Unveiling the Fallout: Operation Cronos’ Impact on LockBit Following Landmark Disruption

The first 72 hours after LockBit’s disruption
In the days following the disruption, the topic was still being widely discussed across underground forums. Members of the forums seemed to appreciate the NCA’s sense of humor, commenting that the law enforcement agency was trying to be “lulzy” (internet slang for comical or amusing) in its actions on LockBit’s leak site. The release of information regarding the arrests also instigated further conversation. There was also a consensus that LockBit would simply rebrand and return, similar to what happened with Conti, Royal, Black Basta, and Hive, although as the rest of the week went by, LockBit’s reputation was further damaged.
On one Breachforums thread that discussed the disruption, one member was of the opinion that LockBit deserved the disruption due to the group targeting hospitals. In the initial days following the disruption, the Exploit and XSS forums seemed to be unusually constrained in their discussion of the topic. The discussion about LockBitSupp’s ban status was active, but the overall discussion pertaining to LockBit’s disruption seemed to be less active than in other forums. One reason for this could have been that as two of the more mature forums in operation, the members of Exploit and XSS might have been under instruction to be wary of researchers and law enforcement monitoring their activity following such a high-profile action.
An interesting observation when looking at the fallout from the disruption is that it sparked some self-reflection among other active RaaS groups. Notably, competitor RaaS groups expressed much interest in learning about how LockBit was infiltrated. A Snatch RaaS operator also pointed out on their Telegram channel that they were all at risk. This is a subtle bonus stemming from the disruption operation: the spread of paranoia in the cybercriminal ecosystem. Other groups are now taking a closer look at what they need to do to reduce the risk of infiltration. Anything that makes operating more difficult is a good thing in the fight against ransomware actors.
In a period that fostered paranoia and introspection, it’s no surprise that members of the criminal underground started to question whether LockBitSupp had collaborated with law enforcement or otherwise. Although there were several mentions of LockBitSupp cooperating with the Federal Security Service (FSB), it’s important to note that this is just speculation and not something we can confirm. The claims were probably bolstered by a Chainalysis report that LockBit group sent donations to a certain “Colonel Cassad” in Donetsk.
Although LockBitSupp was guarded when it came to public communication efforts, which is partly due to its being banned on XSS and Exploit, LockBitSupp attempted to preserve the appearance of being in control of the situation. For example, LockBitSupp responded to the law enforcement countdown that would release information about its identity by doubling the reward to US$20 million. This was a clever move on LockBitSupp’s part, as it seemed to garner support in the criminal underground. The apparent defiance might have also been part of a strategic plan to try to persuade affiliates that the operation was not under threat. In some ways, LockBitSupp appears to have resorted to a PR tactic that many of its own victims were forced to enact following ransomware attacks: LockBitSupp publicly projected a position of strength to its customer base while also internally trying to rebuild and get back to business.
In the first 72 hours, many speculated about the extent of the information to be released about LockBitSupp. There was a lot of build-up leading up to it, which was heightened by the NCA using the infamous LockBit countdown to make the announcement. There was also some confusion in the first few days, with people looking for the official LockBitSupp Telegram channel. This was a result of several accounts masquerading as LockBitSupp. Given the curiosity and media attention generated by the disruption, some actors sought to capitalize on the confusion and take advantage of unwitting victims. For example, a Telegram user with the handle “Lockbit 3.0” claimed to be a LockBit operator and offered positions for affiliates to join the group for a small fee of US$150.
The first week post-LockBit disruption
The much-anticipated leak of information about the threat actor LockBitSupp seemed to have been perceived as anti-climactic in the underground community. Law enforcement’s use of the “Tox Cat” emoji in its announcement, to imply some level of access that it had to LockBit’s operations, was also seen as further trolling from law enforcement. To add, some felt that the lack of details showed that LockBitSupp had called its bluff. However, it was clear that the vague reference to LockBitSupp’s communication with law enforcement did have the desired effect of seeding doubt among some members. Less than an hour after the release of the message pertaining to LockBitSupp talking with law enforcement, some messages on Telegram mentioned that “There’s chatter that Lockbit is a snitch.”
There was also speculation that other groups could now become the market leader, with ALPHV being touted to rise to the top. We now know following the events surrounding ALPHV that this would not be the case.
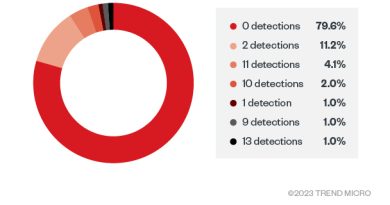
There was also a discussion about how victim data wasn’t deleted following a payment. It was pointed out that this was no surprise when you consider the value such data would still hold.
As the dust settled following the first few days, there were still a few actors who were focused on how the disruption came about and what its implications were. Some members of the criminal underground undertook their own investigation and began trawling through old posts and dissecting what was said in the past. This further demonstrates the state of paranoia that the disruption instilled.
In a rebuttal to law enforcement’s press release, LockBitSupp announced that it will return with new Onion sites on Feb. 24, 2024 and added fbi.gov as the first victim on the new leak site.
Read More HERE