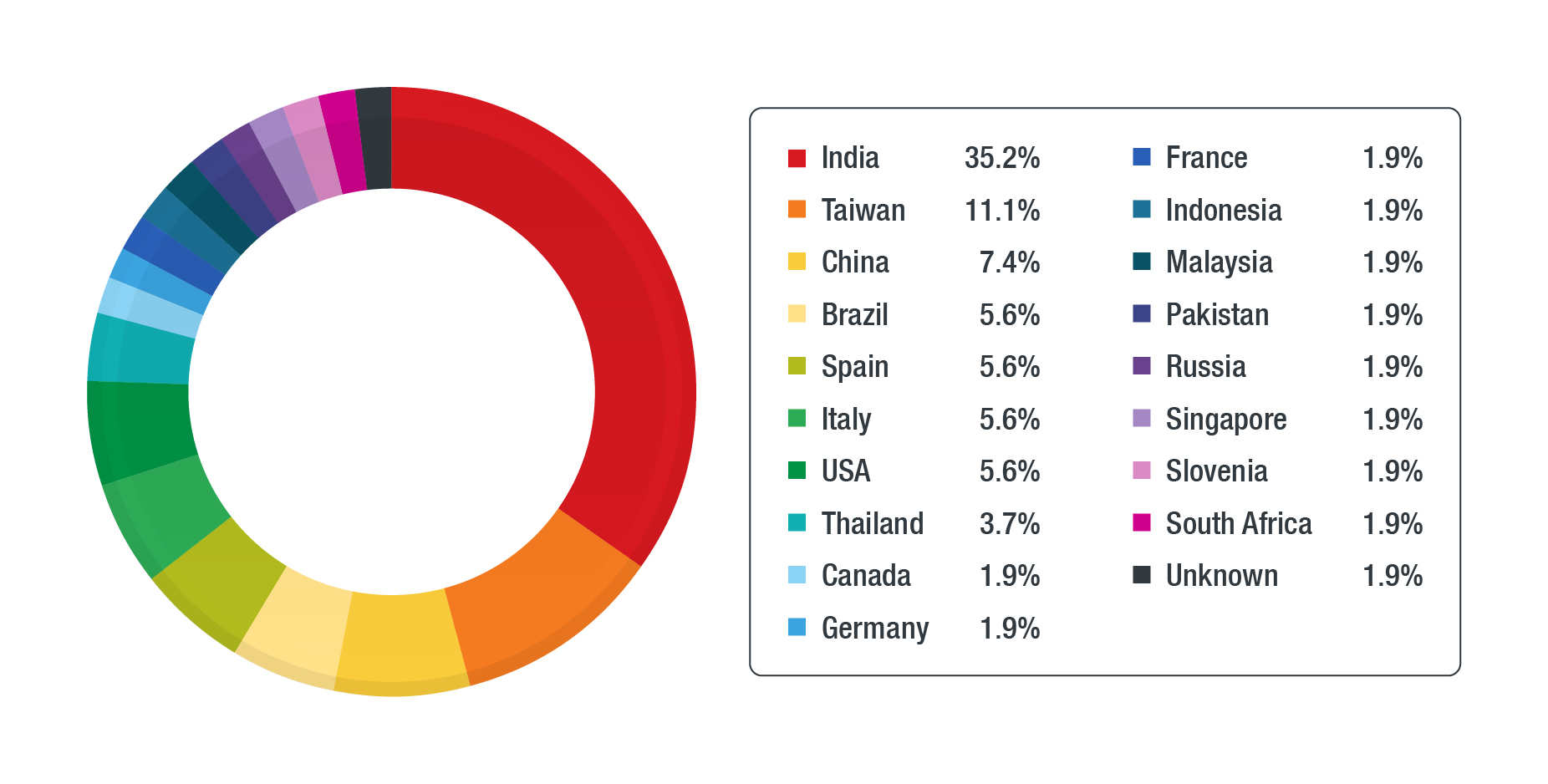
Top Countries With ICS Endpoint Malware Detections Sr. Security Specialist Sr. Manager, Threat Research Sr. Threat Researcher Sr. Threat Researcher

Smart Factories
The Trend Micro research paper, “2020 Report on Threats Affecting ICS Endpoints,” presents findings on ICS endpoints and the threats that plague them. From these findings, we rounded up the list of the top ten countries with the most malware and grayware detections.

The ever-increasing interconnection between IT and OT in Industrial Control Systems (ICS) promotes efficiency but also makes it susceptible to threats. Organizations should examine possible security issues to prevent compromise.
The Trend Micro research paper, “2020 Report on Threats Affecting ICS Endpoints,” presents findings on ICS endpoints and the threats — such as ransomware, coinminers, and legacy malware — that plague them. From these findings, we rounded up the list of the top ten countries with the most malware and grayware (like potentially unwanted applications, adware, and hacking tools) detections.
The top 10 countries with the most ICS malware infections
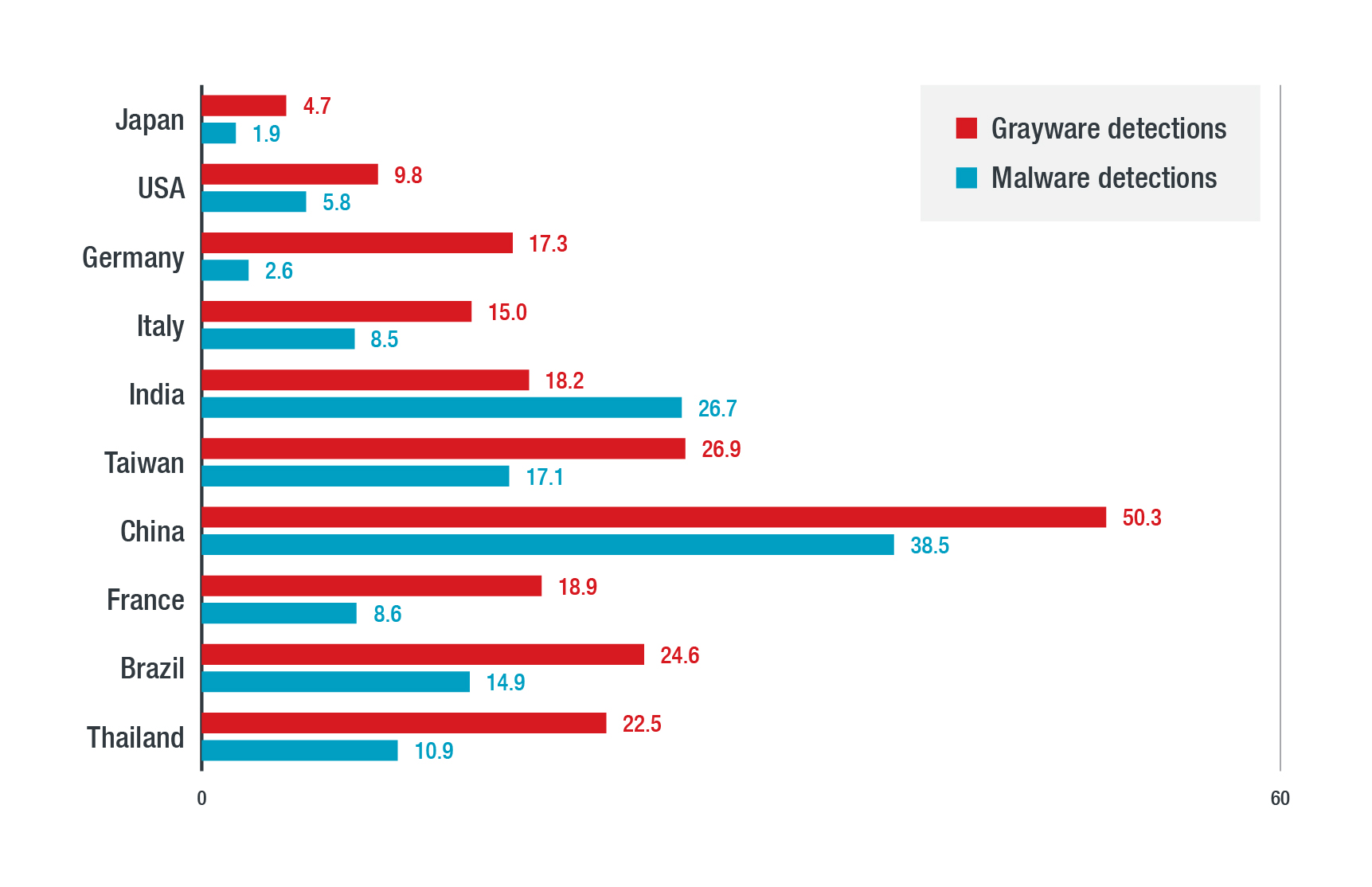
The list includes the following countries: Japan, US, Denmark, Italy, India, Taiwan, China, France, Brazil, and Thailand.
