Why operational resilience will be key in 2021, and how this impacts cybersecurity

The lessons we have learned during the past 12 months have demonstrated that the ability to respond to and bounce back from adversity in general, can impact the short-and long-term success of any organization. It can even dictate the leaders and laggards in any industry.
When we take into consideration that as security threats also become more daunting, with many organizations remaining in a remote work environment, global organizations must reach a state where their core operations and services are not disrupted by unexpected changes.
The key to success in surviving any unforeseen circumstances in 2021, will be operational resiliency. Operational resilience is the ability to sustain business operations during any major event, including a cyberattack. It requires a strategic and holistic view of what could go wrong and how an organization will respond. Consider the risk and response for a utility company, for example, an organization that relies on IoT data, or a manufacturer of medical supplies. While their approach may differ, the impact would be equally as devastating should their operational continuity be halted. In today’s digital world, preparing for cyber threats must be a strategic part of that plan just like any other form of continuity and disaster recovery.
Speaking with customers globally, we know they are not fully prepared to withstand a major cyber event. Whilst many firms have a disaster recovery plan on paper, nearly a quarter have never tested that plan and only 42 percent of global executives are confident their organization could recover from a major cyber event without it affecting their business.
It begins with Zero Trust. Zero Trust is based on three principles, verify explicitly, use least privilege access, and assume breach.
Verify explicitly
Rather than trust users or devices implicitly because they’re on the corporate network or VPN’ed into it, it is critical to assume zero trust and verify each transaction explicitly. This means enabling strong authentication and authorization based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
This starts with strong user authentication. Multi-factor authentication (MFA) is essential, but it’s time to move away from passwords plus SMS and voice calls as authentication factors. Bad actors are getting more sophisticated all the time, and they have found a number of ways to exploit the publicly switched telephone networks (PSTN) that SMS and voice calls use as well as some social engineering methods for getting these codes from users.
For most users on their mobile devices, we believe the right answer is passwordless with app-based authentication, like Microsoft Authenticator, or a hardware key combined with biometrics.
Least privileged access
Least privileged access means that when we do grant access, we grant the minimum level of access the user needs to complete their task, and only for the amount of time they need it. Think about it this way, you can let someone into your building, but only during work hours, and you don’t let them into every lab and office.
Identity Governance allows you to balance your organization’s need for security and employee productivity with the right processes and visibility. It provides you with the capabilities to ensure that the right people have the right access to the right resources.
Assume breach
Finally, operate with the expectation of a breach, and apply techniques such as micro-segmentation and real-time analytics to detect attacks more quickly.
In a Zero Trust model, identities—whether they represent people, services, or IoT devices—define the control plane in which access decisions are made. Digital identities, such as transport layer security (TLS) and code signing certificates, SSH keys, secrets, and other cryptographic assets are critical to authentication, signing, and encryption.
That’s why having a strong identity is the critical first step to the success of a Zero Trust security approach.
Embracing Zero Trust allows organizations to harden their defenses while providing employees access to critical data, even during a cyber event. That’s because identity is the foundation of any Zero Trust security strategy because it automatically blocks attacks through adaptive security policies; across users and the accounts, devices, apps, and networks they are using. Identity is the only system that connects all security solutions together so we have end-to-end visibility to prevent, detect, and respond to distributed and sophisticated attacks thanks to cloud technology.
In a Zero Trust model, identities—whether they represent people, services, or IoT devices—define the control plane in which access decisions are made. Digital identities, such as TLS and code signing certificates, SSH keys, secrets, and other cryptographic assets are critical to authentication, signing, and encryption.
“Human identities” such as passwords, biometrics, and other MFA are critical to identifying and authenticate humans. Being a Zero Trust organization also means pervasive use of multi-factor authentication—which we know prevents 99 percent of credential theft and other intelligent authentication methods that make accessing apps easier and more secure than traditional passwords.
Identity is both the foundation for Zero Trust and acts as a catalyst for digital transformation. It automatically blocks attacks through adaptive security policies. It lets people work whenever and wherever they want, using their favorite devices and applications.
That’s because Zero Trust security relies heavily on pervasive threat signals and insights. It is essential to connect the dots and provide greater visibility to prevent, detect and respond to distributed and sophisticated attacks.
Future-proofing your security posture
As security threats become more daunting and many organizations remain in a remote work environment, global organizations must reach a state where their core operations and services will not be disrupted by unexpected global changes.
To maintain operational resilience, organizations should be regularly evaluating their risk threshold. When we talk about risk, this should include an evaluation of an organization’s ability to effectively respond to changes in the crypto landscape, such as a CA compromise, algorithm deprecation, or quantum threats on the horizon.
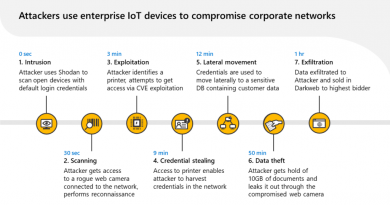
Bottom line: organizations must have the ability to operationally execute the processes through a combination of human efforts and technology products and services. The ability to do something as simple as restoring from recent backups will be tested in every ransomware attack, and many organizations will fail this test—not because they are not backing up their systems, but because they haven’t tested the quality of their backup procedures or practiced for a cyber event.
Operational resilience guidelines call for demonstrating that concrete measures are in place to deliver resilient services and that both incident management and contingency plans have been tested. Our new normal means that risks are no longer limited to commonly recognized sources such as cybercriminals, malware, or even targeted attacks. Operational resilience is the necessary framework we must have in place in order to maintain business continuity during any unforeseen circumstances in the year ahead.
We want to help empower every organization on the planet by continuing to share our learnings to help you reach the state where core operations and services won’t be disrupted by geopolitical or socioeconomic events, natural disasters, or even cyber events.
To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE