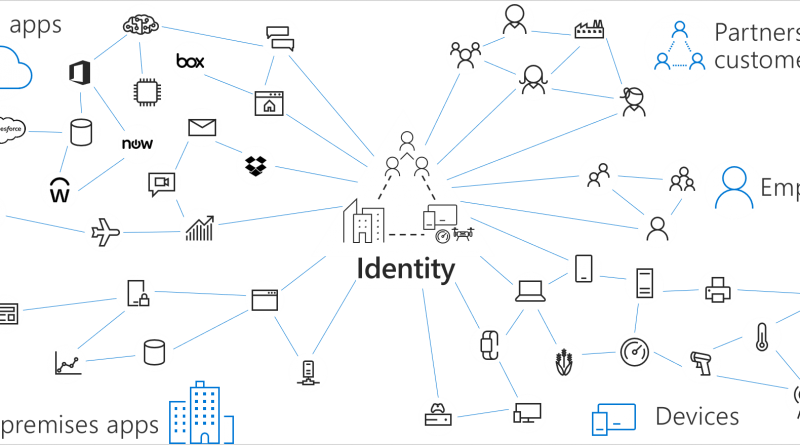
Further enhancing security from Microsoft, not just for Microsoft
Today, at the Microsoft Ignite Conference in Orlando, Florida, I’m thrilled to share the significant progress we’re making on delivering endpoint security from Microsoft, not just for Microsoft.
The post Further enhancing security from Microsoft, not just for Microsoft appeared first on Microsoft Security. READ MORE HERE…