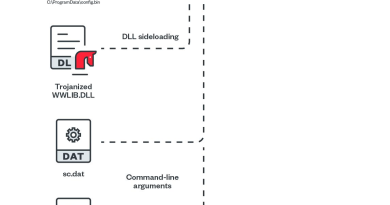
ZDI-CAN-25373: Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns

During our analysis, we discovered that some North Korean threat actors, such as Earth Manticore (APT37) and Earth Imp (Konni), tended to use extremely large .lnk files with large amounts of whitespace and other junk content to further evade detection. Earth Imp used files with a median size of 3.32MB, with a maximum file size of 70.1MB. Earth Manticore used files with a median size of 33.33MB, with a maximum file size of 55.16MB.
ZDI-CAN-25373 is an example of (User Interface (UI) Misrepresentation of Critical Information (CWE-451). This means that the Windows UI failed to present the user with critical information. Similar to a previous discovery we made, it is a failure to properly represent security-critical information to the user. By exploiting ZDI-CAN-25373, the threat actor can prevent the end user from viewing critical information (commands being executed) related to evaluating the risk level of the file.
Conclusion
The threat posed by APTs originating from nation-states, as well as from sophisticated cybercriminals, poses a significant risk to the confidentiality, integrity, and availability of data maintained by governments, critical infrastructure, and private organizations globally. Among the 11 state-sponsored APT groups leveraging ZDI-CAN-25373, a majority have a documented history of exploiting zero-day vulnerabilities in attacks in the wild. These vulnerabilities present substantial risks, as they target flaws that remain unknown to software vendors and lack corresponding security patches, thereby leaving governments and organizations vulnerable to exploitation. As geopolitical tensions and conflicts escalate, an increase in the sophistication of threat actors and the utilization of zero-day vulnerabilities is anticipated to rise, as both nation-states and cybercriminals endeavor to gain a competitive advantage over their adversaries. This growing prevalence of zero-day exploitation necessitates the implementation of comprehensive security solutions to safeguard critical assets and industries effectively. This vulnerability was disclosed to Microsoft via Trend ZDI’s bug bounty program; Microsoft classified this as low severity and this will not be patched in the immediate future.
To make software more secure and protect customers from zero-day attacks, Trend ZDI works with security researchers and vendors to patch and responsibly disclose software vulnerabilities before APT groups can deploy them in attacks. The Trend ZDI threat hunting team also proactively hunts for zero-day attacks in the wild to safeguard the industry.
Proactive security with Trend Vision One™
Organizations can protect themselves from attacks such as those employed by APT groups with Trend Vision One™ – the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry’s first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
When faced with uncertain intrusions, behaviors, and routines, organizations should assume that their system is already compromised or breached and work to immediately isolate affected data or toolchains. With a broader perspective and rapid response, organizations can address breaches and protect its remaining systems, especially with robust Endpoint and Network Security solutions. The platform’s security operations capabilities stop adversaries with unrivalled visibility—enriched by native sensors and third-party telemetry. Detect, investigate, and respond proactively with the power of XDR, SIEM, and SOAR. Leaving attackers with no place left to hide.
Trend rules and filters for ZDI-CAN-25373
The following protections have been available to Trend Micro customers:
Trend Vision One™ – Network Security
- 44844 – ZDI-CAN-25373: Zero Day Initiative Vulnerability (Microsoft Windows)
Trend Vision One™ – Endpoint Security, Trend Micro™ Deep Security™, Trend Vision One Network Sensor and Trend Micro Deep Discovery Inspector (DDI)
- 5351 – ZDI-CAN-25373 MICROSOFT WINDOWS ZERO DAY VULNERABILITY – HTTP(RESPONSE)
- 1012182 - Microsoft Windows Zero Day Vulnerability Over HTTP (ZDI-CAN-25373)
- 1012183 - Microsoft Windows Zero Day Vulnerability Over SMB (ZDI-CAN-25373)
More Trend rules and filters can be found here.
Trend Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Vision One customers can access a range of Intelligence Reports and Threat Insights. Threat Insights helps customers stay ahead of cyber threats before they happen and allows them to prepare for emerging threats by offering comprehensive information on threat actors, their malicious activities, and their techniques. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and effectively respond to threats.
Trend Vision One Threat Insights App
- Threat Actors: Water Glashtyn, Earth Iktomi, Water Poukai, Water Cetus, Earth Balayang, Fire Tengu, Earth Imp, Water Asena, Earth Akurra, Earth GelertEarth Iktomi, Water Poukai, Water Cetus, Earth Balayang, Fire Tengu, Earth Imp, Water Asena, Earth Akurra, Earth Anansi, Earth Gelert, Earth Vetala, Earth Kapre, Earth Preta, Earth Tengshe, Earth Lusca
- Emerging Threats: ZDI-CAN-25373: Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Detect suspicious cmd.exe or powershell.exe execution from LNK files
eventSubId:2 AND (processFilePath:\”*\\cmd.exe\” OR processFilePath:\”*\\powershell.exe\”) AND parentFilePath:\”*.lnk\”
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Yara Threat Hunting Rule
Use this YARA rule to find files exploiting ZDI-CAN-25373:
rule ZTH_LNK_EXPLOIT_A
{
meta:
author = “Peter Girnus”
description = “This YARA file detects padded LNK files designed to exploit ZDI-CAN-25373.”
reference = “<LINK_TO_BLOG>”
target_entity = “file”
strings:
$magic = {4C 00 00 00 01 14 02 00}
$spoof_a = {20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00 20 00}
$spoof_b = {09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00 09 00}
$spoof_c = {0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00 0A 00}
$spoof_d = {0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00 0D 00}
$spoof_e = {11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00 11 00}
$spoof_f = {12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00 12 00}
$spoof_g = {13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00 13 00}
$spoof_h = {0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00 0D 00 0A 00}
condition:
$magic at 0x00 and ($spoof_a or $spoof_b or $spoof_c or $spoof_d or $spoof_e or $spoof_f or $spoof_g or $spoof_h)
}
Indicators of compromise
The indicators of compromise for this entry can be found here.
Read More HERE