Tracking Cobalt Strike: A Trend Micro Vision One Investigation Threats Analyst Threats Analyst Threats Analyst Threats Analyst
![]()
Cyber Threats
Cobalt Strike is a well-known beacon or post-exploitation tool that has been linked to several ransomware campaigns. This report focuses on the process of uncovering its tracks in order to fully contain and remove a malware infection.
In late May, Trend Micro Managed XDR alerted a customer to a noteworthy Vision One alert on one of their endpoints. What followed was a deeper investigation that involved searching for other similarly infected endpoints and the confirmation of a Cobalt Strike detection.
This blog will cover the tactics and steps we took during this investigation. The alert from one endpoint led to the collection of further evidence and clues that pointed to other infected endpoints, eventually revealing the root of the attack.
Cobalt Strike is a well-known beacon or post-exploitation tool that has been linked to ransomware families like Ryuk, DoppelPaymer, and Povlsomware. The Cobalt Strike variant used here follows its typical characteristics. However, this report focuses on the process of uncovering its tracks in order to fully contain and remove the malware.
An overview of the investigation
We first uncovered several detections related to Cobalt Strike, accompanied by a machine learning detection later verified as IcedID. In such cases, the initial detections usually point to something big: the distribution of ransomware. In fact, we published a report on a similar case wherein we used Cobalt Strike to track a Conti ransomware campaign.
Before we delve into the details we want to detail the process we followed in this investigation. It involved several interconnected steps that occurred simultaneously and repeatedly throughout the process. These steps are mainly:
- Creating an indicators of compromise (IOCs) list and observe for tactics, techniques, and procedures (TTPs) to check in the environment, which will be improved in the next items
- Checking the context of the generated alerts
- Examining the execution profile of the files related to the detection
- Collecting additional logs from the endpoint to correlate events
- Checking detections that occurred around the time range of the alerts
These steps allowed us to retrace the actions taken by the variant from a single endpoint and revealing the full extent and its origins. Figure 1 maps out the Cobalt Strike activity that we tracked; it also indicates where we started, at Endpoint-1.
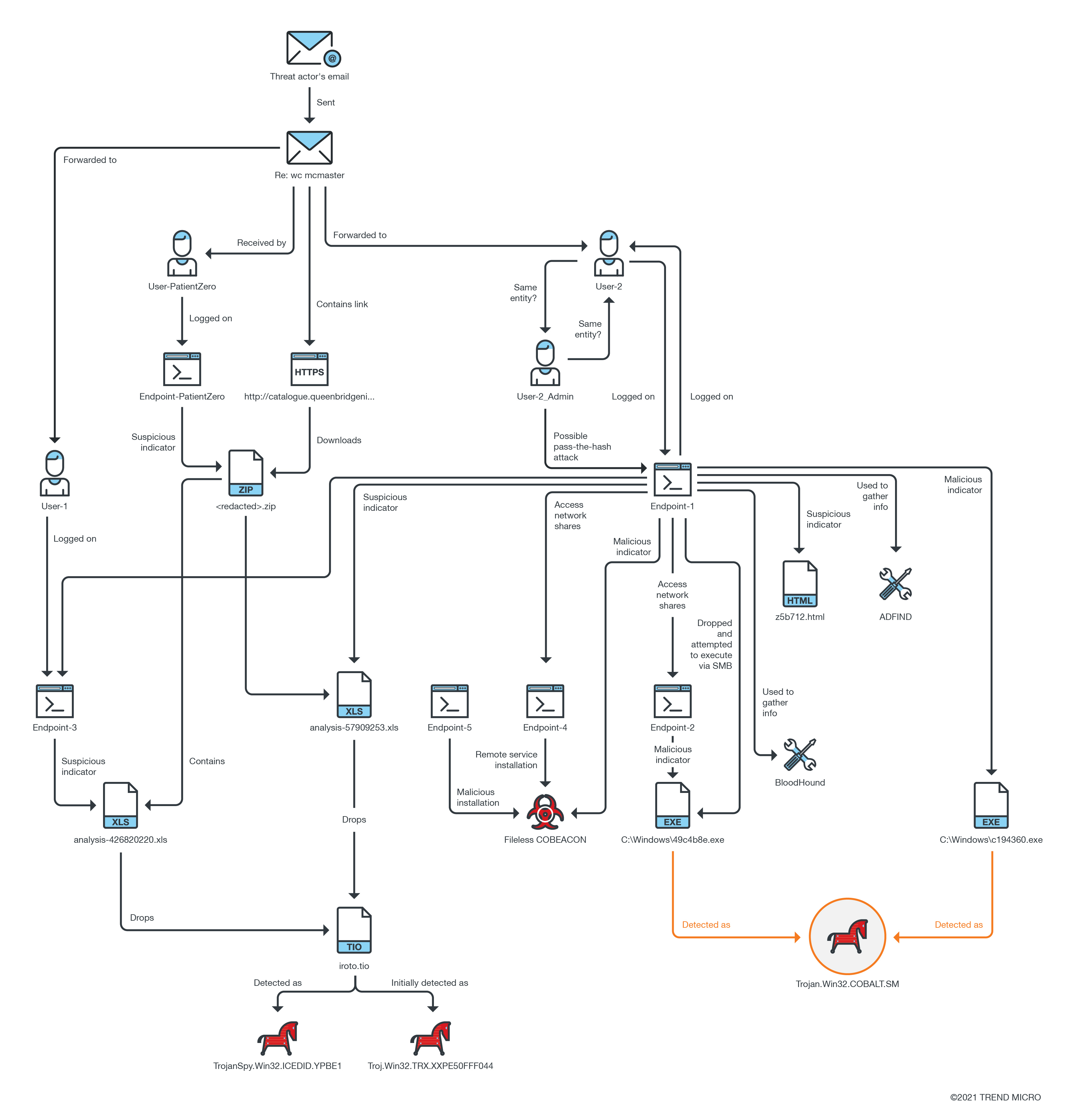
It is important to note that we already provided the affected customer our initial response very early into the investigation, allowing them to start taking steps to contain the threat as we worked to fully reveal its extent.
