Virtual Event: Google Cloud Next | October 12 – 14 Solution Engineer
Workload Security
Level-up your skills and uncover what’s next for cloud by registering for the virtual Google Cloud Next conference starting Oct. 12, 2021.

The next thing I did was enable the APIs with Google Cloud Deployment Manager in my personal GCP project, so I could interact with the Google Cloud Deployment Manager programmatically.
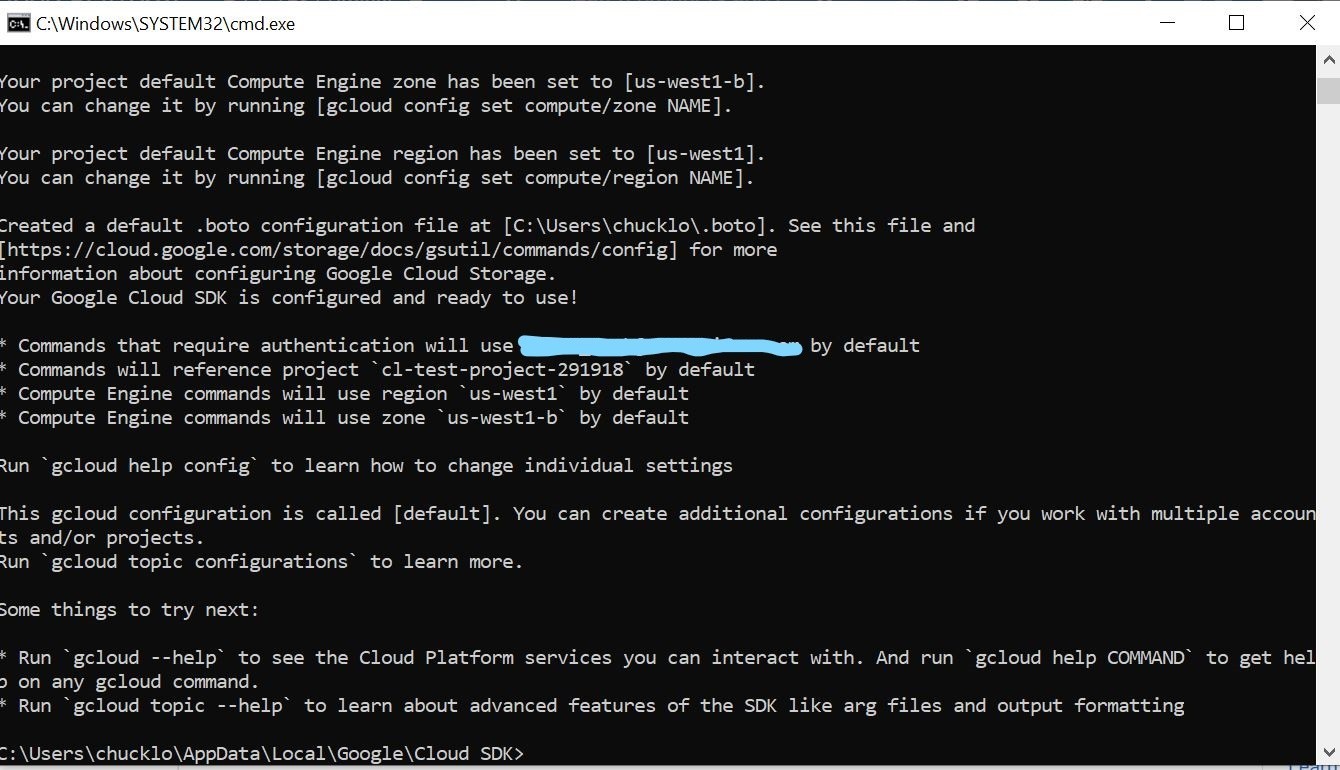
After doing this and authenticating to my GCP account, I should be able to interact with Google Cloud Deployment Manager, as shown below.
Ok, cool! So, let’s go ahead and spin up a virtual machine (VM) that we will use as our source image for IaC. We will go ahead and run our Trend Micro deployment script to bake the security agent inside this test GCP source image. This is one way to install the Workload Security agent. You could also call the deployment script at VM launch time with the start-up script attribute. I will show both methods as an example.
