Web3 IPFS Only Used for Phishing – So Far

Cloud
We discuss the use of the InterPlanetary File System (IPFS) in phishing attacks.
Web3 has been garnering attention recently, but it has yet to be used for anything practical and widespread except for one thing: phishing. The concept of Web 3 encompasses a variety of technologies. In this article, we will ignore the blockchain aspects of Web3 and focus instead on its storage side: specifically, the InterPlanetary File System (IPFS), a peer-to-peer (P2P) object storage system that relies on content addressing instead of location addressing.
Simply put, each file is addressed by a cryptographic hash and a distributed hash table scheme is used to locate a copy of the file. The hash is encapsulated in a so-called content identifier (CID) and immutably identifies that file. We have been observing a rise in the misuse of this technology and will dive into it in greater detail in a future report. In the meantime, let us focus on a specific type of phishing on IPFS.
Normally, IPFS is only available through the P2P network, although to ease the transition for ordinary web users, there are a number of public IPFS gateways that accept a URL with a CID in it and deliver the content of that IPFS file. These gateways usually take the form http[s]://<gateway domain>/ipfs/<CID>.
Research on gateways used for phishing attacks
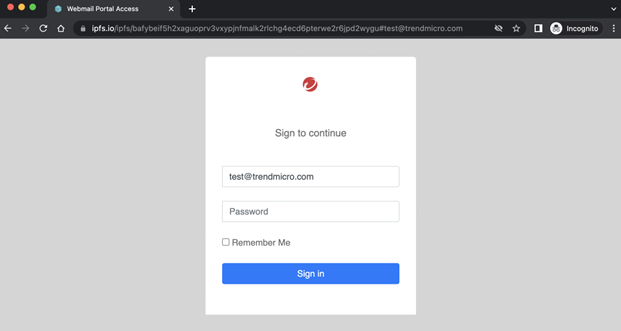
Using Trend Micro’s Web Reputation telemetry data from January 2022 to Nov. 15, 2022, we looked for instances of phishing that used IPFS gateways. Specifically, we looked for IPFS gateway URLs that contained email addresses in the form hxxps[:]//ipfs[.]io/ipfs/<CID>#<EmailAddress>, which is typical of a particular kind of phishing page. For instance, the following phishing page generates a login screen hosted by an IPFS gateway and uses a CID (the string starting with “baf…”). Since it uses the same favicon as that used in the domain of the target’s email address, the phishing page thus appears like the official page of the target organization..
Searching in VirusTotal, we found examples of emails that use IPFS gateways for phishing attacks. For instance, the following email looks like a DocuSign request, but the button displayed points to a gateway hosted by Fleek, a platform that makes creating IPFS websites easy. When the link is accessed, a sign-in page that looks like it comes from Microsoft appears.

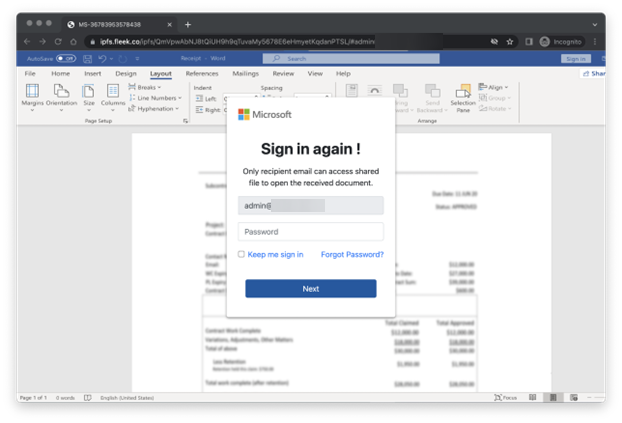
Notably, even if Fleek decided to block such content, it would still be available through any other IPFS gateway.
How big is this problem?