Initial detections, IOCs, and observed TTPs
As we had mentioned earlier, our investigation started when we noticed suspicious activity in one endpoint. For the purpose of this discussion we shall label this endpoint as Endpoint-1, since this is where we encountered the first hints of an attack. We began our investigation from this endpoint to uncover the real entry point.
Endpoint-1
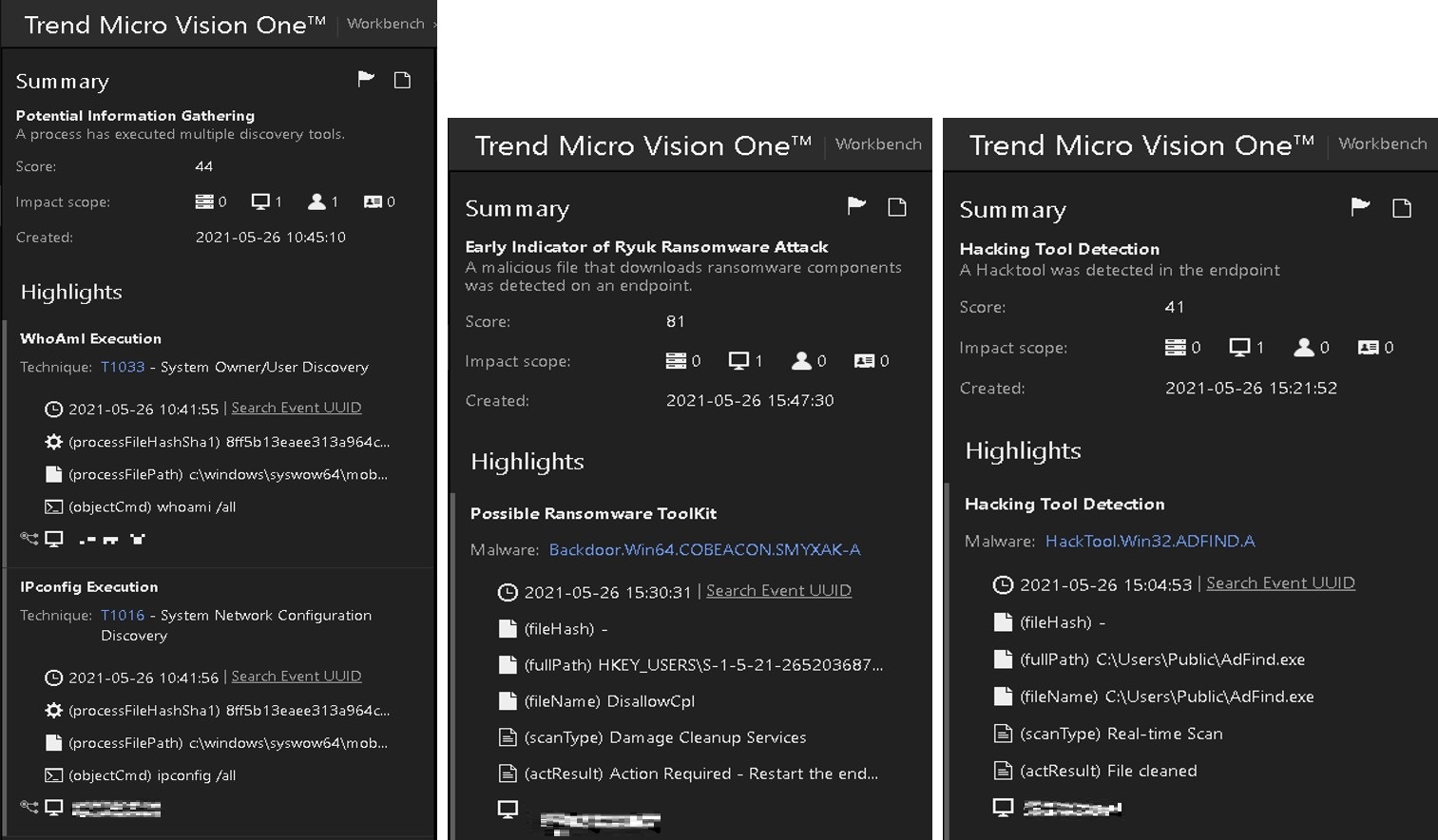
Checking the alerts of Endpoint-1 revealed several important findings that sparked the investigation:
- AdFind.exe was downloaded in the Users\Public directory
- A Cobalt Strike detection occurred, as seen in Figure 1
- Mobsync.exe executed information gathering commands
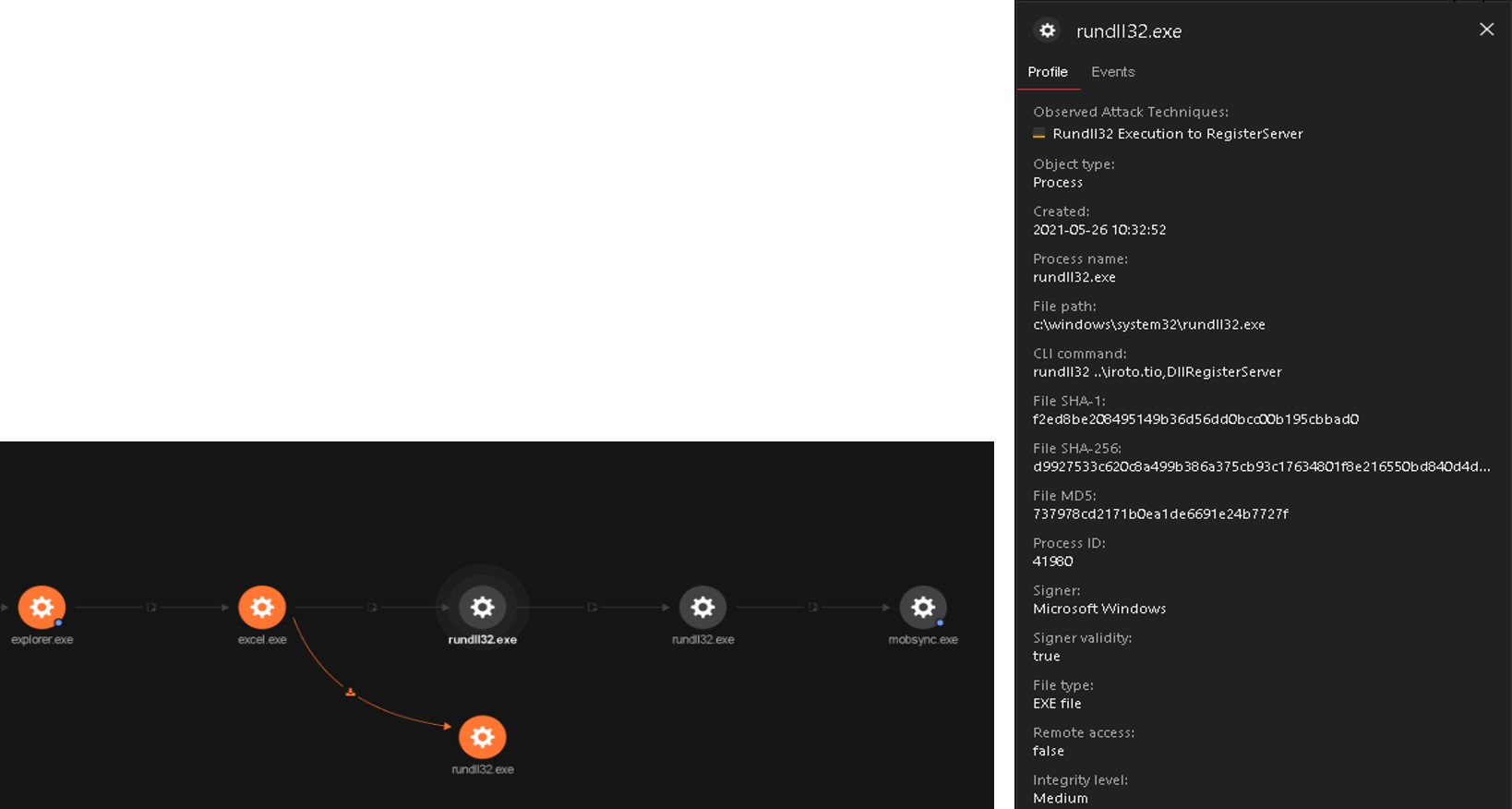