Here are some pertinent findings on specific types of threats:
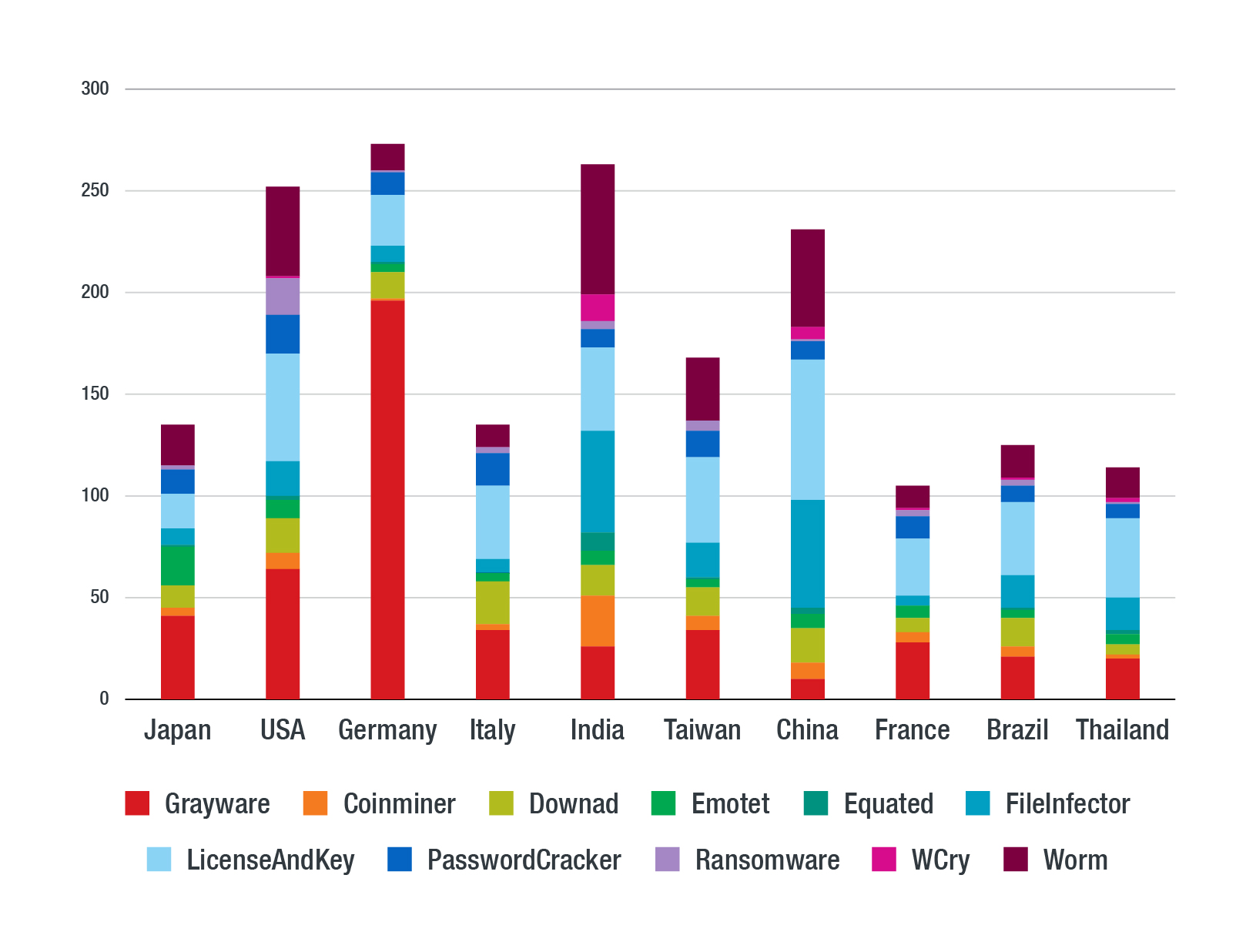
- The US had the greatest number of organizations affected by ransomware.
- India has the most of the coinminer, Equated malware, and WannaCry ransomware detections.
- Legacy malware (particularly worms in removable drives and file infecting viruses) infections were mostly detected in India, China, the US, and Taiwan.
- Japan has the highest number of Emotet infections. However, while Emotet is known to deploy other malware such as Ryuk, Trickbot, or Qakbot post-infection, the data seems to show no further installation of malware.
- ICSs in Germany has the most grayware, primarily because of adware bundled with software tools.
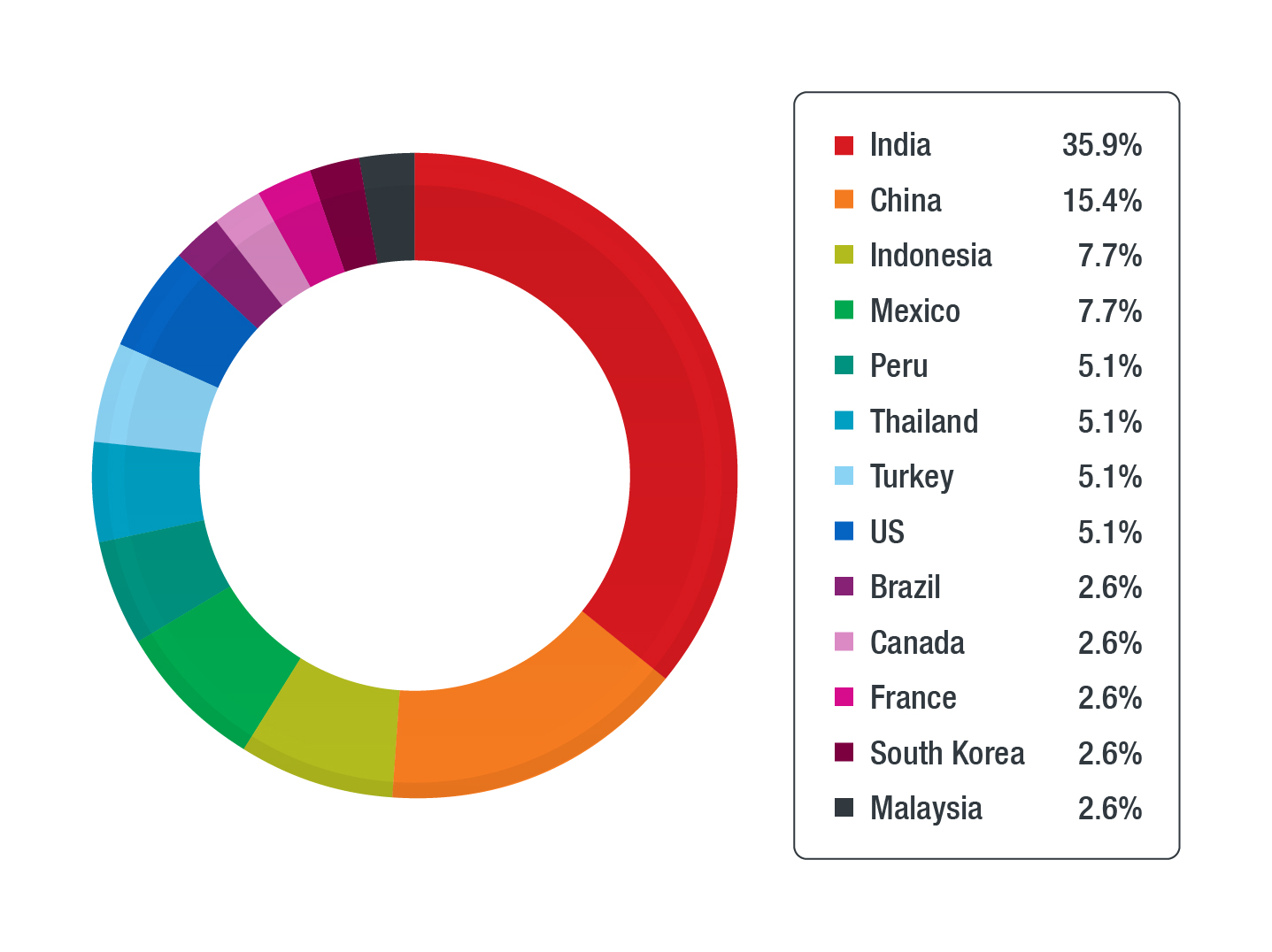
In terms of organizations that have ICSs that have been infected with ransomware, the US has the most ransomware detections affecting ICS, followed by India, Taiwan, and Spain.