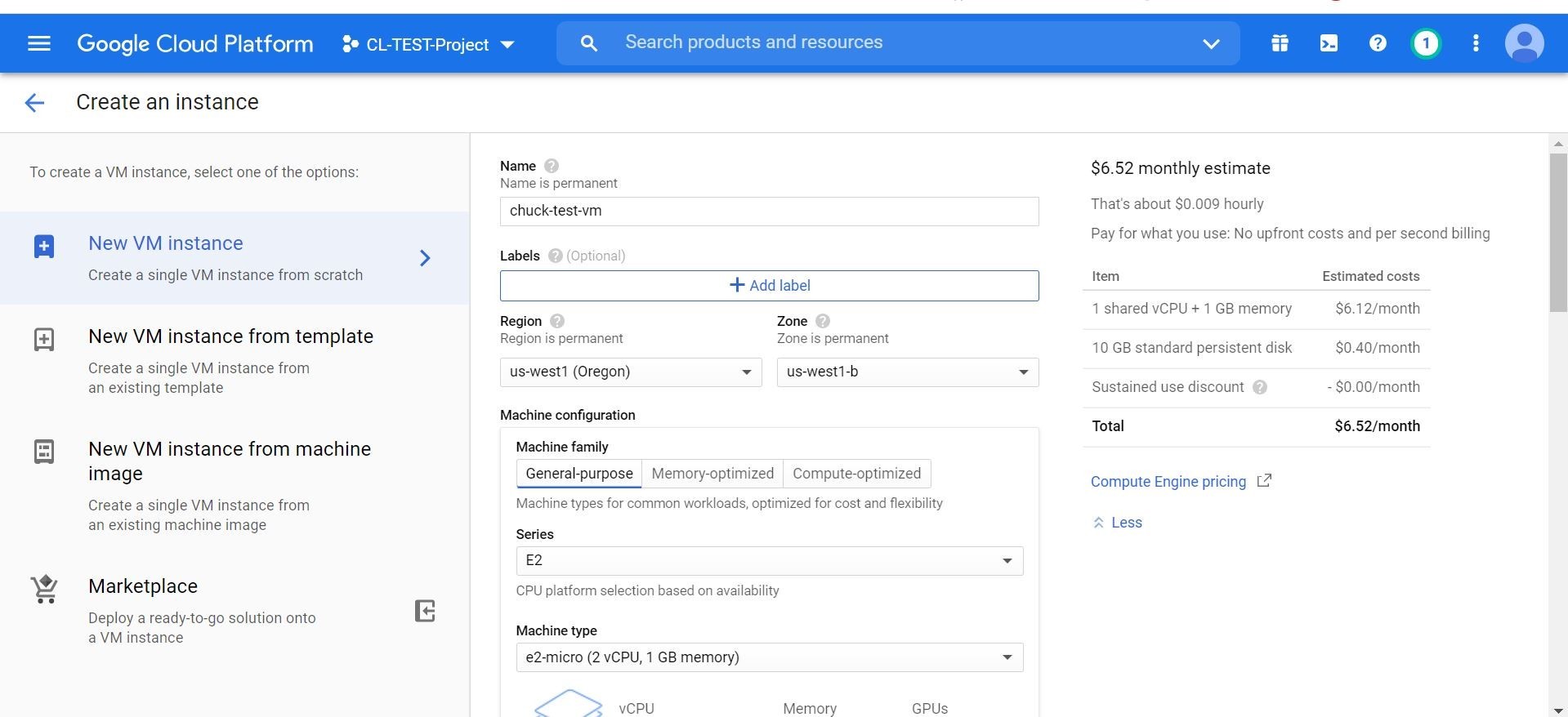
So, after my source machine has been provisioned, I am going to go ahead and ssh onto the instance. Next, I downloaded my handy-dandy deployment script from my Trend Micro Cloud One™ console shown below. Look out below! Screenshots galore!
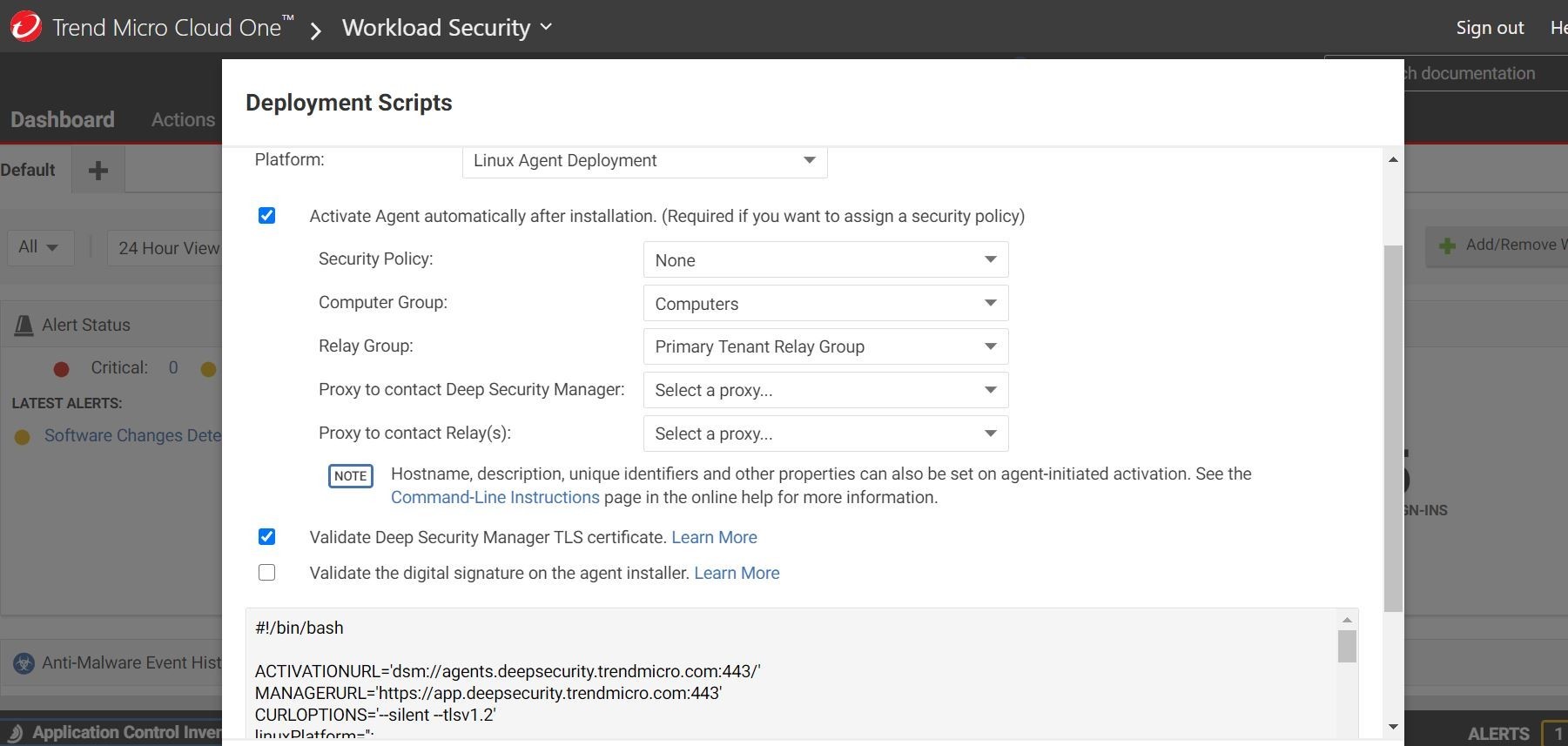
In the ssh procedure, I went ahead and copied the deployment script and made it executable to run on my source image machine. You can see the agent being installed.
Let’s go ahead and check in on the Trend Micro Cloud One console and see if this source machine has checked in properly.
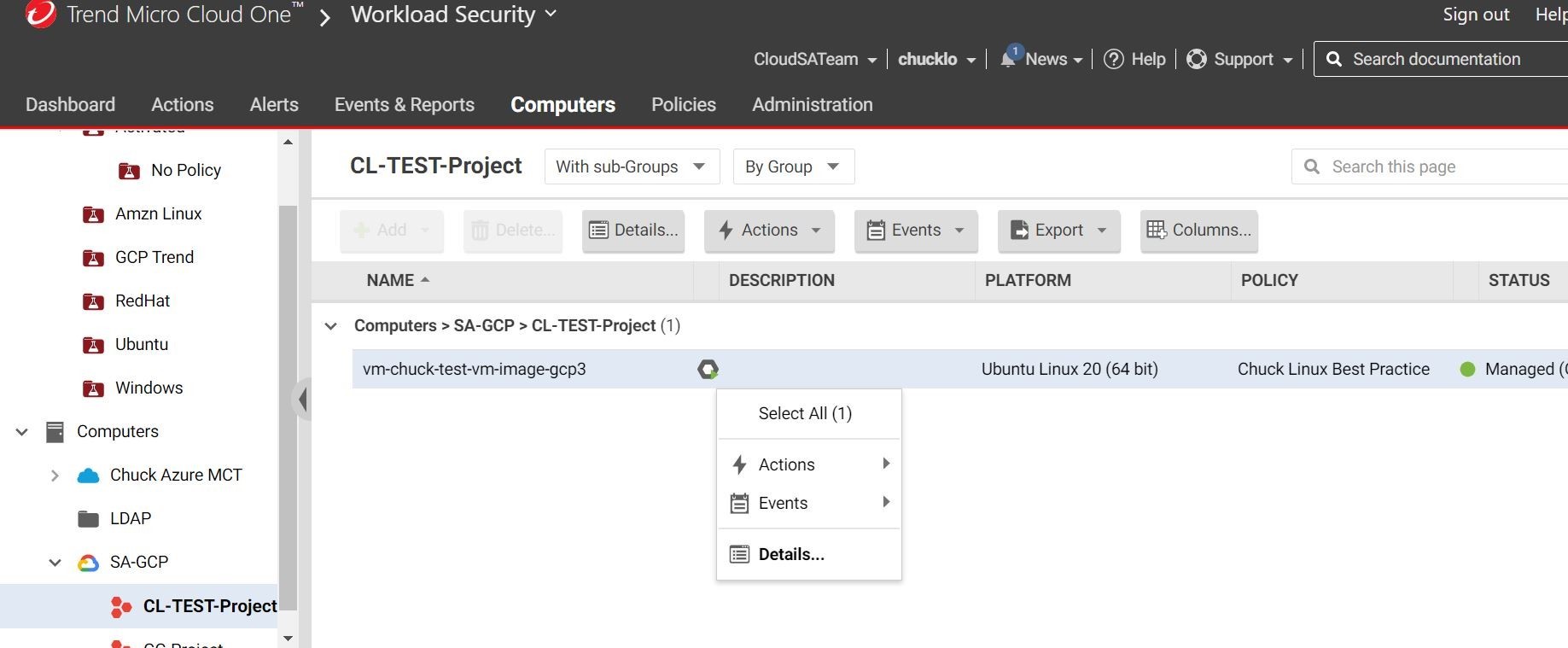
Looks like it has and is showing as managed and online.