First let us narrow our focus on the suspicious process, mobsync.exe. Vision One’s Progressive RCA allowed us to pinpoint a possible infection vector that lead to its execution. The process chain for Endpoint-1 started with a user executing a file named excel.exe, which then created a rundll32.exe. The rundll32.exe loaded a file named iroto.tio, leading to the execution of the aforementioned mobsync.exe, which is a legitimate MS tool hijacked via process hollowing.
Progressive RCA gave us the choice to expand the nodes to find additional indicators that might be useful to the investigation. In this case, we were interested in excel.exe, or the source; and mobsync.exe, which seemed like the final payload at that point.
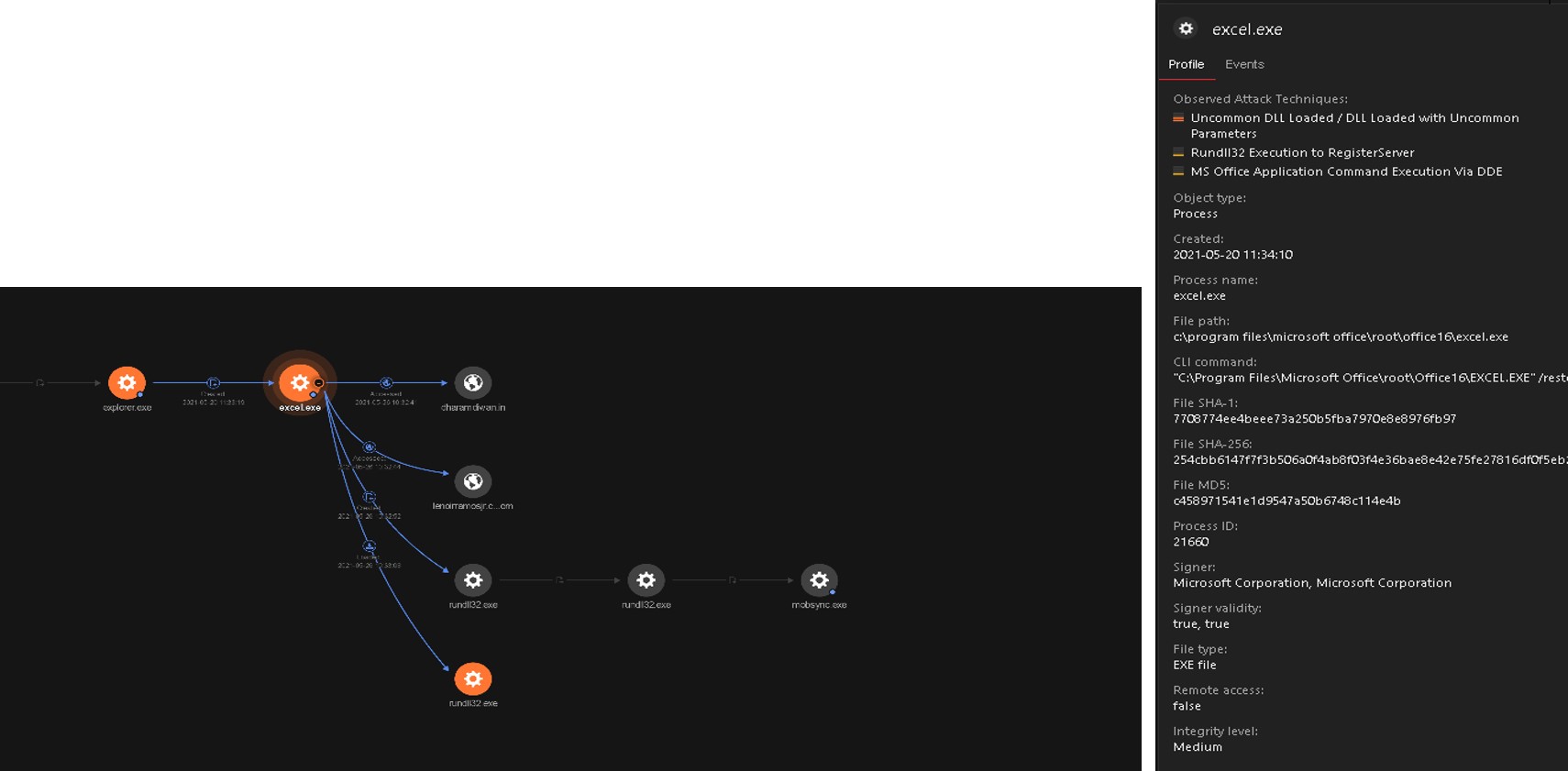
