different method. We also tackle the technical details of CVE-2022-32800, another SIP-bypass that we discovered more recently, in this report. Read More HERE…
Diving into an Old Exploit Chain and Discovering 3 new SIP-Bypass Vulnerabilities
More than two years ago, a researcher, A2nkF demonstrated the exploit chain from root privilege escalation to SIP-Bypass up to arbitrary kernel extension loading. In this blog entry, we will discuss how we discovered 3 more vulnerabilities from the old exploit chain. Read More HERE…