How companies are securing devices with Zero Trust practices
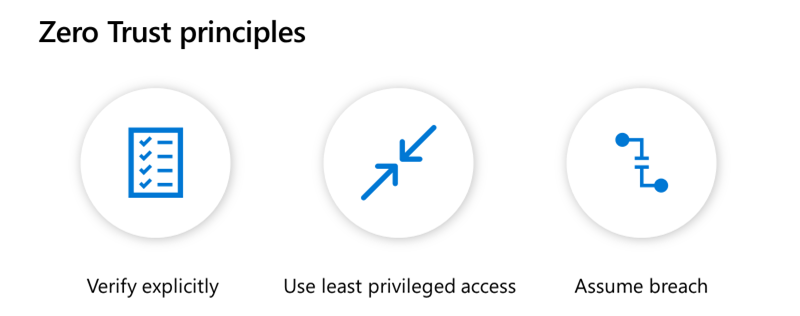
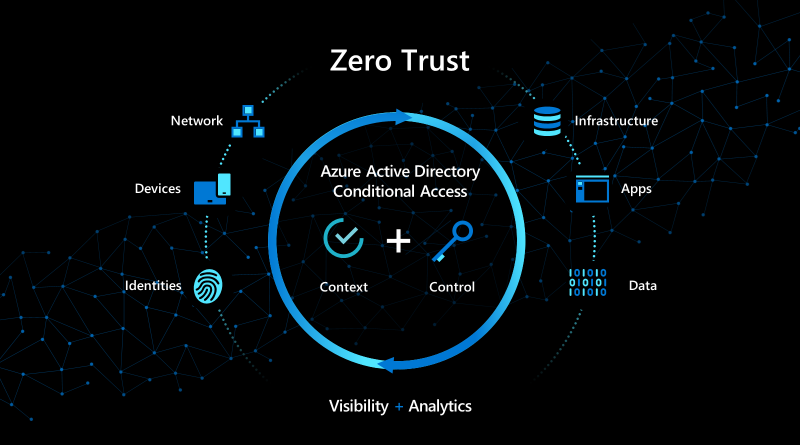
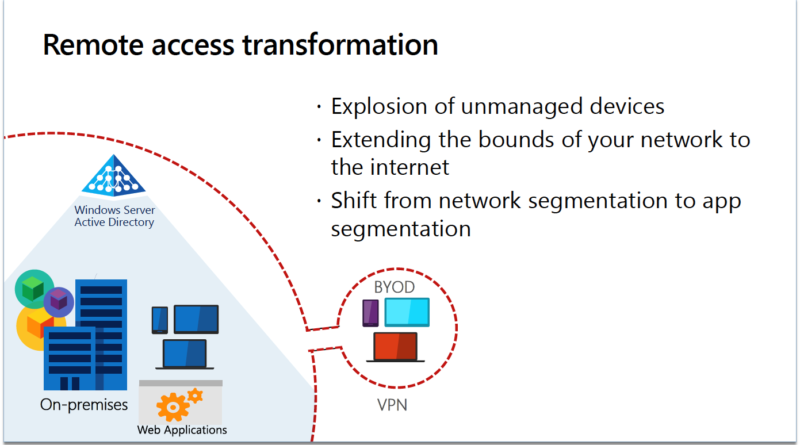
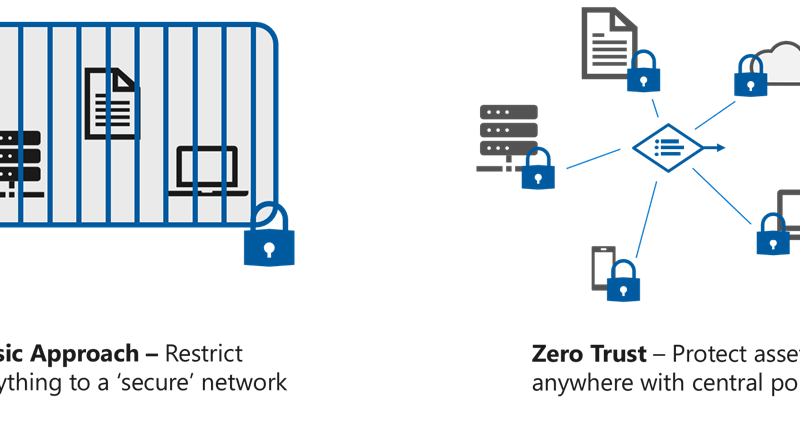
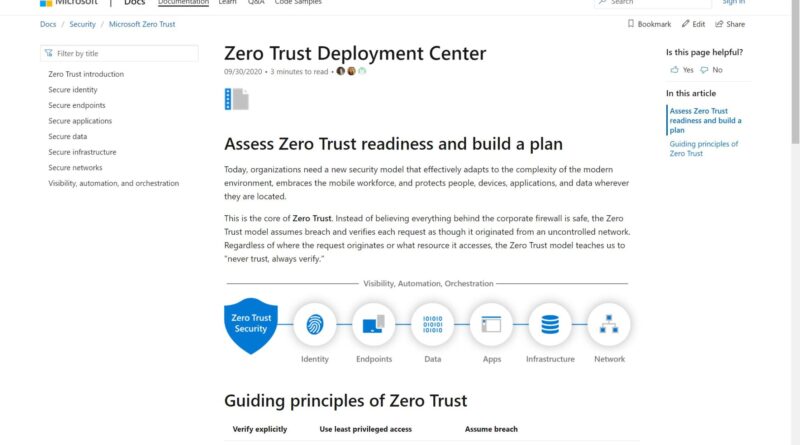
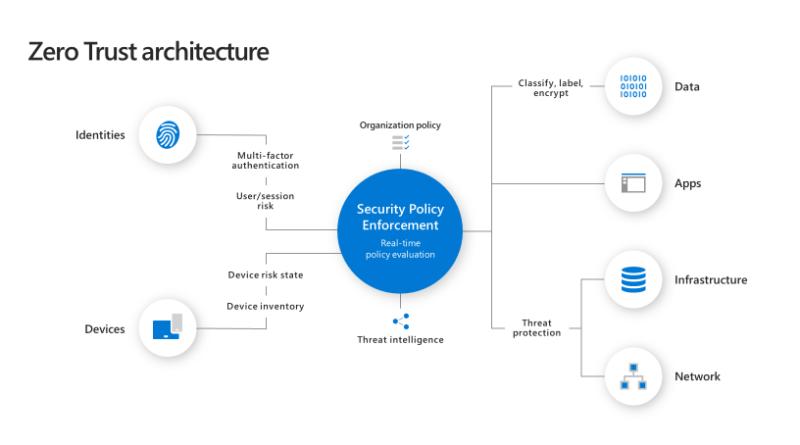
Organizations are seeing a substantial increase in the diversity of devices accessing their networks. With employees using personal devices and accessing corporate resources from new locations in record numbers, IT leaders are seeing an increase in their attack surface area. They’re turning to Zero Trust security models to ensure they have the visibility they need,…
The post How companies are securing devices with Zero Trust practices appeared first on Microsoft Security. READ MORE HERE…