Let’s stop right here and detour a bit. If you notice, we have the GCP account/project integration on the left-hand side. It’s awesome that you can tie-in your GCP account and associated projects to see if your workloads are protected. Integration at its finest! You can also add other associated GCP accounts or other public cloud accounts for a single pane of glass for all your cloud workloads. As Bill and Ted say: excellent!
Here are the docs from Trend Micro to easily add your GCP accounts and subsequent projects with a GCP connector using a GCP service account.
Alrighty then! Next, I created a repeatable image of that VM using the image creation option with compute engine in my project.
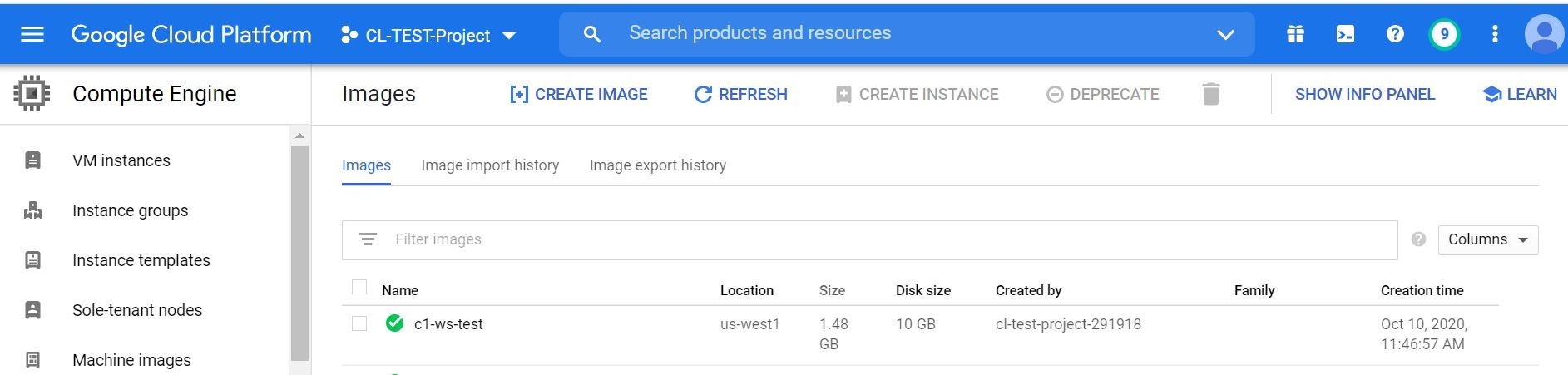
Now, I have a source image that I can use for repeatable deployments in the future that has my Trend Micro Cloud One agent already pre-installed.
With those repeatable deployments, we are going to use IaC utilizing the sample deployment templates from Google’s official GitHub.
Here is my Visual Studio Code IDE showing the section where I add my newly referenced source image stored inside my GCP account to the deployment template. You can also utilize the start-up script method and pull in the deployment script from an available Google Storage Bucket. We are going to utilize the pre-baked custom image we made earlier.
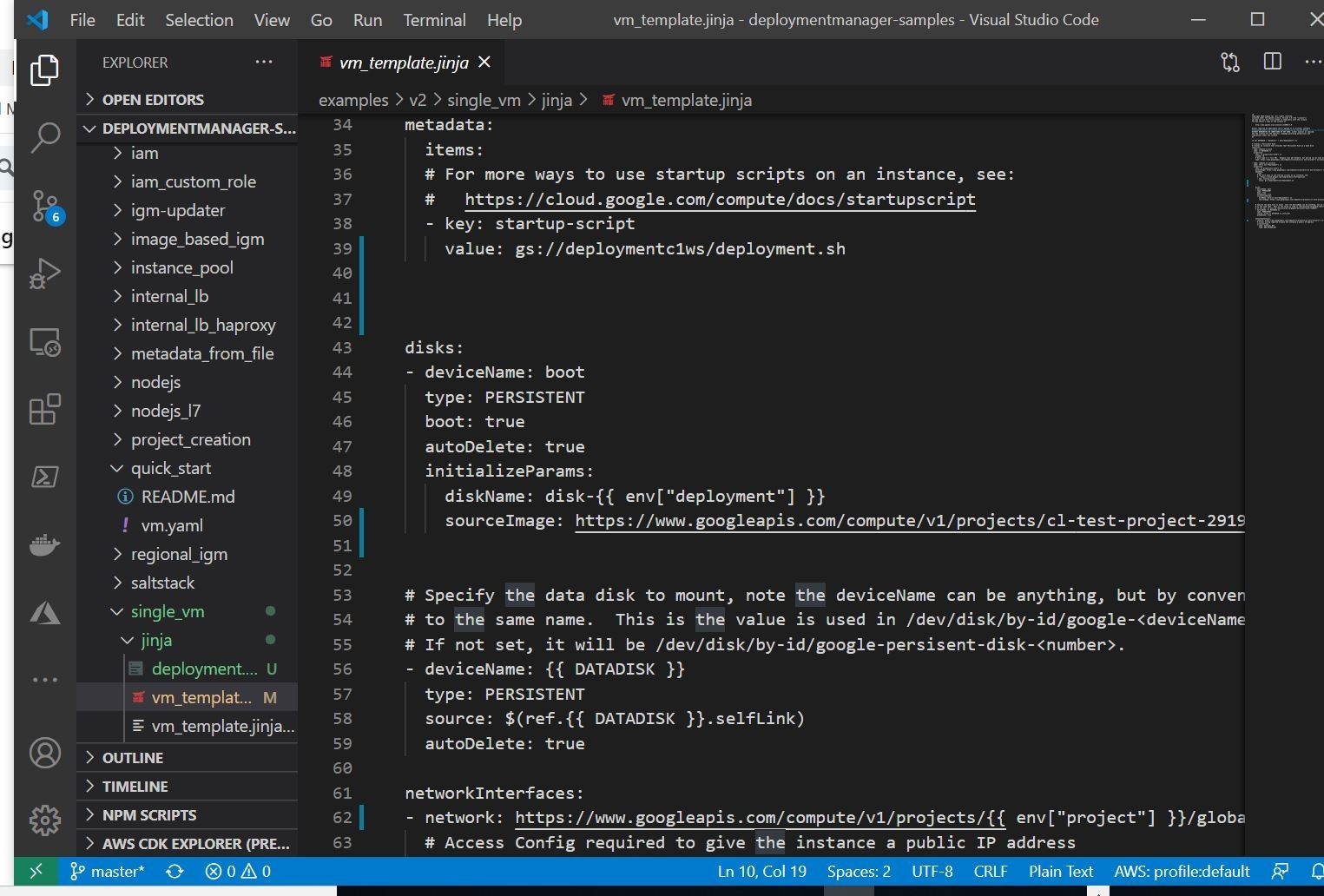
Here we are running our deployment script utilizing the Google Cloud SDK on my system.
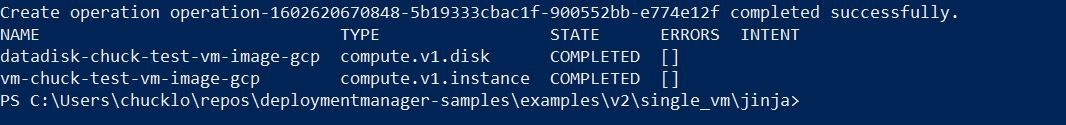
You can also monitor the deployment process in the GCP console with the Google Cloud Deployment Manager.
Alrighty, that looks awesome! Let’s check our Trend Micro Cloud One console and see if our GCP workload shows up.
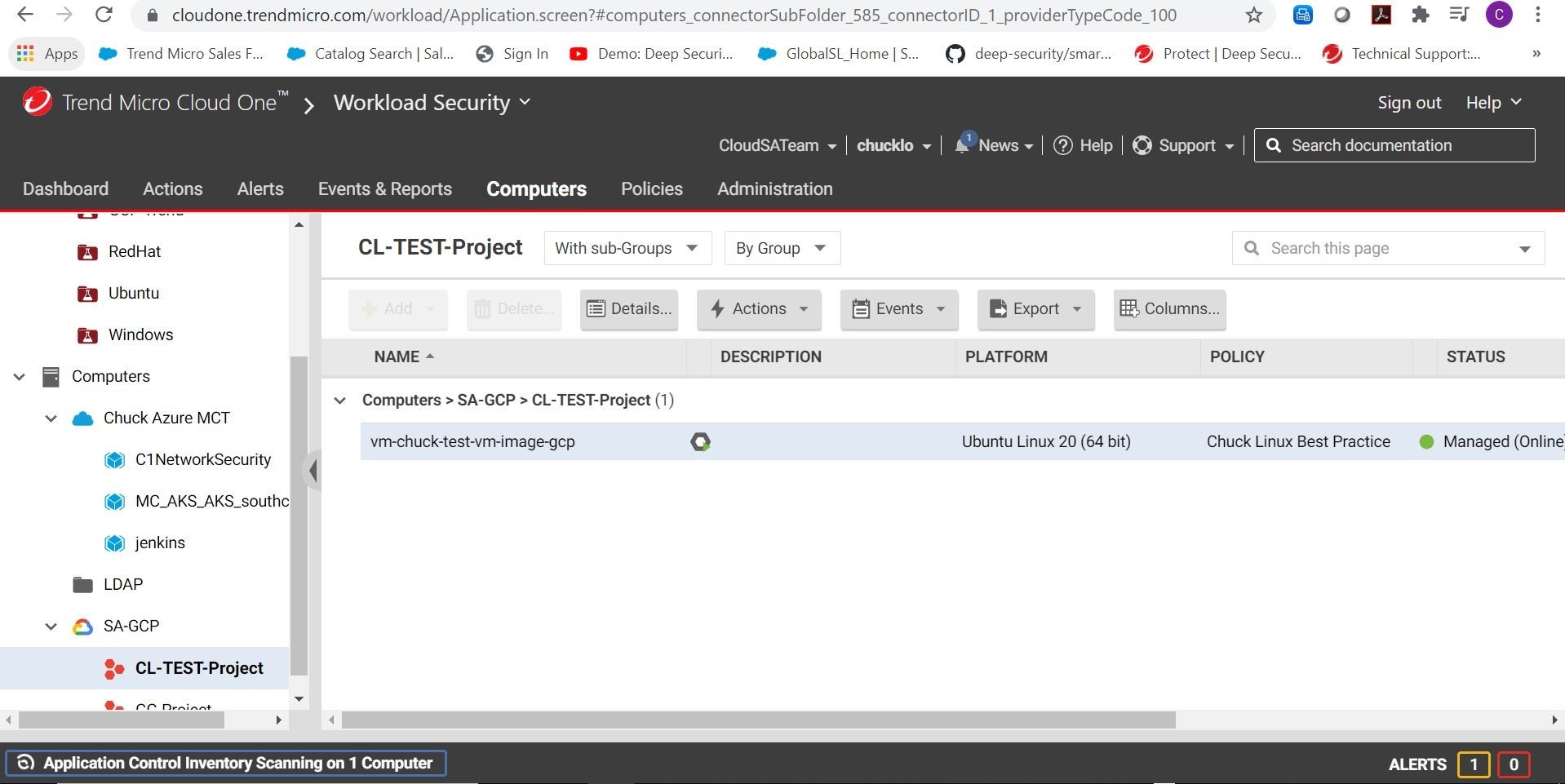
Yep, there it is! Looks like it automagically applied a security policy. How did it do that? I don’t remember specifying that in the deployment script that I ran on the initial capture image. Ohhh, ok, yes, I forgot to show you event-based tasks in Workload Security.
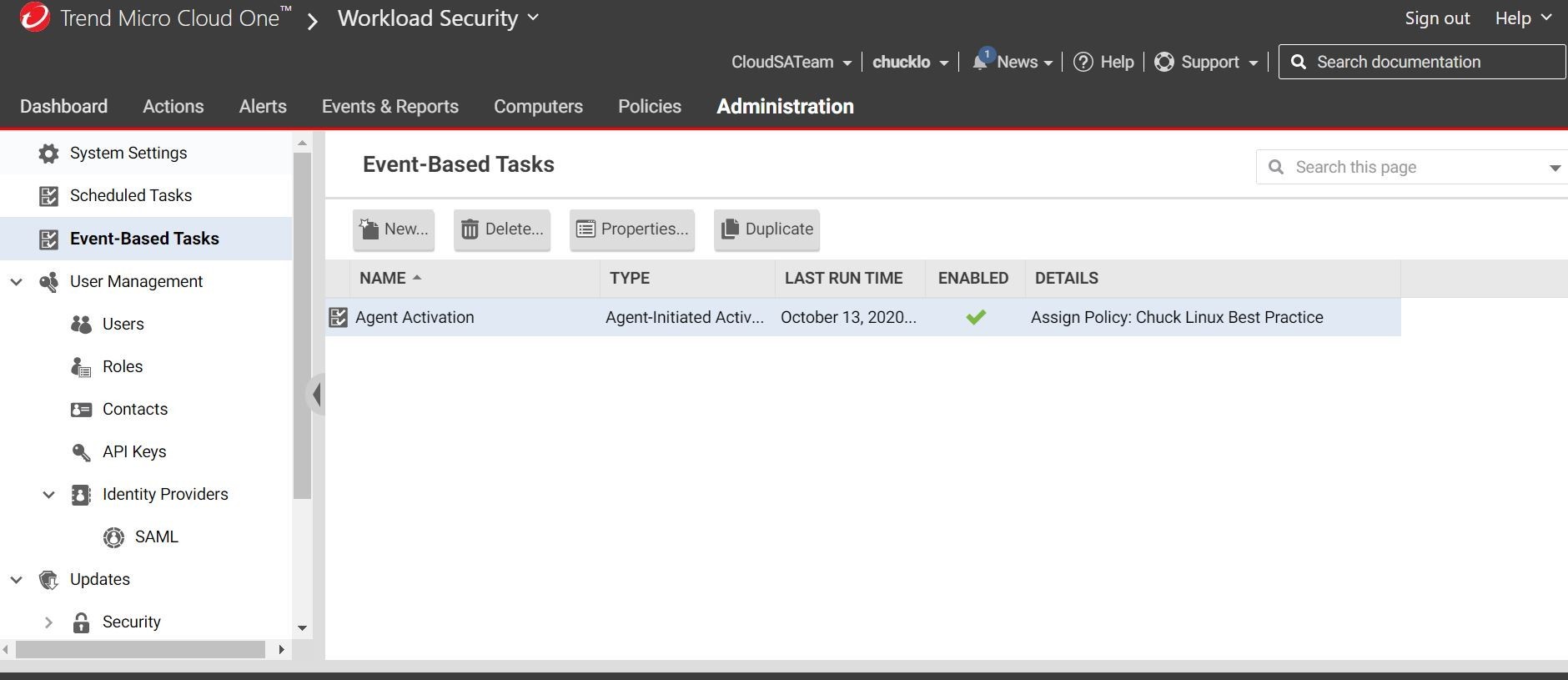
So, in the Administrative section of the Workload Security console, you can easily create an event-based task for your GCP workloads. This way, I make sure that I have a policy assigned for every machine I spin up in my GCP account with a “Linux Best Practices policy”.
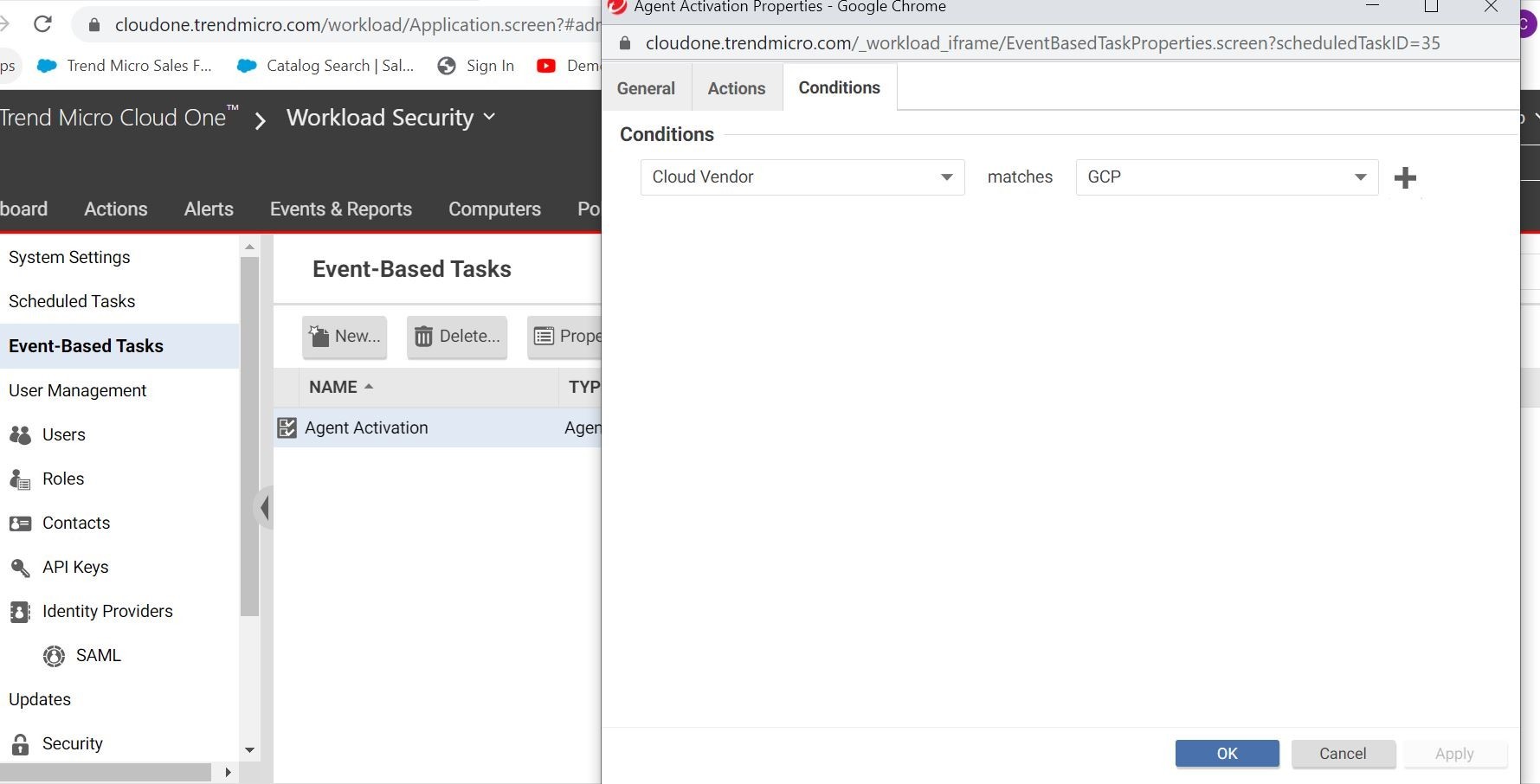
You can always use Smart Folders to easily get to the workloads that you want to inspect based off GCP tags, etc. Here is an example where I am filtering by OS and GCP label.
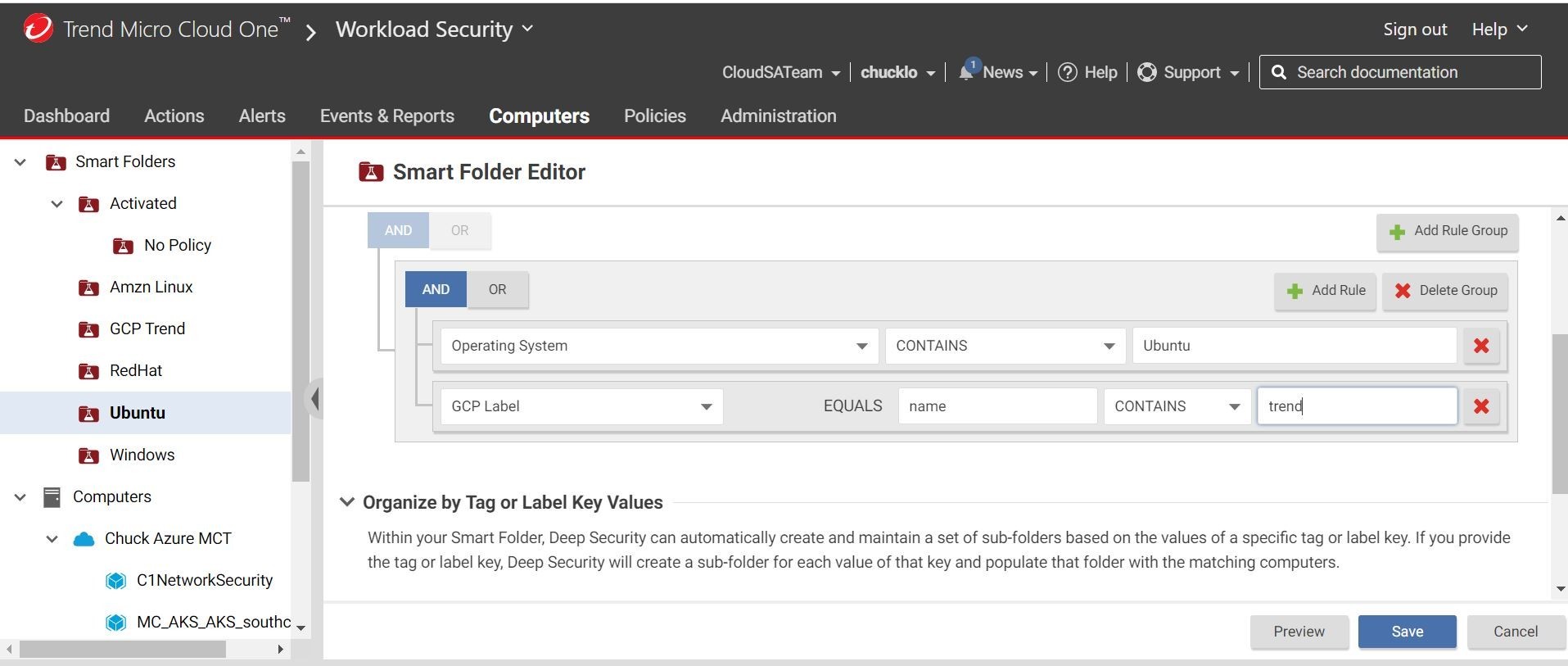
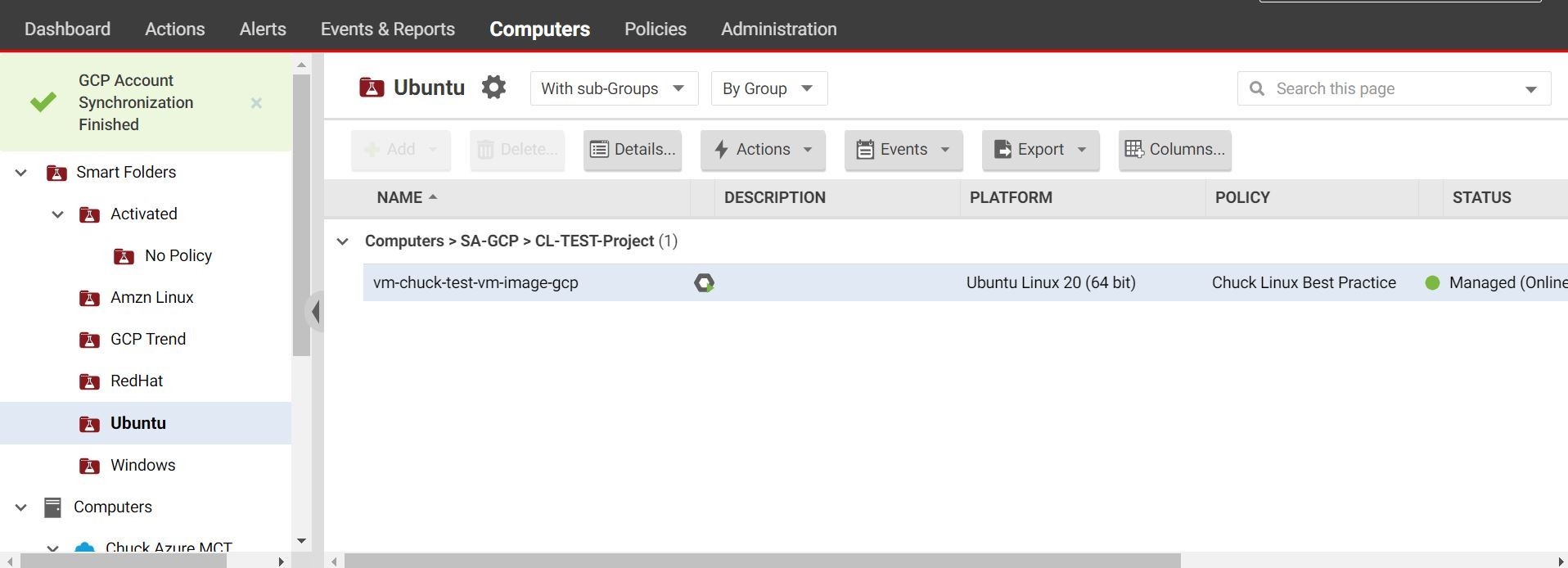
Checking out my smart folders instead of going into and drilling down into the GCP projects level saves me lots of time.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE