What is Nmap? Why you need this network mapper
Network administrators, IT managers and security professionals face a never-ending battle, constantly checking on what exactly is running on their networks and the vulnerabilities that lurk within. While there is a wealth of monitoring utilities available for network mapping and security auditing, nothing beats Nmap’s combination of versatility and usability, making it the widely acknowledged de facto standard.
What is Nmap?
Nmap, short for Network Mapper, is a free, open-source tool for vulnerability scanning and network discovery. Network administrators use Nmap to identify what devices are running on their systems, discovering hosts that are available and the services they offer, finding open ports and detecting security risks.
Nmap can be used to monitor single hosts as well as vast networks that encompass hundreds of thousands of devices and multitudes of subnets.
Though Nmap has evolved over the years and is extremely flexible, at heart it’s a port-scan tool, gathering information by sending raw packets to system ports. It listens for responses and determines whether ports are open, closed or filtered in some way by, for example, a firewall. Other terms used for port scanning include port discovery or enumeration.
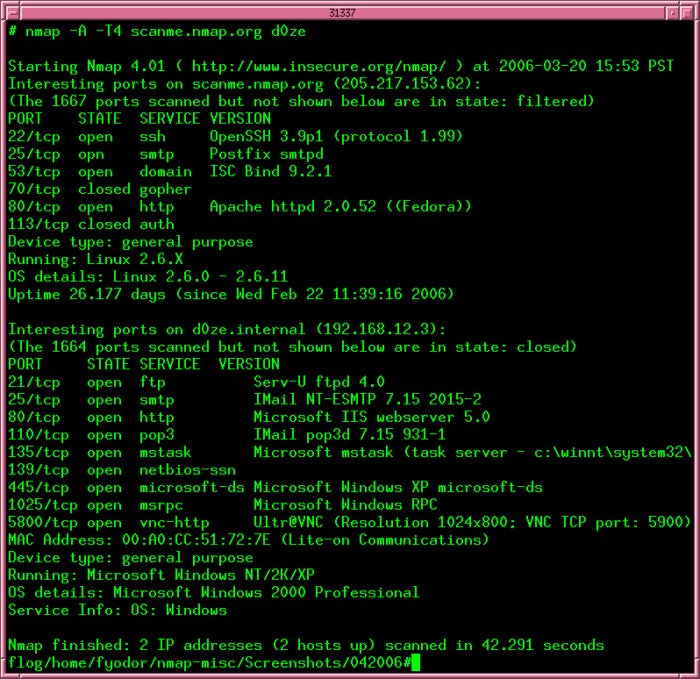 Nmap.org
Nmap.org
Since its release in 1997, Nmap has evolved but the basis of its functionality is still port scanning.
Nmap port scan
The packets that Nmap sends out return with IP addresses and a wealth of other data, allowing you to identify all sorts of network attributes, giving you a profile or map of the network and allowing you to create a hardware and software inventory.
Different protocols use different types of packet structures. Nmap employs transport layer protocols including TCP (Transmission Control Protocol), UDP (User Datagram Protocol), and SCTP (Stream Control Transmission Protocol), as well as supporting protocols like ICMP (Internet Control Message Protocol), used to send error messages.
The various protocols serve different purposes and system ports. For example, the low resource overhead of UDP is suited for real-time streaming video, where you sacrifice some lost packets in return for speed, while non-real time streaming videos in YouTube are buffered and use the slower, albeit more reliable TCP.
Along with its many other features, Nmap fundamental port scanning and packet-capture capabilities are constantly being enhanced.
“Right now we are very focused on our Npcap packet capturing driver and library for Windows,” noted Nmap author Gordon Lyon in an email response to queries about the software. “It makes Nmap faster and more powerful on Windows and is now used by many other applications as well. We have done eight releases of Npcap this year.”
Nmap’s journey to cult status and networking stardom
Nmap was written in C++ and first introduced, with source code, in Phrack Magazine in September 1997. It’s been extended with C, Perl and Python. Creator Gordon Lyon had adopted the pseudonym Fyodor Vaskovitch, which he picked up after reading Fyodor Dostoevsky’s Notes from Underground, and still uses the handle Fyodor in his work on Nmap.
 Urbane Security
Urbane Security
Nmap creator Gordon Lyon (AKA Fyodor) at Def Con 26 in Las Vegas.
Over the years, Nmap has benefited from the contributions of a growing community of aficionados and developers, and it’s now downloaded thousands of times a day. Along the way it has achieved a degree of fame in popular culture, becoming the go-to hacking tool featured by directors in at least a dozen movies in scenes with stars like Rihanna and Kate Mara. Its first break in big-time films came in The Matrix Reloaded, where the Trinity character played by Carrie-Anne Moss showed off her hacking chops and impressed techie admirers by correctly using the software. (You can see her, and it, in action in a clip on YouTube.)
What OSes does Nmap run on?
One reason for Nmap’s popularity is that it can be used on a variety of different operating systems. It runs on Windows and macOS and supports Linux distributions including Red Hat, Mandrake, SUSE and Fedora. It also runs on other OSes including BSD, Solaris, AIX and AmigaOS.
How to use Nmap
There is a wide range of free network monitoring utilities as well as free open-source vulnerability scanners available to network administrators and security auditors. What makes Nmap stand out as the tool IT and network managers need to know is its flexibility and power. While the basis of Nmap’s functionality is port scanning, it allows for a variety of related capabilities including:
- Network mapping: Nmap can identify the devices on a network (also called host discovery), including servers, routers and switches, and how they’re physically connected.
- OS detection: Nmap can detect the operating systems running on network devices (also called OS fingerprinting), providing the vendor name, the underlying operating system, the version of the software and even an estimate of devices’ uptime.
- Service discovery: Nmap can not only identify hosts on the network, but whether they’re acting as mail, web or name servers, and the particular applications and versions of the related software they’re running.
- Security auditing: Figuring out what versions of operating systems and applications are running on network hosts lets network managers determine their vulnerability to specific flaws. If a network admin receives an alert about a vulnerability in a particular version of an application, for example, she can scan her network to identify whether that software version is running on the network and take steps to patch or update the relevant hosts. Scripts can also automate tasks such as detecting specific vulnerabilities.
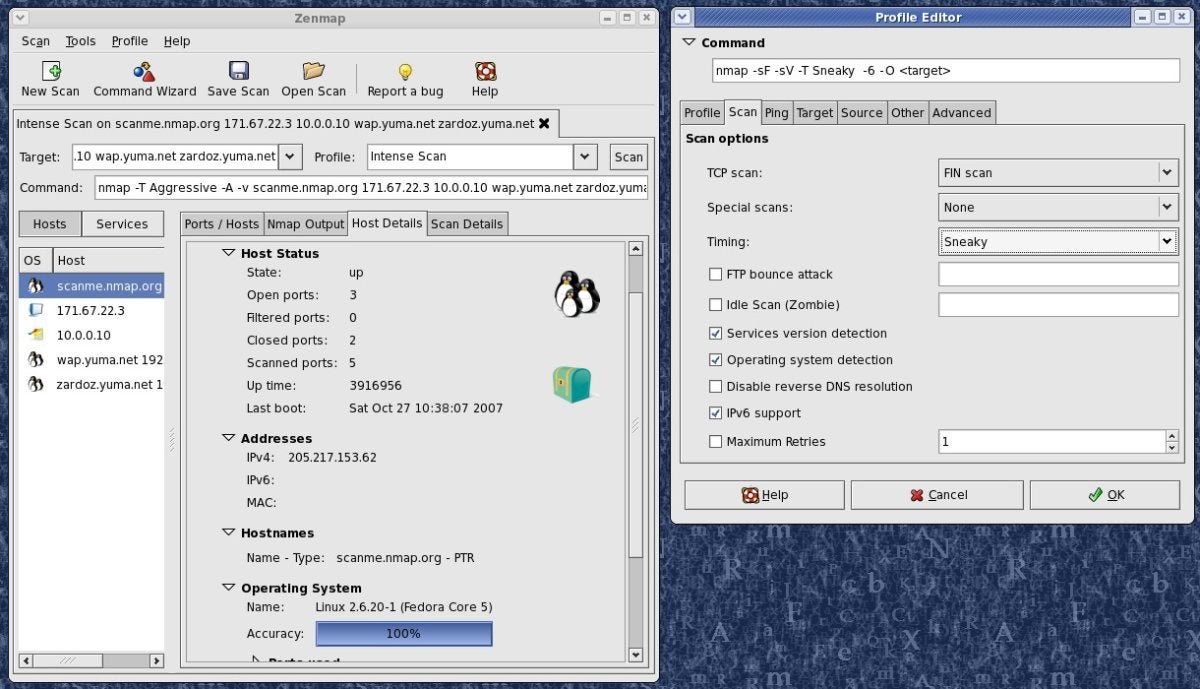 NMap.org
NMap.org
Zenmap is the graphical user interface for Nmap.
Nmap commands for beginners and pros
One of the beauties of Nmap is that beginners with little system or network knowledge can get started with simple commands for basic scanning, while professionals can take advantage of more complex sorts of probes, which result in more fine-grained view of a network.
What you get when you use Nmap is essentially a list of the targets you’ve scanned, along with information associated with those targets. The information you receive depends on the sort of scan you do – in other words, the commands you’ve used.
Depending on the command, scans don’t necessarily generate a lot of traffic and don’t have to be very intrusive. Scanning all ports on all systems would be inefficient, primarily since only a fraction of available ports are going to be in use at any one time (a system can have 65,535 TCP ports and 65,535 UDP ports). Different options allow for finetuning or expanding scans. In service version detection for example, available options include:
- sV (enables version detection)
- version-intensity <intensity> (sets scan intensity)
Intensity ranges between 0 and 9, and establishes the sort of probes that you want to apply. A lower-number intensity scan will probe for common services, while a higher-number intensity scan can identify lesser-used services correctly but takes longer.
Different commands can also, for example, let you specify which ports or subnets to scan or skip.
The Nmap Scripting Engine (NSE)
Nmap includes a scripting engine using the Lua programming language to write, save and share scripts that automate different sorts of scans. Though they are frequently used to check for well-known network infrastructure vulnerabilities, all sorts of tasks can be automated.
Zenmap, the Nmap GUI
Zenmap is the Nmap security scanner graphical user interface and provides for hundreds of options. It lets users do things like save scans and compare them, view network topology maps, view displays of ports running on a host or all hosts on a network, and store scans in a searchable database.
What’s new in Nmap
Nmap 7.70, released in March, offered nine new NSE scripts and provided hundreds of new OS and service fingerprints for operating system and application version detection, including fingerprints for IPv6 and IPv4 OS support. Version 7.70 enhancements also make service-version detection faster and more accurate. Because of the widespread use of Windows, improvements to the Npcap Windows packet-capturing library intended to enhance performance and stability are particularly important.
The next release is expected late third quarter or early fourth quarter, but Lyon notes that between releases, new scripts and protocols are being polished up and available for testing.
“Moving from the obsolete, unmaintained Winpcap driver to our new Npcap system really is a huge step forward for Windows Nmap users,” Lyon said. “We also continue to expand and improve the Nmap Scripting Engine. We now have 591 scripts and 133 protocol libraries, as documented at https://nmap.org/nsedoc/. I feel like Nmap is truly reaching adulthood. In fact it turns 21 on September 1st!”
Is Nmap used illegally?
While port scanning per se is not illegal, at least under U.S. federal law, Nmap’s features are certainly useful to malicious hackers probing for vulnerabilities to exploit. Certain uses of the software, especially without permission, can get you fired or in legal trouble, even if you’re doing a vulnerability scan for benign purposes.
While some Nmap scans are fairly light touch and may not set off alerts, it’s always best to get your scans approved with the appropriate people in your organization. Be aware that many Nmap options, such as OS fingerprinting, require root privilege. When in doubt about the legality of what you want to do, especially when you are working alone and don’t have an organization’s legal team to consult, speak to a lawyer with expertise in computer fraud and abuse.
Nmap resources
If want to get deeper in Nmap, the best single source for information is Nmap.org, maintained by Fyodor himself. Essential resources on Nmap.org and other sites include:
Where to download Nmap
To download Nmap, go here and follow the instructions.
READ MORE HERE