White House Report Dishes Deet On All 11 Major Government Breaches From 2023
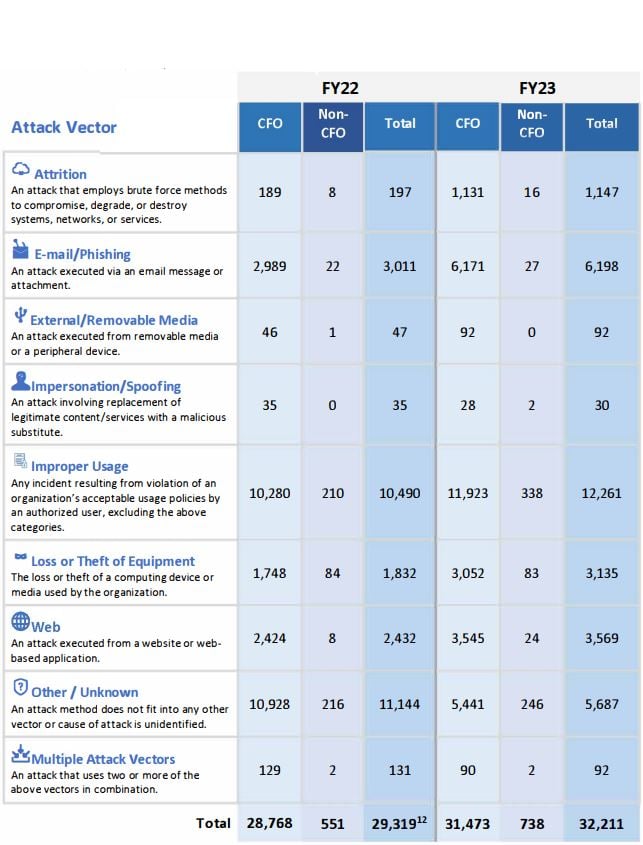
The number of cybersecurity incidents reported by US federal agencies rose 9.9 percent year-on-year (YoY) in 2023 to a total of 32,211, per a new White House report, which also spilled the details on the most serious incidents suffered across the government.
Of the total number of incidents, the majority (38 percent) were classed as “improper usage,” meaning a system was used in a way that violated the agency’s acceptable use policies. The report stated that agencies have the capability to detect when security policies are being violated, but not the ability to prevent it from actually happening.
The next most common incident was caused by, unsurprisingly, phishing and malicious emails, and it was the vector that saw the biggest YoY increase (by number of incidents) from 3,011 in 2022 to 6,198 in 2023.
5,687 incidents couldn’t be categorized by any specific vector, so they were ambiguously lumped under “other/unknown.” Web-based attacks barely increased YoY with 3,569 cases, unlike incidents of equipment going awry – either through carelessness or actual theft.
The report [PDF] doesn’t break down the total into loss or theft, which would have been interesting, but the number of yearly cases rose from 1,832 to 3,135 in 2023.
Brute force attacks on networks and services were the only other vector to register more than 1,000 cases (1,147) – but took the price for the biggest YoY percentage increase in incidents, up from just 197 the year before.
But, despite the annual increase in attacks, none registered higher than “medium” on the National Cyber Incident Scoring System (NCISS), which acts like the CVSS for individual vulnerabilities and grades incidents according to how impactful they’re likely to be on aspects of society such as national and economic security, delivering public services, and foreign relations.
The vast majority (31,621) fell into the baseline category, meaning “highly unlikely” to affect society. Only 348 fell into “low” – “unlikely” to affect society, while 31 were categorized as “medium” – incidents that “may affect” society. 229 cases didn’t include sufficient information to categorize them.
The juiciest cases
Separately to the grading of incidents’ impactfulness on the US are “major incidents”, of which there were 11 reported across federal agencies in 2023 and multiple reports from the Health and Human Services, Justice, and Treasury departments.
According to M-23-03, a major incident is defined as such if it meets one of two descriptions, taken verbatim from the memorandum [PDF]:
-
Any incident that is likely to result in demonstrable harm to the national security interests, foreign relations, or the economy of the United States, or to the public confidence, civil liberties, or public health and safety of the American people
-
A breach that involves personally identifiable information (PII) that, if exfiltrated, modified, deleted, or otherwise compromised, is likely to result in demonstrable harm to the national security interests, foreign relations, or the economy of the United States, or to the public confidence, civil liberties, or public health and safety of the American people
HHS
Two of the 11 major incidents in 2023 came from the Department of Health and Human Services (HHS). The first was described in the report as a ransomware attack on a system owned and operated by a contractor supporting the department’s Centers for Medicare and Medicaid Services.