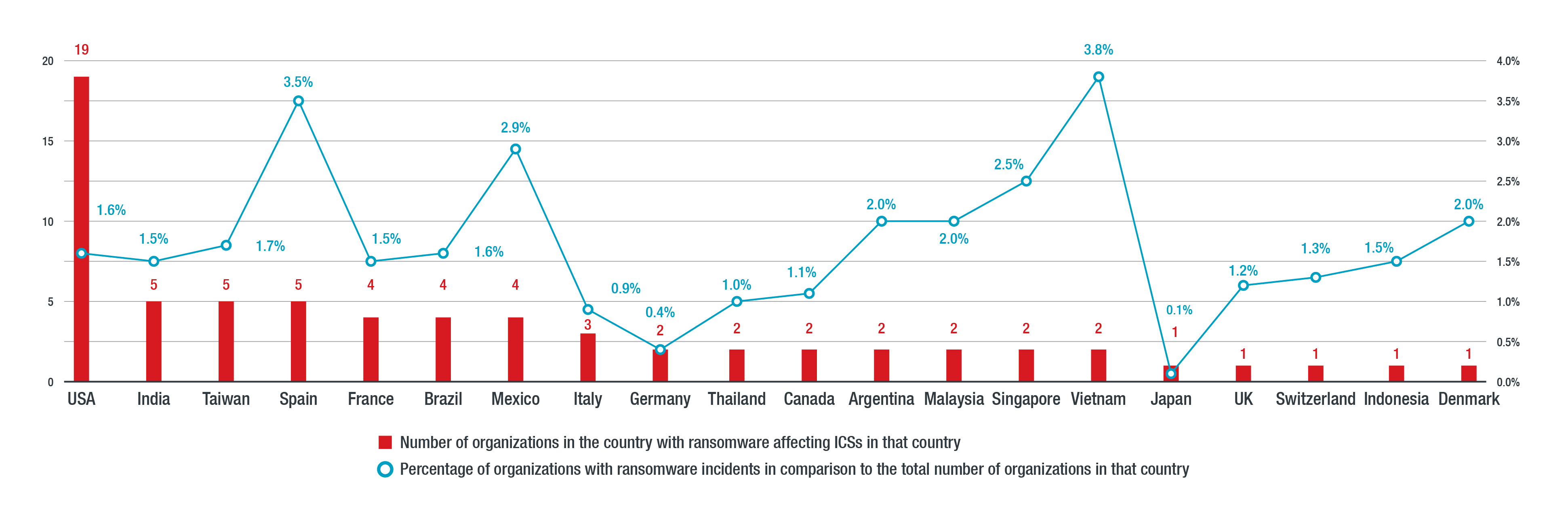
However, taking the percentage of organizations that had ransomware affecting their ICS, Vietnam can be considered to have the most detections, followed by Spain and Mexico.
India had the most coinminer detections, with MALXMR being the most detected variant in 2020. Of the countries with MALXMR running on ICS endpoints, India accounts for more than a third of detections. This shows that ICS software in the country is vulnerable to EternalBlue; this data is supported by the high percentage of detections for WannaCry ransomware in the same region. The said ransomware also exploits EternalBlue.
To protect ICSs from threats, organizations need to regularly patch and update their systems. Although this might be a tedious process especially for legacy systems, doing so is necessary to thwart threats before they get in and do serious damage. If patching is not an option, organizations can also avail of virtual patching technologies.
Organizations can also implement micro-segmentation to enhance security by restricting network access and communications to the necessary devices and protocols. Adhering to the principle of least privilege, where employees are only given the exact level of access they need and nothing more, would also help curb the possible spread of threats.
Security solutions can also help. TXOne StellarProtectTM is an application control security software that only allows known benign executables and processes to execute in an endpoint. This solution delivers patternless protection against both known and unknown malware via machine learning and the ICS root of trust.
Other recommendations and more extensive findings can be read in our report, “2020 Report on Threats Affecting ICS Endpoints”.
Disclaimer: Please note that these detection numbers are from the coverage of the SPN sensors distributed globally, which is not exhaustive. Those regional rankings and figures cannot be free from such market-share influenced distribution bias.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE