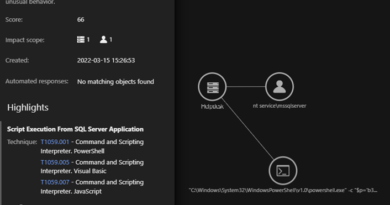
The Evolution of IoT Linux Malware Based on MITRE ATT&CK TTPs


New IoT botnet techniques
During the observation period, we noted four new techniques added to threat actors’ arsenals. One is a newly implemented technique in botnet families called Masquerading: Match Legitimate Name or Location (T1036.005). It is a Defense Evasion technique that likely reflect the manufacturers’ increasing interest and efforts in securing these IoT devices or appliances. The technique involves adversaries trying to match the name and location of legitimate and trusted programs to hide malicious executables and evade detection.
Another new technique that diverges from the more common technique being used in IoT Linux malware (Indicator Removal on Host: File Deletion (T1070.004) is File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification (T1222.002) introduced in a malware discovered in mid-2020. We observed these additions especially in the Dark Nexus malware. Most of the platforms provide two primary commands used to manipulate file and directory ACLs: chown (change owner) and chmod (change mode).
Furthermore, among the 2021 discovered families, is a variant of StealthWorker GO, a malware written in the Golang language, where we observed the addition of the Scheduled Task/Job: Cron (T1053.003) technique. This is an execution tactic which also allows malware to achieve persistence in the system. This software utility maintains persistence in the system by enabling an attacker to achieve time-based command execution.
Dropped techniques
On the other hand, we found three techniques relating to the lateral movement tactic to have been dropped. We observed a trend in recently discovered families that gives the responsibility for propagation back to the C&C server. In the Dark Nexus family, for example, we found that it is the C&C server that takes steps to propagate the malware. Our analysis highlighted the drop of two techniques linked to the Lateral Movement tactic, which are Remote Services (T1021) and Exploitation of Remote Services (T1210). In relation to this, the technique for the discovery of network information, System Network Configuration Discovery (T1016), is also no longer enforced.
Uncommon techniques
Additionally, we noticed that IoT Linux malware authors are not interested in stealing data. In our data set, there is only one malware (QSnatch) that implements typical tactics for data leakages, such as collection and exfiltration. Moreover, we also found that privilege escalation is not among the interests of IoT malware authors. It is likely because, from a malware author’s standpoint, the benefits of executing malware that require higher privileges are not worth the effort of implementation. Furthermore, the default accounts on targeted devices usually already come with all the privileges needed to run programs, write to the filesystem, and establish new connections.
Differences between ransomware and botnet malware
The characterization through the ATT&CK matrix also allowed us to compare different malware classes that target IoT devices which in our data set are ransomware and botnet families.
The findings highlight some common techniques, such as the Credential Access methodology where Brute Force: Password Guessing (T1110.001) is the most common technique that both malware classes fall under. This finding is not a surprise since it is common to find default usernames and passwords still being used in these kinds of devices. Usually, users are not aware of the risks of exposing IoT devices to the internet. Indeed, many devices are still installed without changing the default credentials or securing remote access.
Another common capability for both classes is External Remote Services (T1133) from the Initial Access Tactic, which confirms unsecured and exposed internet services, such as Telnet and SSH. This technique allows attackers to exploit external-facing remote services to initially access and/or persist within a network; they also often use exposed services that do not require authentication.
Another similarity is in the two classes’ Command and Control implementation, as both implement Application Layer Protocol: Web protocol (T1071.001). This is likely because the market for malware-as-a-service is growing. Thus, having a simple UI that the “customers” or other threat actors can use to control the malware is an important aspect.
By comparing the number of unique TTPs implemented, we studied the implementation variations among different malware families and noticed that while different ransomware families share many common techniques, botnets tend to innovate more and implement a variety of different TTPs to exploit many services. This may be because detection of botnet malware is more mature, so they require more frequent changes to avoid being easily detected. These differences are illustrated in Figure 2.
Read More HERE