What Worries CISOs Most In 2019

We recently held a valuable conversation (and a great dinner) with about a dozen senior IT security leaders in Atlanta, Georgia. I was fortunate to attend and discuss what plagues them most.
Here are some of their concerns.
Many face considerable change in their business environments – one third of the companies called out the high pace of acquisitions as a source of risk.
Acquisitions draw down information security resources disproportionately. First, IT security must participate in the due diligence phase, prior to the actual acquisition. Under significant time pressure, and strictly bound by the terms of the governing NDA, the InfoSec team must verify the integrity of the target environment’s IT infrastructure. It must render a judgment on the trustworthiness of the underlying procedures, the competence of the support team, the appropriateness of funding and staffing, the effectiveness of policy and awareness training, the fitness of the security technology judged against the changing mission of the target firm, and the accessibility of crucial information. In regulated industries, the acquirer has to review past certifications, audit findings and recommendations, and earlier security events, including how they were handled, and how the organization effectively integrated lessons learned into its updated way of doing business. Some of the attendees reported an acquisition every six weeks over the past two years or more. This pace requires efficient process maturity and open communication among the team members, and ample trust.
Some CIOs reported the challenge of balancing the executive team’s need to know with the managerial desire to optimize team focus on critical initiatives. In the Boardroom and among the C-suite, IT remains a hot topic and IT security is a known vulnerability. This leads some organizations toward micromanaging the IT security team. As we all know, this inappropriate focus has two costs: first, it distracts the Board and the C-suite from their primary missions. Second, it distracts the people doing the job from their task. One effective tactic some adopted is the weekly – or even daily – newsletter. This document provides the status for ongoing projects, notes about top performers, assessment of newly discovered vulnerabilities, and pointers towards effective risk mitigation the leadership team can bring to their respective operational areas. When a Board member has a question for the team, the CISO can intercept it and post a response through the newsletter.
Many CISOs discussed their challenges with BYOD policies. Some mentioned concerns with GDPR impeding their ability to wipe corporate applications and information from employee-owned devices. It’s unclear how to balance that business requirement with privacy concerns for smart phones. With laptops, one approach is to limit corporate access through a locked-down virtual desktop image accessed through a secure VPN. An evil-minded employee could take a picture of the screen, but that attack works on a corporate laptop just as well.
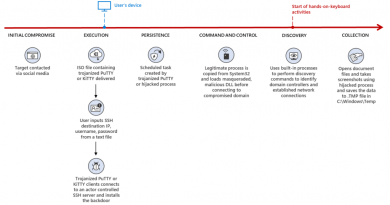
BEC remains a concern, along with phishing attacks leading to possible ransomware infections. One approach is to ignore emails from new domains – those that are less than two months old. This would exclude email from nearly all attackers; anyone legitimately trying to reach an employee will try again in time.
The meeting was quite open and convivial. It was an honor to participate in the discussion, and I look forward to similar meetings in the future. My thanks to the participants!
What do you think? Let me know in the comments below, or message me @WilliamMalikTM!
Read More HERE