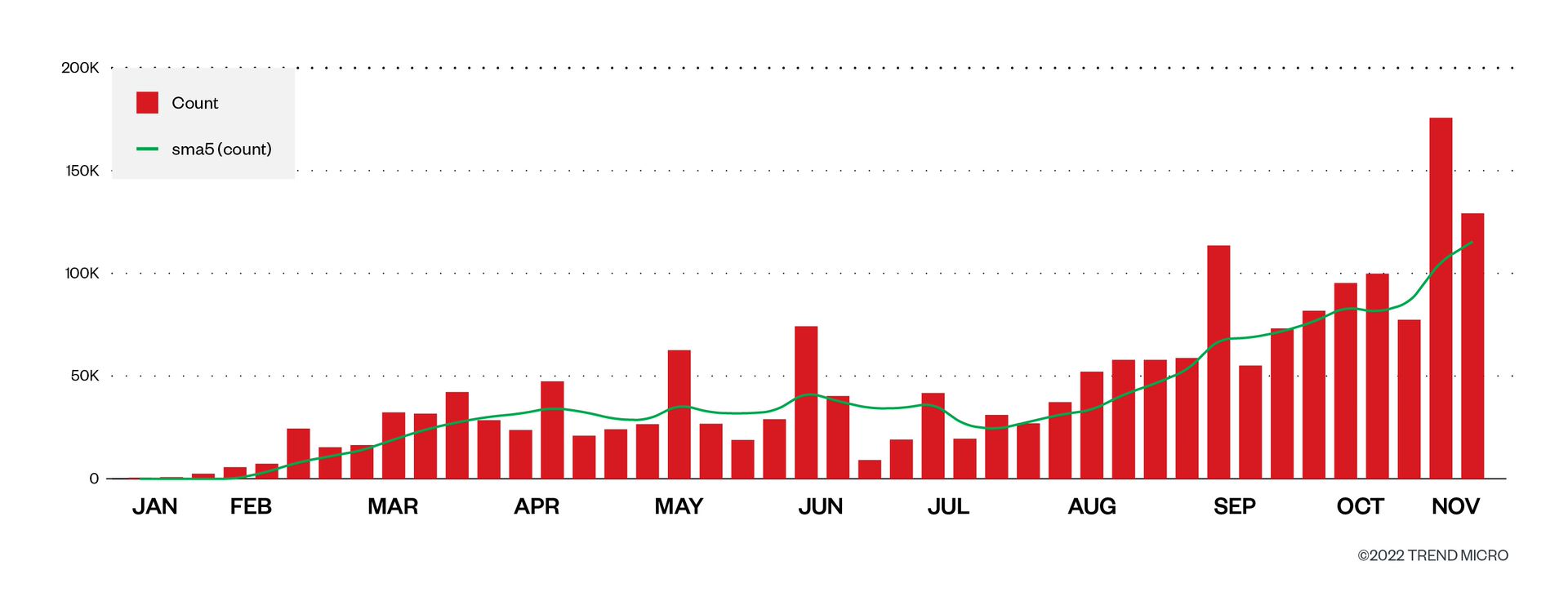
We first observed one IPFS phishing URL being accessed on Jan. 18, 2022. Since then, the attacks have been constantly rising, as the following graph demonstrates. Recently, there was a spike on November 7, when we observed more that more than 70,000 phishing URL were accessed — double the maximum we observed up to that point. This shows us that criminal usage is increasing rapidly.
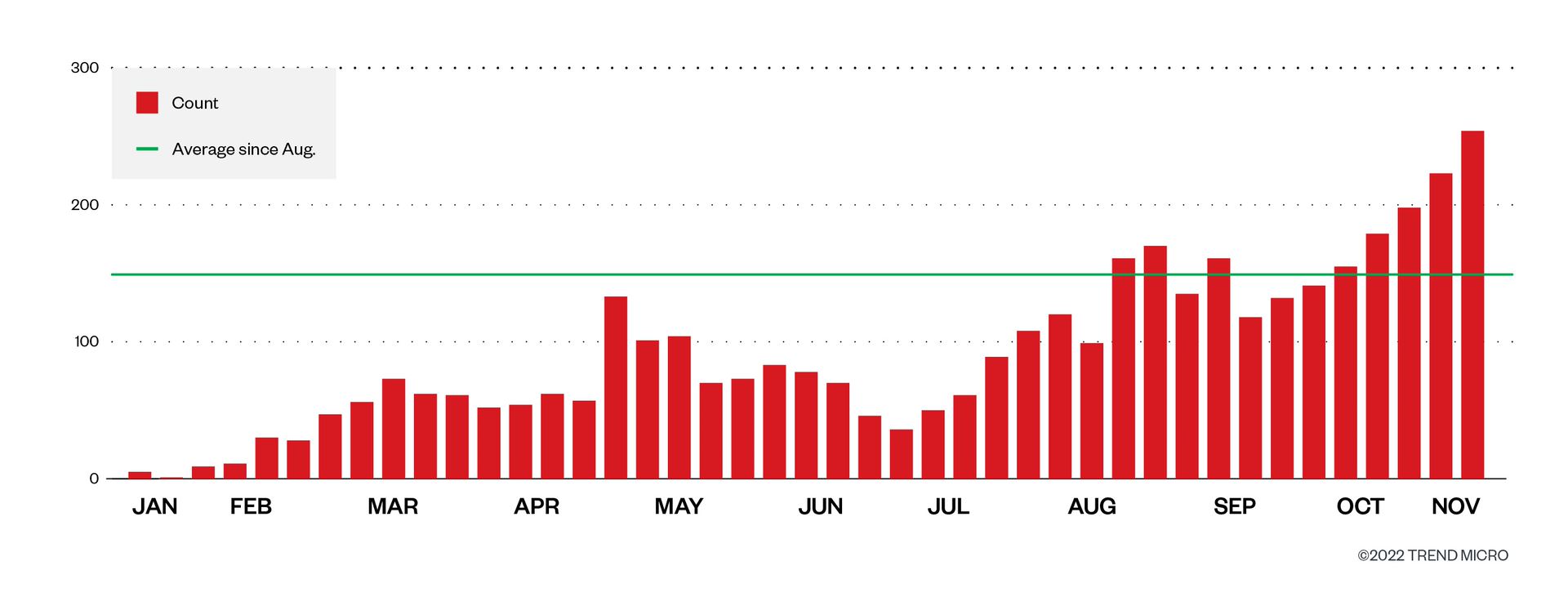
However, not all CIDs found in this sample set were unique. We wanted to know how the growth of unique phishing content was developing, so we removed the duplicate CIDs and found that we could still see a steady rise over the last year. This is perhaps a better estimate of how campaigns using IPFS are developing. So far, we have observed 3,966 unique CIDs and an average of 148 new CIDs per week since August. Since then, we have often observed numbers greater than the average as seen in Figure 4.
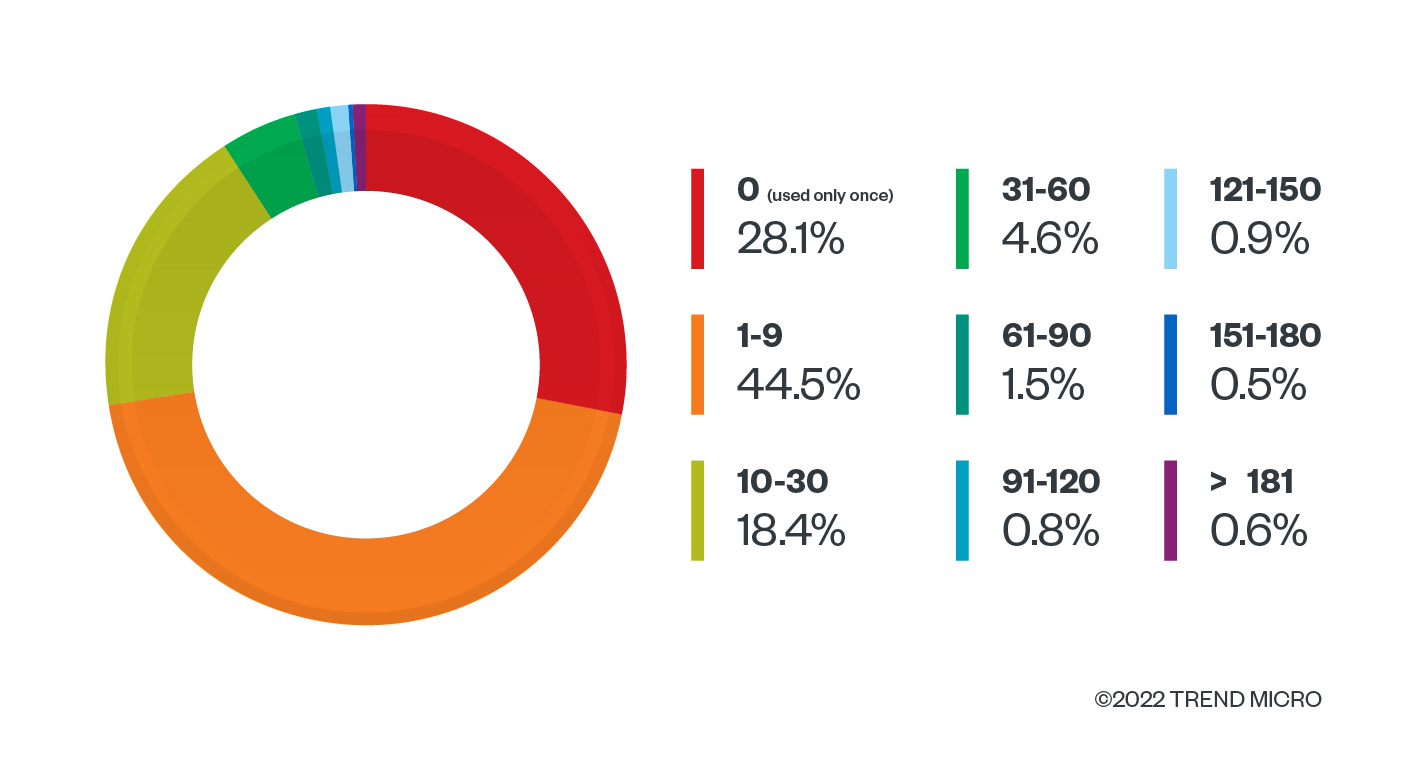
Approximately 28% of the CIDs have been seen only once, and about 72% have been used for less than 10 days. Only 5% have been used for more than a month. This means that while most phishing campaigns move on to new CIDs relatively frequently, there are CIDs that have been in use for longer periods.
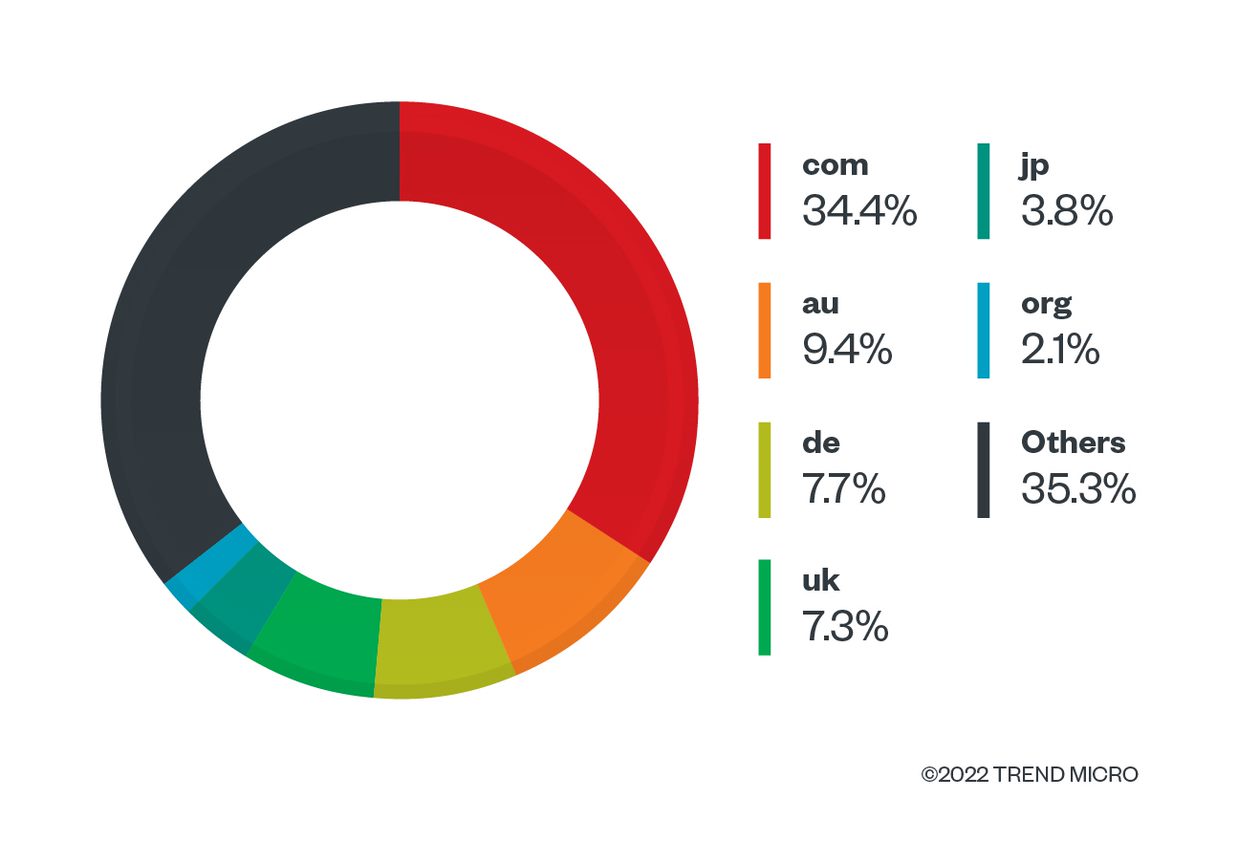
The targeted email addresses are much more diverse, with 455,071 email addresses from 47,734 domains. A closer look at top-level domains shows that “.com” is by far the most popular domain, followed by “.au,” “.de,” “.uk”, and “.jp”.
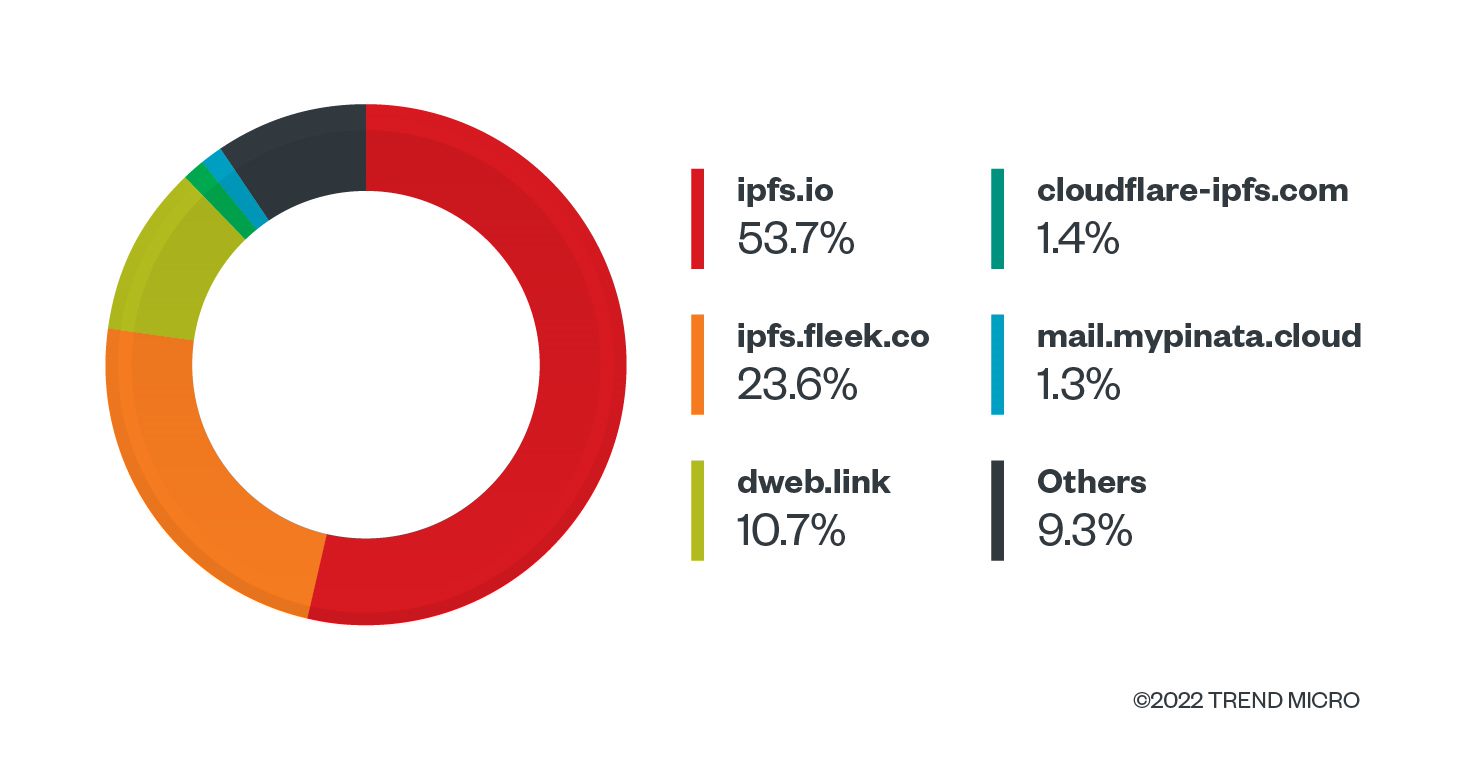
The most common gateways are, unsurprisingly, the official ipfs.io and Fleek’s gateway. Dweb.link is also a prominent gateway provider, probably because it is also mentioned in the official documentation. Since anyone can host a gateway, the long tail of gateways is not insignificant.
The subject lines for phishing are surprisingly diverse. The following table shows the top 10 subject lines according to our telemetry data:
| Rank | Subject (Normalized) |
| 1 | Host-server notification |
| 2 | [WARNING]: The “<EmailAddress>” email account is nearly full |
| 3 | Mail delivery failed: returning message to sender |
| 4 | You have recieved a file via WeTransfer |
| 5 | Password Expiry notice! |
| 6 | (7) Pending incoming messages, Clear Cache for <EmailAddress> to fix Errors. |
| 7 | Password for <EmailAddress> expires soon from Today <Date> <Time> |
| 8 | Mail Account Update |
| 9 | IT support <EmailAddress> |
| 10 | Authentication error in <EmailAddress> on <Date> <Time> |
Table 1. Top 10 subject lines for phishing emails from telemetry data
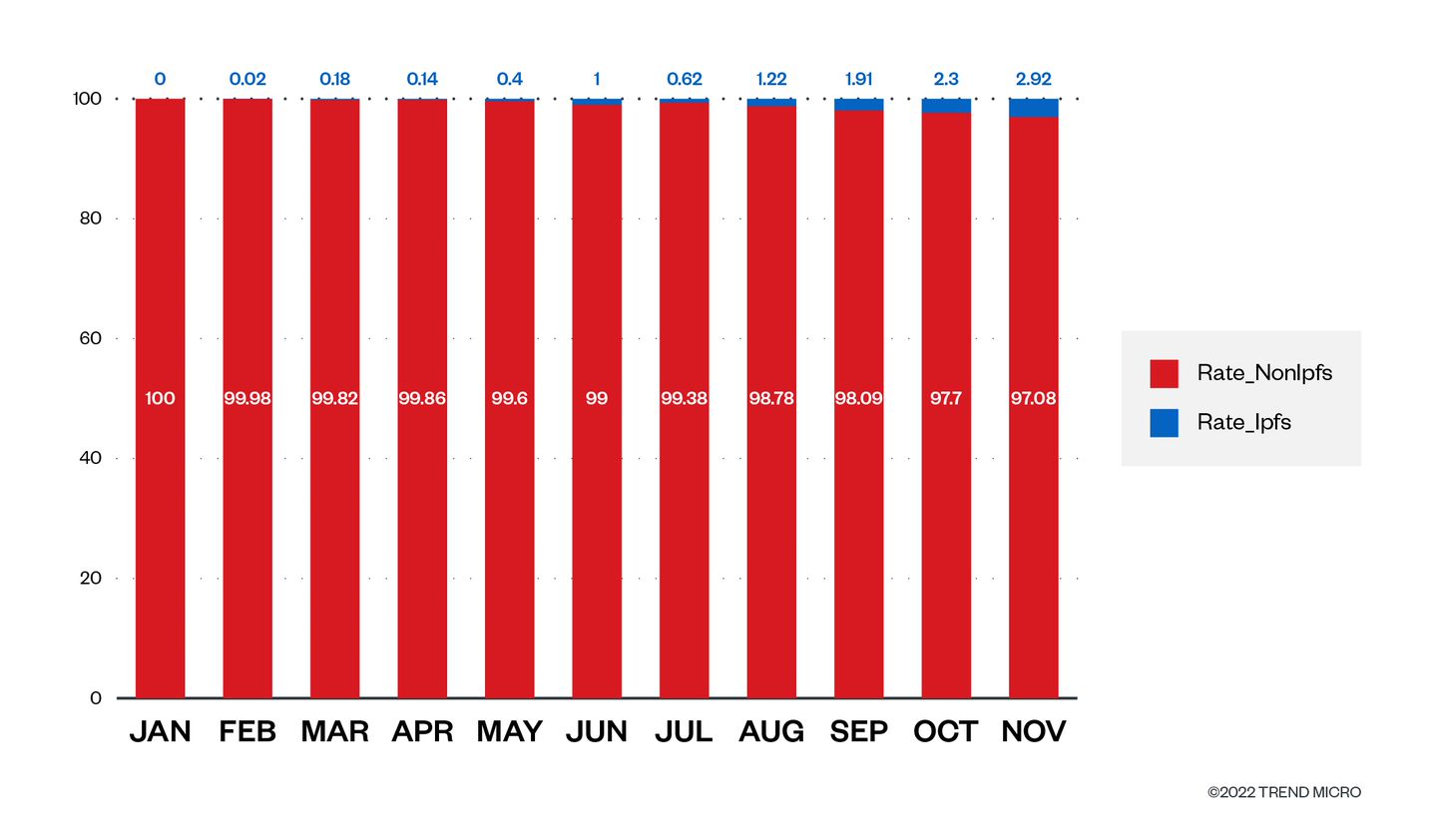
The proportion of IPFS-related phishing among all phishing instances detected by the Trend Micro Web Reputation System (WRS) is very small, but it has been gradually increasing and is expected to continue doing so.
Conclusion
The rise of IPFS-related phishing is concerning because this kind of content cannot be deleted as it is not stored centrally. Since August, we have been seeing a marked rise in phishing URLs that contain email addresses and use IPFS this year. This is likely because this kind of phishing gives attackers an advantage, not to mention that other alternatives have been discontinued. We expect that the exploitation of IPFS will increase further in the future, emphasizing the need for vigilance.
In the meantime, blocking all gateways individually might not be feasible, as NFTs also often use IPFS. Blocking CIDs by URL patterns is more realistic, but this has its own limitations. However, the entire ecosystem of IPFS is already much bigger than just IPFS and is constantly evolving; this calls for a complete report that we will publish soon. At present, however, phishing unfortunately seems to be the main use-case for IPFS.
Indicators of Compromise (IOCs)
The email sample is from VirusTotal:
- 570ab44831e863671b06f3ec8e489715ca5a346daae09c3c00ec4b4db34292fb
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE