The Underground Exploit Market and the Importance of Virtual Patching Trend Micro

Exploits & Vulnerabilities
Over the past two calendar years, we conducted research on the underground exploit market to learn more about the life cycle of exploits, the kinds of buyers and sellers who transact, and the business models that are in effect in the underground.
Over the past two calendar years, we conducted research on the underground exploit market to learn more about the life cycle of exploits, the kinds of buyers and sellers who transact, and the business models that are in effect in the underground. We detail our findings in our research paper “The Rise and Imminent Fall of the N-Day Exploit Market in the Cybercriminal Underground.”
In this blog entry, we discuss several of our findings and recommend a security solution that can help organizations defend their systems against exploits by affording them time to properly implement patches.
Exploits for zero-day or unpatched vulnerabilities can be a cause of great distress for many organizations. They’re difficult to detect and, without patches addressing the exploited vulnerabilities, well nigh impossible to thwart under normal circumstances. It’s not surprising, then, that such exploits fetch very high prices in the underground — typically exceeding US$10,000 for a working zero-day exploit.
Once a vulnerability is discovered, and especially once an exploit for it is developed, the vendor of the affected product finds itself in a race for time to issue a security patch. Once a patch is released, the value of the exploit, which is now an N-day exploit, drops drastically, and its price is likely to be reduced by half or more in just a few months.
An example is the exploit for the Zyxel network-attached storage (NAS) vulnerability CVE-2020-9054. Initially sold on a Russian-language underground forum for US$20,000 in February 2020, it was advertised as an N-day exploit the following May for US$10,000. By August, at least one request for the exploit offered up to US$2,000.
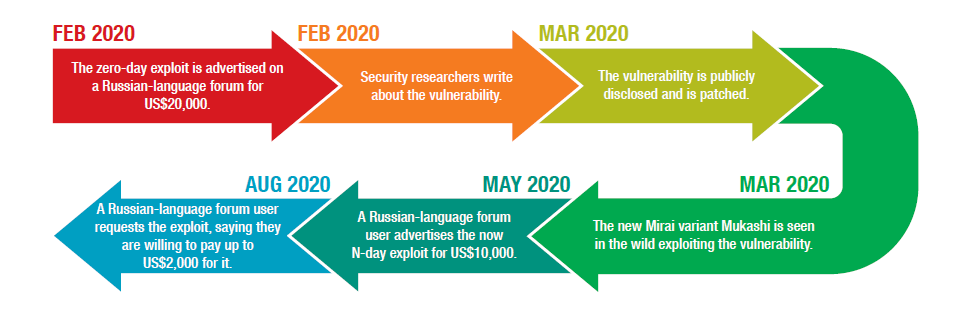
It’s but natural for an exploit to lose value over time: The longer the patch for the exploited vulnerability has been out, the larger the number of affected users who have updated their machines becomes. However, this does not mean that exploits are rendered useless past a certain window. Given that not all organizations and individual users are able — or even willing — to patch their systems, old exploits continue to be used by malicious actors. Often such exploits are bundled together as a package to make them more enticing to potential buyers, who can then choose which exploits to use depending on their needs.
Unsurprisingly, popular software products figure prominently in the most requested and sold exploits in the underground. Exploits for Microsoft products, in particular, had the lion’s share of the market in our findings, with Microsoft Office, Microsoft Windows, Microsoft Remote Desktop Protocol (RDP), Internet Explorer, and Microsoft SharePoint accounting for at least 47% of requests and at least 51% of sales. The combination alone of Microsoft Word and Microsoft Excel, two of the most widely used office applications in the world, made up 46% of Microsoft-related exploits requested and 52% of Microsoft-related exploits sold.

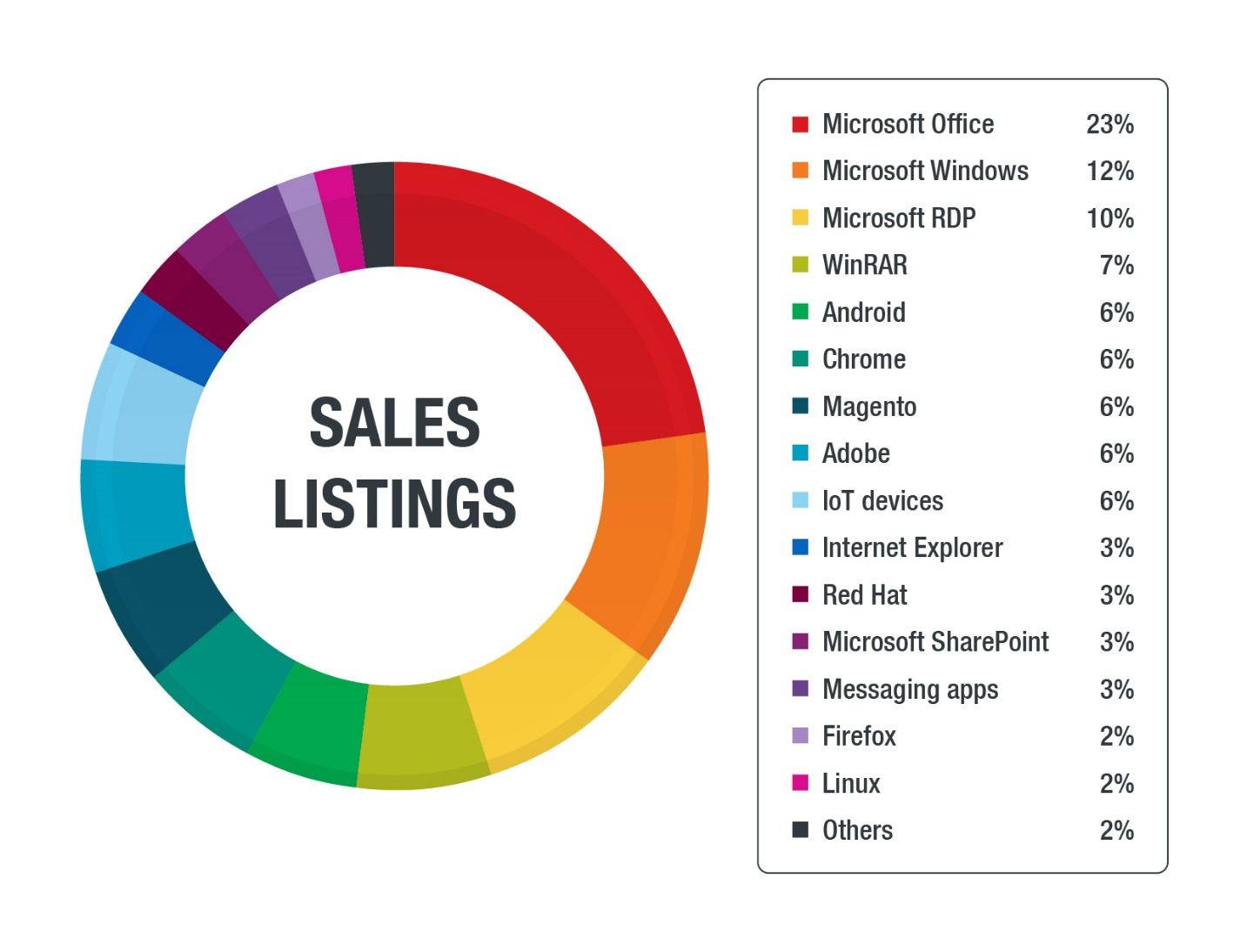
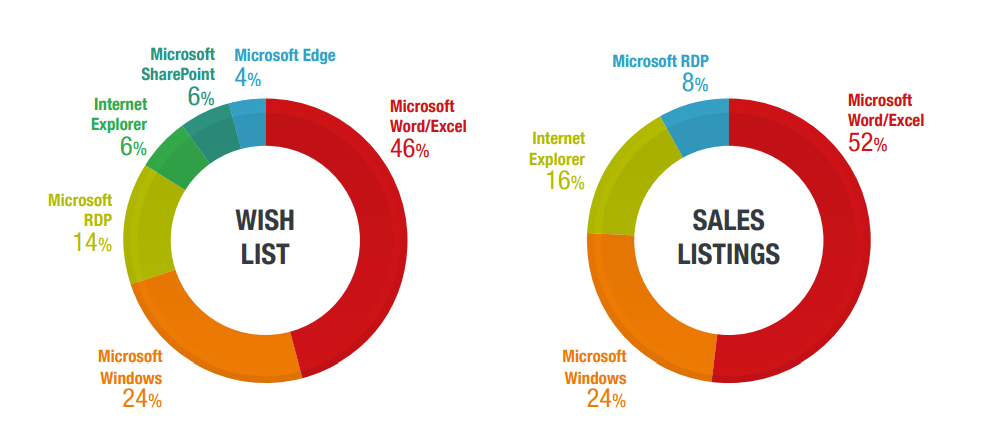
Notably, exploits for internet-of-things (IoT) devices made up only 5% of requests and 6% of sales. However, considering the increasing number of IoT devices — and the relative difficulty of patching them — we can only expect these numbers to go up.
In an ideal world, organizations would be able to apply security updates as soon as they become available, minimizing the attack surface that malicious actors could use to compromise systems. But this is rarely the case in real-world scenarios, where patching often takes plenty of time and resources — especially for large organizations, companies that have decentralized systems, and enterprises that use customized versions of stock software.
Fortunately, certain security technologies have the ability to apply virtual patching. Adding an additional security measure against threats that exploit vulnerabilities, virtual patching is the implementation of security policies and rules that prevent exploits from being able to take network paths to and from a vulnerability.
Virtual patching offers a number of advantages, such as reducing the downtime needed to roll out patching and providing flexibility in patch management. But perhaps the most important benefit of virtual patching is that it buys additional time for an organization to assess vulnerabilities and apply the necessary patches.
For the full details of our findings on the underground exploit market and more information on virtual patching, read our research paper “The Rise and Imminent Fall of the N-Day Exploit Market in the Cybercriminal Underground.”
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE


