TeamTNT Campaigns Emphasize Importance of Addressing Cloud Security Gaps Trend Micro

Cloud
Having covered TeamTNT in several of our blog entries over the past couple of years, we embarked on a research that encompasses the malicious actor group’s campaigns, tools, and techniques in 2020 and early 2021.
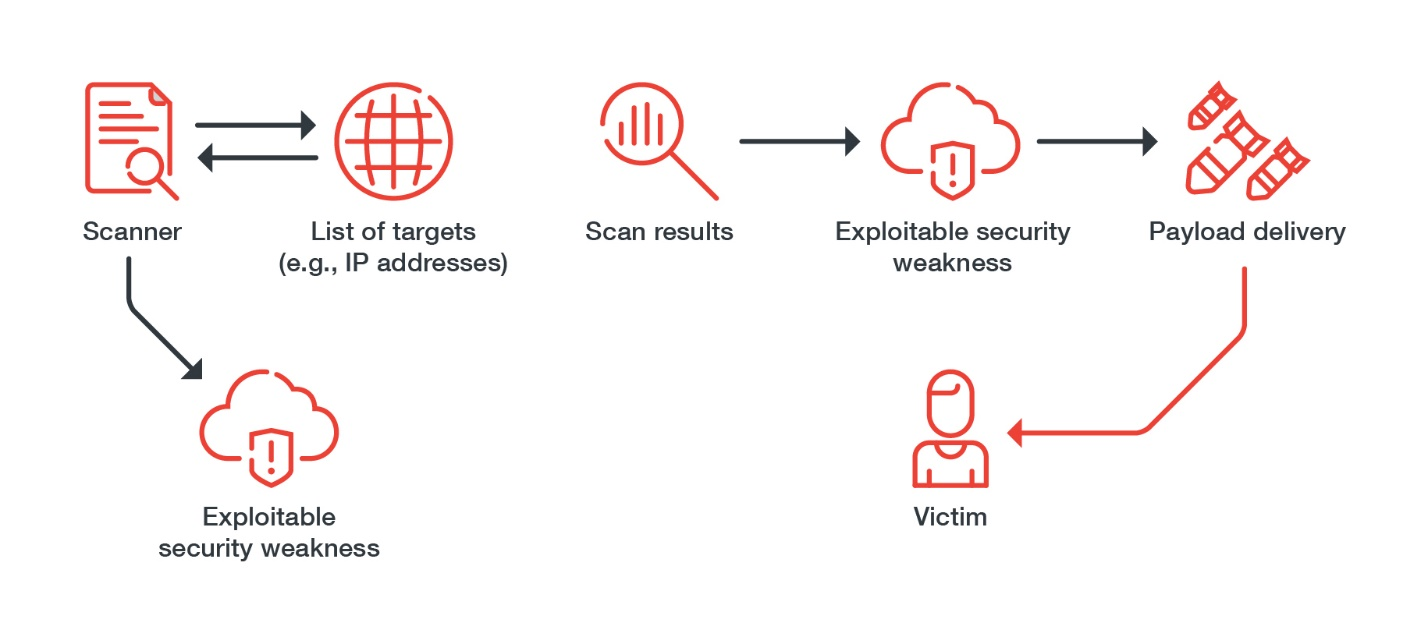
What makes TeamTNT particularly noteworthy is not only its targets — primarily cloud-based software and services — but also how quickly it has evolved existing techniques and integrated new ones into its campaigns.
Be that as it may, in most of the group’s campaigns, TeamTNT’s method of entry is more or less consistent: It uses a number of tools to scan the internet for potential targets with misconfigurations and vulnerabilities, and takes advantage of these weaknesses to gain a foothold in the systems. TeamTNT specializes in finding exploitable gaps in security, be they unsecured Redis instances, exposed Docker APIs, vulnerable internet-of-things (IoT) devices, or leaked credentials.
For a victim organization, the group’s payloads, if successfully deployed, could at best be disruptive — as with cryptocurrency miners — and at worst cause heavy monetary loss and even reputational damage — especially if the group manages to exfiltrate credentials and other sensitive information from the organization.
TeamTNT has largely been successful because of various exploitable security weaknesses. While it is admittedly difficult to completely eliminate these, enterprises need to prioritize security as much as they can. They should implement the most effective strategies for protecting the cloud from external attacks, while also being mindful of which aspects of the shared responsibility model they need to be accountable for.
Here are several best practices that organizations should consider putting into place:
- Grant users access only to the parts of the system they need in order to reduce possible entry points and contain damage even in the event of a successful attack. This is known as the principle of least privilege.
- Implement private keys authentication for Secure Shell (SSH) on the client side for stronger access control security.
- Regularly patch and update systems and devices to minimize instances of vulnerability exploitation. For organizations that need time to implement patches, virtual patching can provide buffer time, helping protect their systems from vulnerabilities while updates are still being prepared.
Enterprises should also consider using security solutions such as the Trend Micro Cloud One™ platform, which protects cloud-native systems by securing continuous-integration and continuous-delivery (CI/CD) pipelines and applications. The platform includes:
- Workload Security: runtime protection for workloads
- Container Security: automated container image and registry scanning
- File Storage Security: security for cloud files and object storage services
- Network Security: cloud network layer for intrusion prevention system (IPS) security
- Application Security: security for serverless functions, APIs, and applications
- Conformity: real-time security for cloud infrastructure — secure, optimize, comply
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE