Microsoft’s guidance to help mitigate Kerberoasting
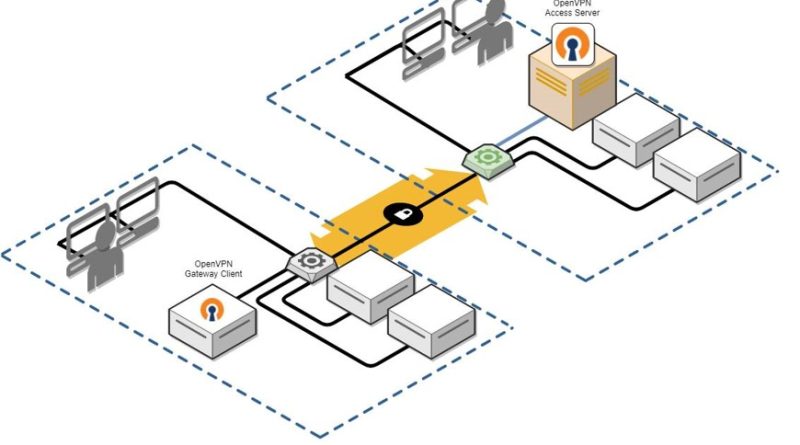
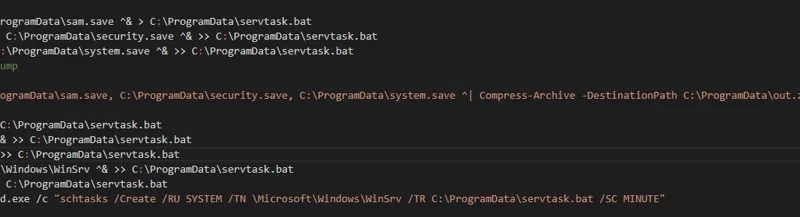
Kerberoasting, a well-known Active Directory (AD) attack vector, enables threat actors to steal credentials and navigate through devices and networks. Microsoft is sharing recommended actions administrators can take now to help prevent successful Kerberoasting cyberattacks.
The post Microsoft’s guidance to help mitigate Kerberoasting appeared first on Microsoft Security Blog. READ MORE HERE…