The attack specifically targeted network file shares and led to the exposure of personal data concerning 2.8 million people, around half of which were deceased at the time. Names, addresses, dates of birth, Medicare identifiers, and bank details were involved.
At first, this sounded a little like it could have been the MOVEit incident at Maximus, which handles admin services for Medicare and Medicaid, but that case affected 8-11 million people rather than just 2.8 million and didn’t actually involve the deployment of ransomware.
The HHS’s other major incident was again the fault of contractors, two of them which were targeted by attackers using a zero-day to gain access to systems hosting personal data. It’s believed that 1.88 million people’s data may have been compromised, including all the usual data types as well as, in some cases, social security numbers and medical diagnoses.
Treasury
The Treasury Department also clocked in two major incidents in 2023, and the first one could be argued as two separate incidents given that it involved the disclosure of the same data set twice.
Announced by the Internal Revenue Service (IRS) in September 2022, the incident saw 990-T forms, containing names, addresses, email addresses, and phone numbers, made available for download by members of the public.
A coding error made this possible and even though the data was promptly deleted from the public web server, the vendor responsible didn’t delete the data from a staging server, which inadvertently saw it published a second time.
The second incident involved an employee at the department’s Office for the Inspector General (OIG) unwittingly handing their login credentials after being phished by an overseas state-sponsored attacker, country withheld.
Their account was taken over for roughly 15 hours and could have accessed all manner of files, but they were booted out before any lateral movement or malware could be introduced to the equation.
Justice
The Justice Department was the target of two successful ransomware attacks in fiscal year 2023, the first of which targeted a United States Marshals Service’s (USMS) computer and exposed the personal data of USMS personnel, but otherwise had limited impact given the quick response.
Not a great deal was offered in terms of detail about the second case, which hit a vendor supplying data analytics support for cases. It led to the compromise of personal and medical data, and everyone affected was offered the requisite credit monitoring services.
Interior
There was just one major case at the Interior Department, and it was a total accident. The report tells the story of an authorized developer who modified a security policy of a payroll system that mistakenly allowed HR personnel to view the records of 36 federal agency customers.
It’s thought that around 147,000 people’s personal data was potentially exposed as a result, and the Interior Business Center, which operated the affected system, also failed to Carry out a privacy impact assessment following the architecture changes that led to the incident. It strengthened internal processes and training in the aftermath.
Consumer Financial Protection Bureau
A rogue now-former employee was to blame for the breach at CFPB after they sent 14 emails and two spreadsheets packed with personal data belonging to around 256,000 consumers linked to a single financial institution.
The CFPB demanded the naughty worker delete the emails and provide proof of that deletion – demands that were ignored. The official assessment was that the data included in those emails couldn’t be used to access a person’s account or carry out identity theft, but some affected individuals were notified anyway.
Transportation
Around 237,000 individuals were potentially affected after several administration systems were breached and personal data stolen from the Parking and Transit Benefit System (PTBS), which supports the TRANServe initiative.
The attackers gained access by exploiting an unpatched critical vulnerability in an unnamed
“commercial web-application development platform” and lifted details such as names, home and work addresses, and the last four digits of social security numbers.
Office of Personnel Management
Although MOVEit isn’t explicitly named here, Cl0p was almost certainly responsible for the OPM’s only major incident in FY23. An OPM contractor was using MOVEit MFT to support te admin behind the Federal Employee Viewpoint Survey. What followed was the unauthorized access of data belonging to circa 632,000 employees at the Justice and Defense departments.
Energy
Again, this was almost certainly another MOVEit-related incident affecting the Department of Energy’s Waste Isolation Pilot Plant and the Oak Ridge Associated Universities. 34,000 former Energy Department workers, covered by a program to support those who may have been exposed to dangerous substances like nuclear waste, had their personal and health data exposed.
Around 66,000 individuals from the Office of Science were also affected, with names, dates of birth, full or partial SSNs, passport details, and nationalities compromised. ®
READ MORE HERE
