The FBI Created A Fake FedEx Website To Unmask A Cybercriminal
The FBI has started deploying its own hacking techniques to identify financially-driven cybercriminals, according to court documents unearthed by Motherboard. The news signals an expansion of the FBI’s use of tools usually reserved for cases such as child pornography and bomb threats. But it also ushers in a potential normalization of this technologically-driven approach, as criminal suspects continually cover up their digital trail and law enforcement have to turn to more novel solutions.
The two 2017 search warrant applications discovered by Motherboard both deal with a scam where cybercriminals trick a victim company into sending a large amount of funds to the scammers, who are pretending to be someone the company can trust. The search warrants show that, in an attempt to catch these cybercriminals, the FBI set up a fake FedEx website in one case and also created rigged Word documents, both of which were designed reveal the IP address of the fraudsters. The cases were unsealed in October.
“What kinds of criminals mask their location, and for what kinds of crimes? Child pornography, yes; violent threats, yes; but also organized-crime rings engaged in cybercrime. A business email compromise scam, like those at issue in these warrants, falls squarely in that camp,” Riana Pfefferkorn, associate director of surveillance and cybersecurity at the Stanford Center for Internet and Society, told Motherboard in an online chat after reviewing the documents.
Got a tip? You can contact Joseph Cox securely on Signal on +44 20 8133 5190, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
The first case centers around Gorbel, a cranes and ergonomic lifting manufacturing company headquartered in Fishers, New York, according to court records. Here, the cybercriminals used a long, potentially confusing and official looking email address to pose as the company’s CEO Brian Reh, and emailed the accounts team asking for payment for a new vendor. The fraudsters provided a W9 form of a particular company, and the finance department mailed a check for over $82,000. Gorbel noticed the fraudulent transaction, and brought in the FBI in July. Shortly after, Gorbel received other emails pretending to be Reh, asking for another transfer. This time, the finance department and FBI were ready.
The FBI created a fake FedEx website and sent that to the target, in the hope it would capture the hacker’s IP address, according to court records. The FBI even concocted a fake “Access Denied, This website does not allow proxy connections” page in order to entice the cybercriminal to connect from an identifiable address. (GoDaddy has since repossessed the domain, and the domain did briefly resolve to an IP address in Rochester, New York, where the FBI Special Agent writing the application is based, according to online records).
It is not clear if the FBI sought permission from FedEx to digitally impersonate the company. FedEx did not respond to a request for comment, and the FBI did not provide a response to questions around the specific incident.
Notably, only one other domain has previously resolved to the same IP address as the fake FedEx page; a domain that eludes to a law firm. The site only existed for a short time, is offline at the time of writing, and seems to have a very small digital fingerprint. It appears this law firm domain may also be connected to the FBI.

Caption: A section of one of the warrant applications describing the fake FedEx website. Image: Motherboard.
That FedEx unmasking attempt was not successful, it seems—the cybercriminal checked the link from six different IP addresses, some including proxies—and the FBI moved on to use a network investigative technique, or NIT, instead. NIT is an umbrella term the FBI uses for a variety of hacking approaches. Previous cases have used a Tor Browser exploit to break into a target’s computer and force it to connect to an FBI server, revealing the target’s real IP address. Other NITs have been somewhat less technically sophisticated, and included booby-trapped video or Word files that once opened also ‘phone home’ to the FBI.
This new NIT falls into that latter category. The FBI attempted to locate the cybercriminals with a Word document containing an image that would connect to the FBI server and reveal the target’s IP address, according to court records. The image was a screenshot of a FedEx tracking portal for a sent payment, the court records add.
In the second case found by Motherboard, in August 2017, a business in the Western District of New York received an email claiming to be from Invermar, a Chilean seafood vendor and one of the company’s suppliers, according to court records. This email, posing as a known employee of Invermar, asked the victim to send funds to a new bank account. Whereas the legitimate Invermar domain ends with a .cl suffix, the hackers used one ending in .us. The business the hackers targeted apparently didn’t notice the different suffix, and over the course of September and October wire transferred around $1.2 million to the cybercriminals, with the victim eventually able to recover $300,000 (the court documents don’t specify how exactly, although a charge back seems likely).
The court documents do not name the victim company, but earlier this year Wegmans Food Market filed a lawsuit against Invermar for a similar scam, claimed similar damages, and the suit was filed in the same district as the FBI office writing the warrant application found by Motherboard.
To determine where this criminal was located, the FBI also decided to deploy a NIT.
“The FBI will provide an email attachment to the victim which will be used to pose as a form to be filled out by the TARGET USER for future payment from the VICTIM,” one court record reads. The NIT required the target to exit “protected mode,” a setting in Microsoft Word that stops documents from connecting to the internet. The warrant application says the government does not believe it needs a warrant to send a target an embedded image, but out of an abundance of caution, added to the fact that the target will need to deliberately exit protected mode, the FBI applied for one anyway.
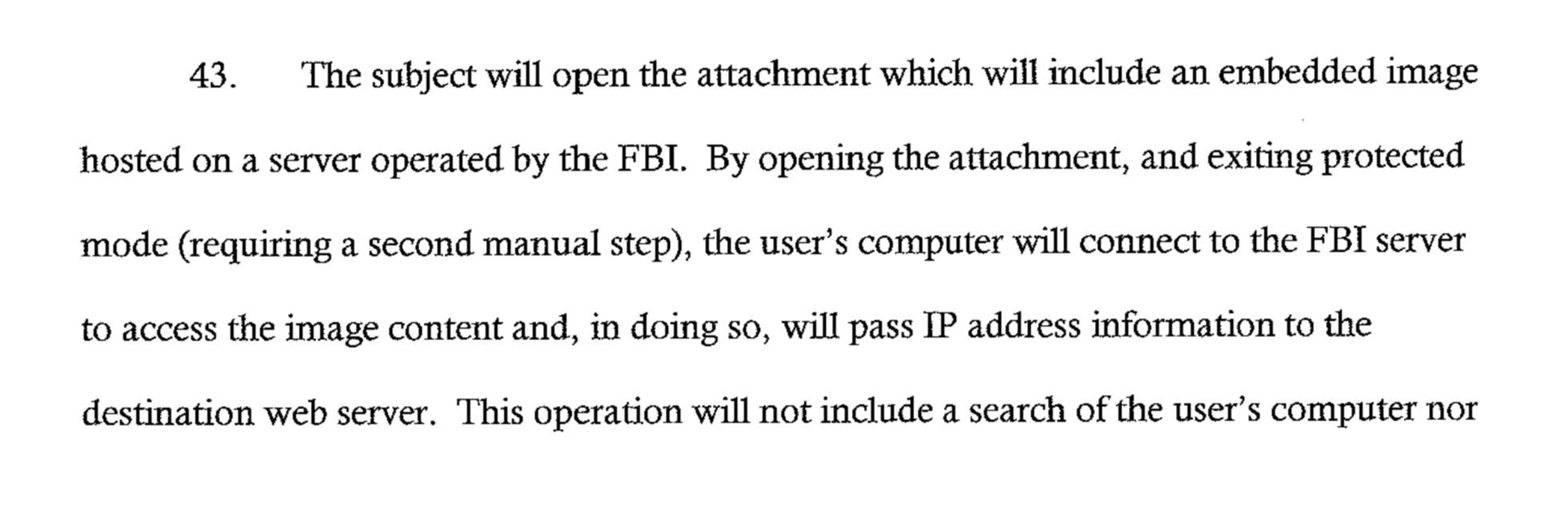
Caption: A section of one of the warrant applications explaining that the target will need to disable protected mode for the NIT to function. Image: Motherboard.
Both NITs were designed to only obtain a target’s IP address and User Agent String, according to the warrant applications. A User Agent String can reveal what operating system a target is using. Although signed by two different FBI Special Agents, both of the NIT warrant applications come out of the Cyber Squad, Buffalo Division, in Rochester, New York.
We don’t know how successful either of these NITs were in identifying the suspects. In the Gorbel case, the Justice Department asked for multiple extensions to keep the search warrant application sealed, right up to at least March of this year. Both warrants were returned as executed, according to court records.
“The use of a Network Investigative Technique is lawful and effective,” an FBI spokesperson told Motherboard in an email. “They are only employed when necessary, against some of the worst offenders. The technique is time and resource intensive and is not a viable option for most investigations.”
Previously, the FBI has deployed NITs on a large, and sometimes indiscriminate scale. When the Bureau targeted dark web hosting provider Freedom Hosting, its NIT also impacted users of a privacy-focused email service not suspected of a crime. In these new warrant applications the FBI emphasises that only the intended target should encounter the NIT.
“The FBI anticipates the target user, and only the target user, will receive the email and attachment after logging in and checking emails,” one of the applications reads. “The general public will be protected from any violation of privacy through careful and direct deployment of the NIT to the specific target email,” another document adds.
Pfefferkorn, the cybersecurity and surveillance expert, said “This shows that the government has learned from the Freedom Hosting case, where the NIT deployed from a website the government had taken over was not carefully targeted enough and ended up infecting the browsers of innocent people.”
This sort of law enforcement hacking is likely to become more common. At the end of 2016, the Justice Department amended Rule 41, one of the rules around search warrants. The change meant that US judges could sign warrants to search computers outside of their district, and in particular, if law enforcement did not know where the suspect was ultimately located—exactly the issue with these two cases.
“Now that Rule 41 has been amended, we can expect to see NIT warrants being used in the investigation of a range of crimes, not just the child pornography Tor Hidden Service busts that pre-dated the amendment,” Pfefferkorn said.
Subscribe to our new cybersecurity podcast, CYBER.
READ MORE HERE