Let us first turn our attention to the excel.exe, which we saw accessing two suspicious URLs dharamdiwan[.]com and lenoirramosjr[.]com before proceeding to drop iroto.tio (not shown in the Figure 3) and loading the dropped file via rundll32.exe.
Vision One’s Observed Attack Techniques (OAT) also showed the techniques used via excel.exe and its child processes, one of which is “MS Office Application Command Execution Via DDE.” Digging deeper in the Vision One console, we identified analysis-57909253.xlsx as the malicious XLS file that utilized DDE.
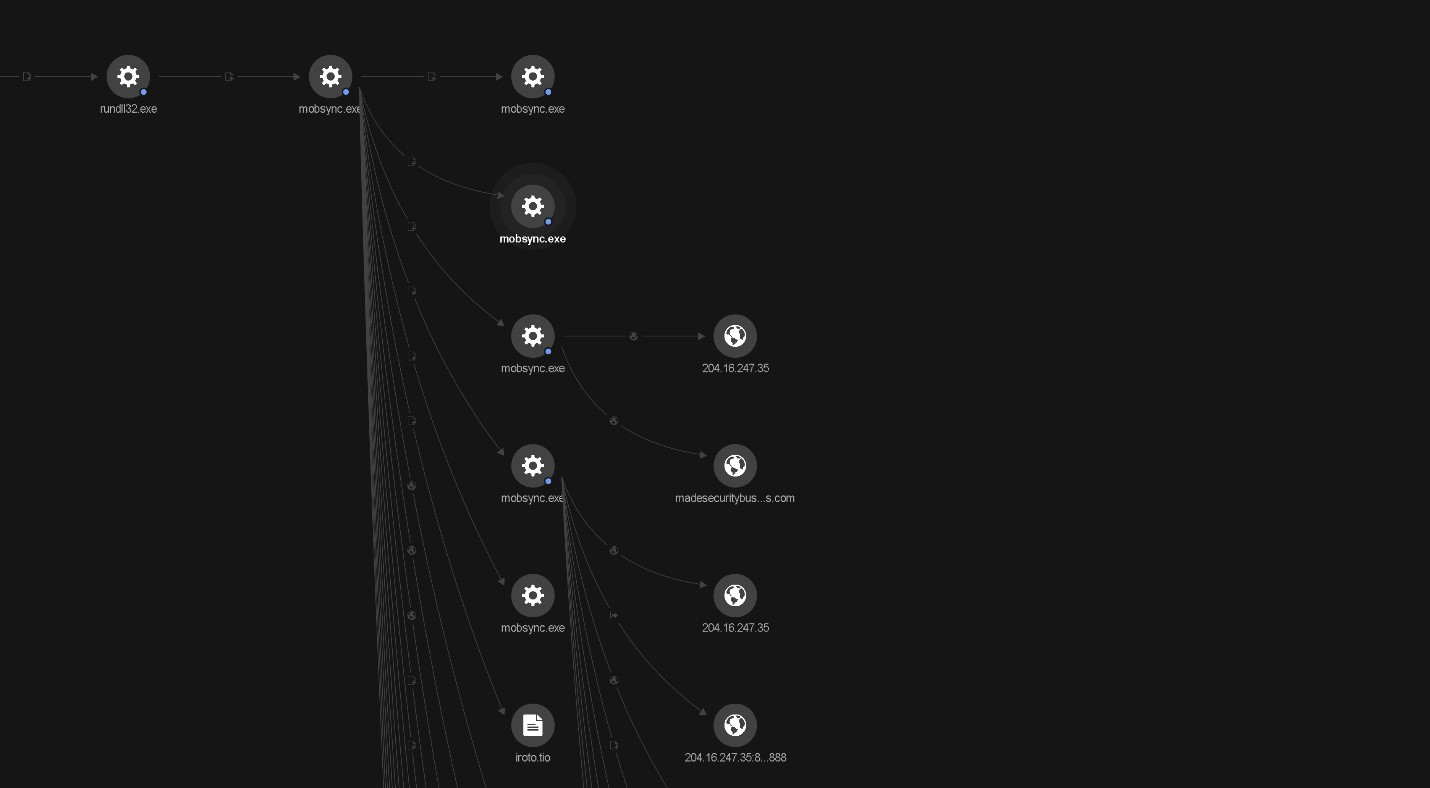
Going back to mobsync.exe revealed several other events, as shown in Figure 5. We summarize the activities done by this injected tool.
It attempts a connection to the following IP addresses:
- 222[.]153[.]124[.]130
- 109[.]106[.]69[.]138
- 75[.]118[.]1[.]141
- 92[.]59[.]35[.]196
- 104[.]98[.]42[.]5
- 204[.]16[.]247[.]35 (madesecuritybusiness[.]com)
It also executed discovery/internal reconnaissance commands and spawned additional mobsync.exe processes, as shown in Table 1.
|
Date and Time (UTC) |
Process |
|
5/26/2021 0:41 |
whoami /all |
|
5/26/2021 0:41 |
cmd /c set |
|
5/26/2021 0:41 |
arp -a |
|
5/26/2021 0:41 |
ipconfig /all |
|
5/26/2021 0:41 |
net view /all |
|
5/26/2021 0:42 |
nslookup -querytype=ALL -timeout=10 _ldap._tcp.dc._msdcs.[WORKGROUP] |
|
5/26/2021 0:42 |
net share |
|
5/26/2021 0:42 |
route print |
|
5/26/2021 0:42 |
netstat -nao |
|
5/26/2021 0:42 |
net localgroup |
|
5/26/2021 1:50 |
C:\WINDOWS\SysWOW64\mobsync.exe |
|
5/26/2021 1:50 |
C:\WINDOWS\system32\ping.exe -t 127.0.0.1 |
|
5/26/2021 1:58 |
C:\WINDOWS\SysWOW64\mobsync.exe |
|
5/26/2021 1:58 |
esentutl.exe /r V01 /l”C:\Users\[Endpoint-1-User]\AppData\Local\Microsoft\Windows\WebCache” /s”C:\Users\[ENDPOINT-1-USER]\AppData\Local\Microsoft\Windows\WebCache” /d”C:\Users\[ENDPOINT-1-USER]\AppData\Local\Microsoft\Windows\WebCache” |
|
5/26/2021 5:33 |
C:\WINDOWS\SysWOW64\mobsync.exe |
|
5/26/2021 5:33 |
C:\WINDOWS\system32\cmd.exe /C ping [ENDPOINT-4] |
Table 1. A list of the commands executed by mobsync.exe
We also identified Bloodhound and ADfind.exe hacking tools deployed in Endpoint-1. These tools can be used to extract information from the Active Directory.
|
Date and Time (UTC) |
Process |
|
5/26/2021 5:00 |
C:\WINDOWS\system32\cmd.exe /C del 20210526145501_BloodHound.zip YmNhMTJiMzAtYTgxZi00ZWRmLWE2ZjctZTc3MDFiZGM2ODBj.bin |
|
5/26/2021 5:04 |
C:\WINDOWS\system32\cmd.exe /C AdFind.exe -f objectcategory=computer -csv name cn OperatingSystem dNSHostName > [REDACTED].csv |
Table 2. Bloodhound and ADfind.exe in the logs of Endpoint-1
With Vision One and the Trend Micro Investigation Toolkit (TMIK), we were able to identify potential Pass-the-Hash (PtH) attacks that extracts the password hash from the memory and then simply passes it through for authentication. If there are recent logins of high privilege accounts in the machine, then the password hash of these logins can be extracted by attackers to perform lateral movement to other networked systems. The event logs also showed a related entry for the PtH technique stating, “Found 4624 event logs with seclogo as process for ENDPOINT-1-USER.”
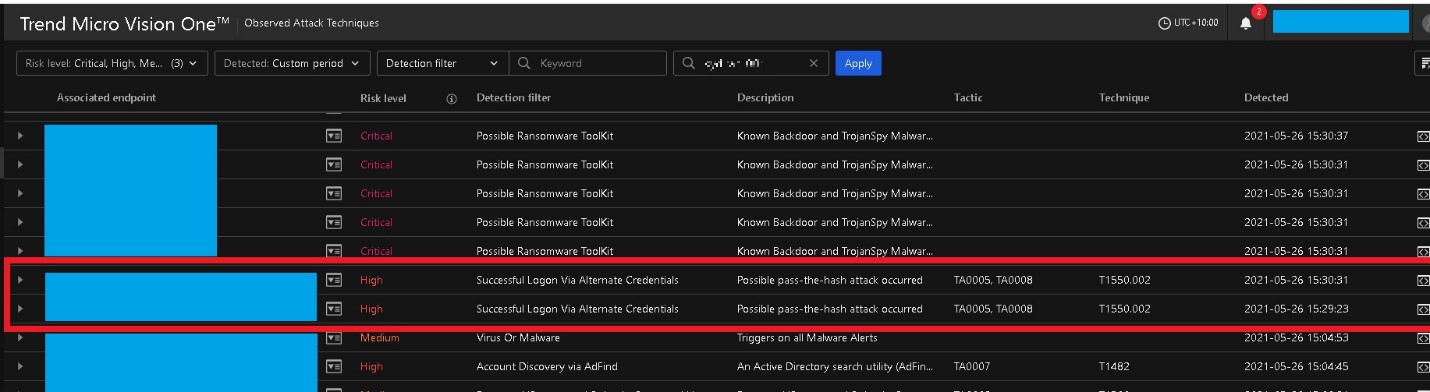
Aside from Endpoint-1, we also found several other endpoints where we identified Cobalt Strike detections. We specify another two here as they already contain the evidence, such as a list of IOCs and observed TTPs, that we needed to pinpoint “Patient Zero,” or the first machine to be infected by the malware.
Endpoint-2
We will label another endpoint as Endpoint-2. Endpoint-2 is a machine that Vision One also alerted to have shown Cobalt Strike detection.
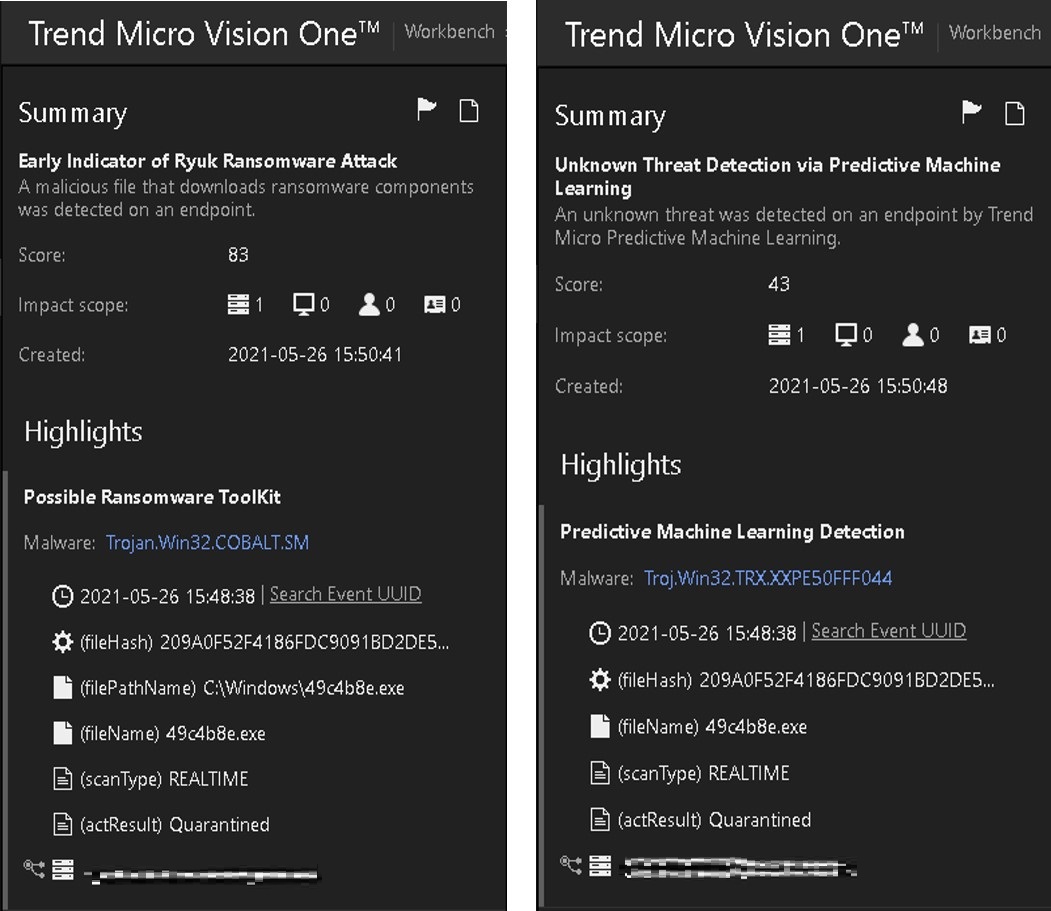
Vision One’s Execution Profile for the file shows ntoskrnl.exe executing 49c4b8e.exe. This sequence of processes in the execution profile implies that the file was transferred via SMB, evidence of lateral movement which was stopped due to the detection.
Hunting IOCs and TTPs
With all the findings from Endpoint-1 and Endpoint-2, we were able to observe for TTPs and create an IOC list that we can search across all the machines reporting to Vision One. This search was based on the following indicators:
- Filename and hashes of the detected files
- Suspicious behavior, such as excel.exe spawning rundll32.exe or mobsync.exe spawning cmd.exe
- Possible command and control (C&C) connections
- Compromised accounts used for lateral movement and are transferred files via SMB
- Detections that occurred around the time the alert occurred (commonly used time range is Last 7 days)
Searching the IOCs in the Vision One search app revealed several other machines related to this case, as shown in Figure 1. An example of such a machine is one that we labeled Endpoint-3.
Similar to Endpoint-1, there were malware detections in the machine, where it blocked the execution of excel.exe that spawned rundll32.exe. There was also a machine learning detection related to the file iroto.tio. Finally, inspecting Workbench alerts showed an entry for Cobalt Strike.
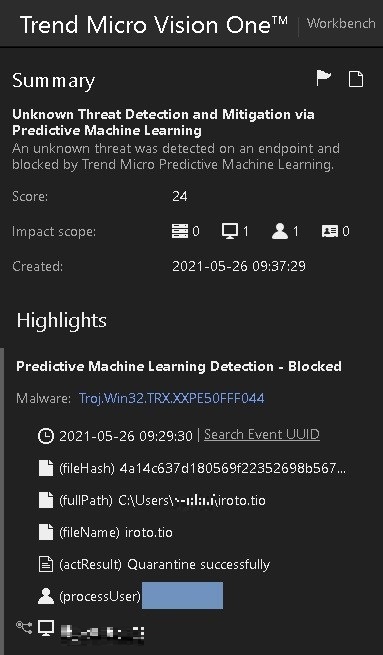
Investigating Endpoint-3’s execution profile showed that the excel.exe process connected to the same suspicious domains that we mentioned earlier. It also created the file iroto.tio.
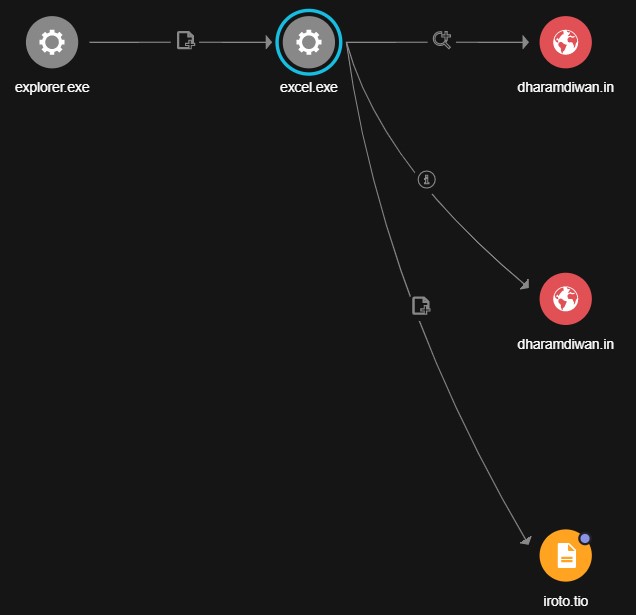
With a list of IOCs and TTPs we were able to look for other infected machines or endpoints and were also then capable of narrowing down Patient Zero.
Locating Patient Zero
Since we know for sure that the threat started with an execution of excel.exe and the .xls file it opened, it is logical to assume that the attack started from an email attachment, which was the case here. The Vision One, Managed XDR team was able to eventually track down the entry point of this attack: a socially engineered spear phishing email sent to an internal user.
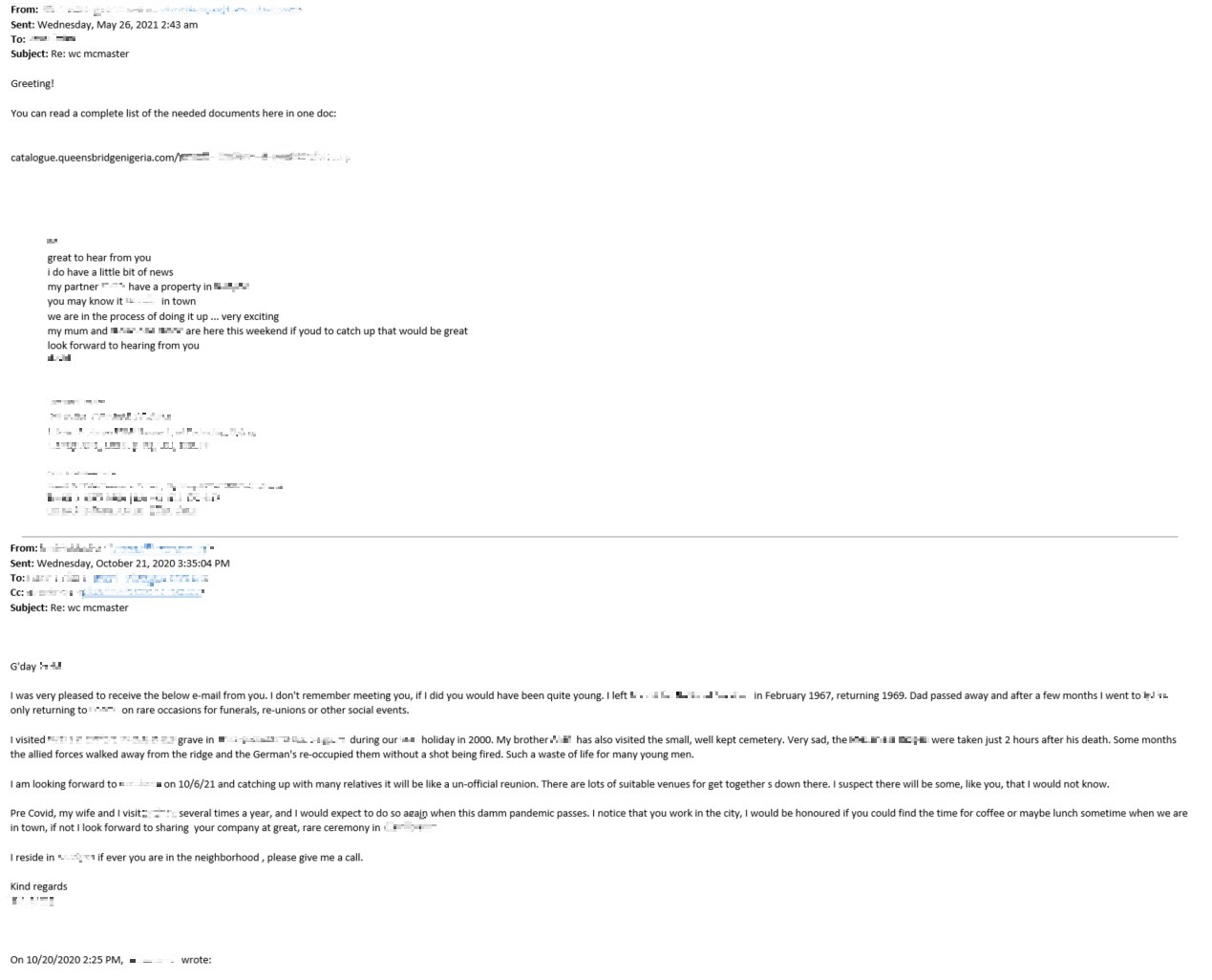
The threat actor made the email seem as if they were replying to an email the targeted user had sent them, thus making it appear as if they already had an existing conversation thread. They also used a forged sender email address so that the targeted user would think that the email came from a legitimate sender. The email contained a link to download a malicious archive file with the name of the targeted user.
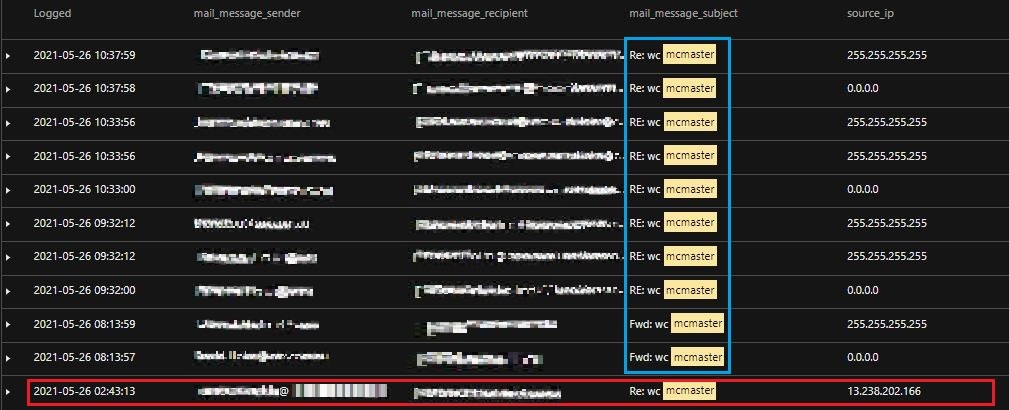
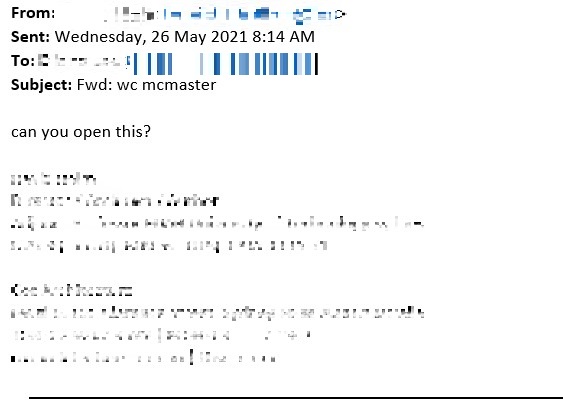
Through Vision One, we were able see that a few minutes after receiving the email, the targeted user forwarded the malicious email to another internal user. These results from Vision One (Figure 11) matched with the email that Managed XDR had acquired (Figure 12), thus proving that the machine was Patient Zero and rounding out our investigation.
Responding to the threat
The overall goal of the investigation was to get a full scope of the Cobalt Strike infection. This involved identifying the IOCs we can use to search for all the machines that were infected, as well as stopping the spread at the root.
All throughout the process we had been reporting to the affected customer, especially after the discovery of each of the affected endpoints. This is to quickly contain the spread of the malware variant. The response to this threat included the following, in no particular order:
- Isolation of affected endpoints as the investigation was being conducted
- Disabling/resetting the passwords of the user accounts that were used for lateral movement
- Collecting related artifacts to the threat and doing further analysis, which were also submitted for detection to improve coverage
- Blocking of domain/IP addresses related to the C&C of the threat
- Further monitoring of the environment to ensure that there’s no suspicious activity going on
Many of these steps were done simultaneous to the investigation, so as not to risk possible consequences and prevent the spread of the malware to other machines.
Conclusion and recommendations
The result of the investigation demonstrated the importance of a multi-layered security approach in protecting the environment. This is crucial so that in case one layer of protection fails another is present to keep the environment safe or at least limit the impact of an attack.
Prioritizing detections and combining different techniques can help in catching the threat and initiating a quick response. As this case reflects, preliminary security events should be taken seriously as they usually are the precursor to something bigger, such as breaches and ransomware attacks.
The investigation also highlights the incident response process for handling breaches and malicious activities. It emphasizes how threat response does not end upon the detection of a threat; an investigation is key to understanding a threat and preventing them from occurring again. Using acquired knowledge from previous attacks and boosting user awareness of common threats can improve the overall security posture of any environment.
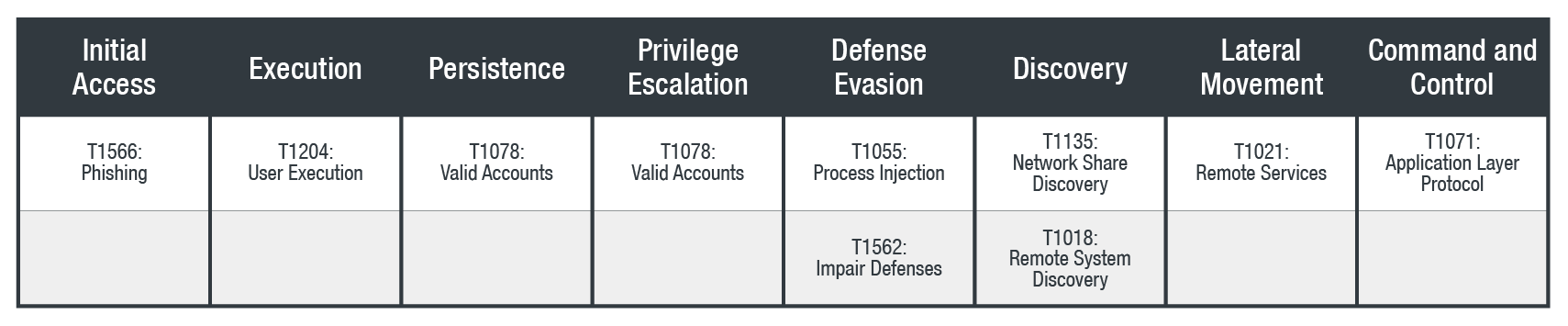
MITRE mapping
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



